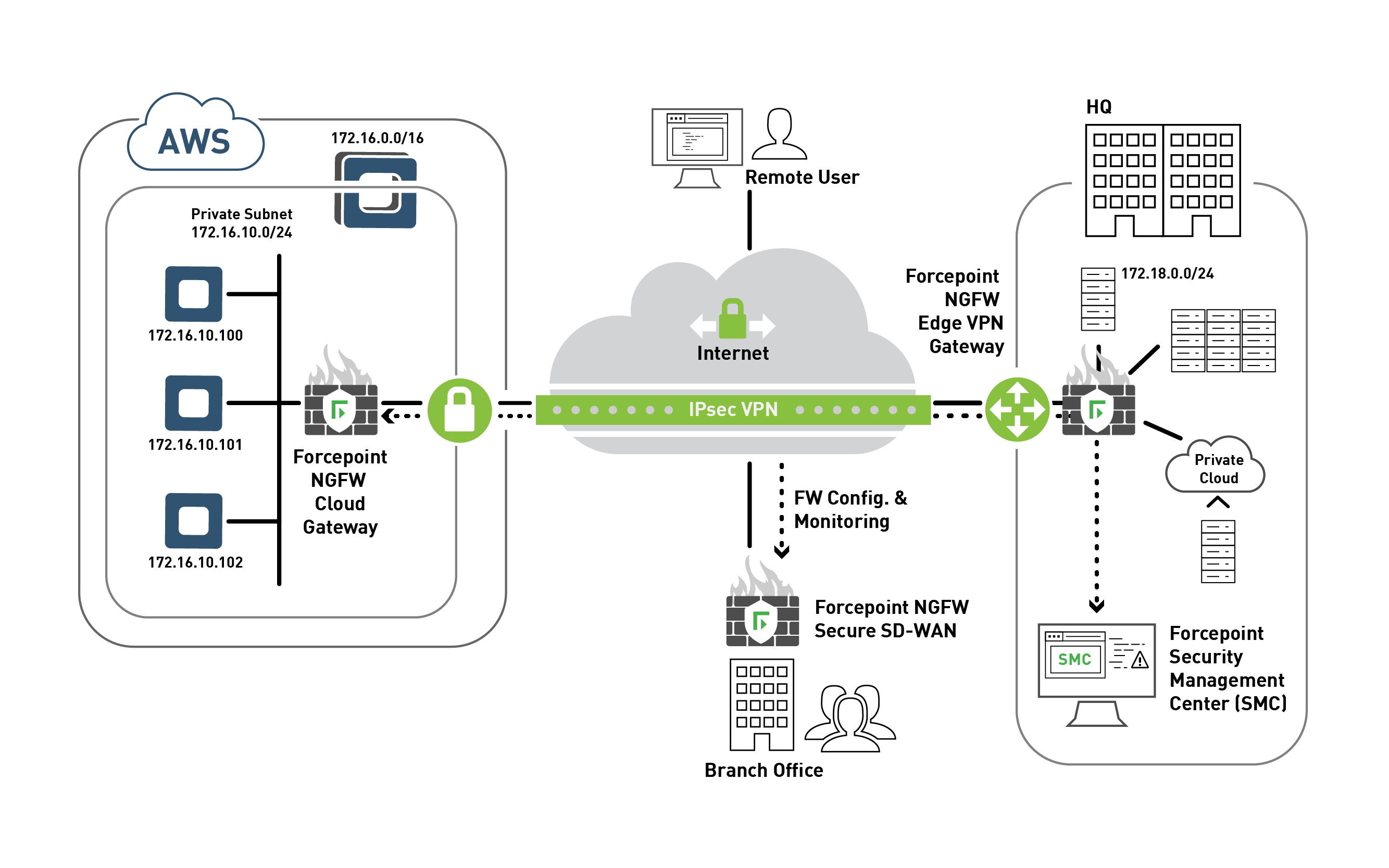
Our cloud security solutions are built to secure and enhance your AWS infrastructure, without compromising productivity or performance.
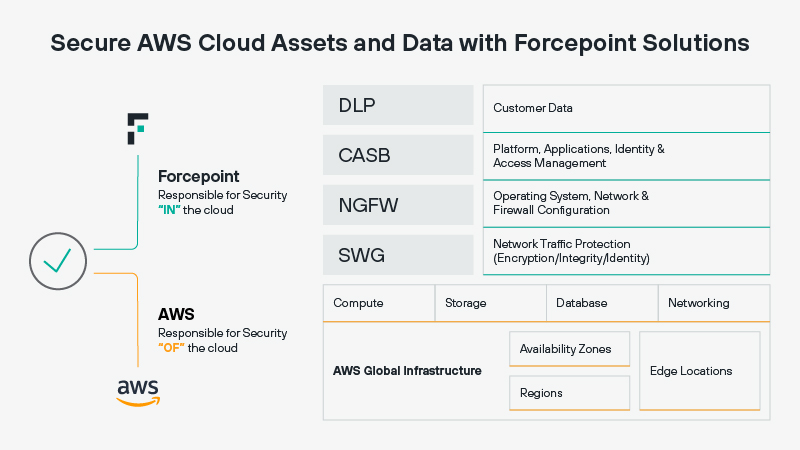
Secure AWS Cloud Assets and Data with Forcepoint Solutions
Next Generation Firewall (NGFW)
Unmatched visibility and secure connectivity using SD-WAN to dynamically connect your AWS VPC to your existing corporate network.
Cloud Access Security Broker (CASB)
Native to AWS, Forcepoint's CASB enables app discovery, granular access controls and risk-adaptive policies to protect AWS infrastructure.
Data Loss Prevention (DLP)
Extend visibility and control to protect critical data across on-prem and AWS infrastructure leveraging analytics to quickly identify and remediate data risks.
Forcepoint's cybersecurity solutions for AWS help protect organization's people and data in their cloud environments. These solutions work together to secure assets and help understand what data is being accessed, how it is being use, by whom, where and why.
Key Capabilities
Next Generation Firewall (NGFW)
- Centralized management that provides seamless visibility across both virtual and physical environments.
- Flexibility for supporting DevOps deployments in Hybrid environments.
- Smart, centralized policy mechanism that enables fast, accurate and consistent policy changes across physical, virtual and cloud deployment options.
- Integration with AWS Security Hub
- Available in Amazon Marketplace
- Accelerate compliance by using the pre-architected policies.
- Control data flows across all channels-network, endpoints and cloud apps.
- Focus on prioritized incidents to focus on high risk activity.
- Integration with AWS Security Hub.
Cloud Access Security Brokers (CASB)
- Discover and risk-prioritize all unsanctioned cloud use (Shadow IT) to quickly and easily determine if applications meet governance rules and avoid compliance issue.
- Implement geo-location-based access and activity monitoring for legitimate users and malicious actors.
- Track application usage for compliance, licensing and cost savings of unused accounts.
- Integration with AWS Security Hub.
Resources
Next Generation Firewall (NGFW)
- Forcepoint NGFW within Amazon Web Services solution brief
- Forcepoint NGFW Deployment Guide for AWS
- Integrating Forcepoint NGFW with AWS Security Hub Video
- Forcepoint NGFW and AWS Security Hub Integration Guide
- Speed, Efficiency, and Resilience – Can You Have it All?
Cloud Access Security Broker (CASB)
- Integrating Forcepoint CASB with AWS Security Hub Video
- Forcepoint CASB and AWS Security Hub Integration Guide
- Forcepoint CASB Datasheet
- Forcepoint DLP Brochure
- Forcepoint DLP Deployment Guide
- Integrating Forcepoint DLP data with AWS Security Hub Video
- Forcepoint DLP and AWS Security Hub Integration Guide
Watch AWS Global Security Lead Rohit Gupta talk AWS Security Hub, partnering with Forcepoint
Blog Post: Forcepoint Integration with AWS Security Hub
White Paper: Harnessing the Power of the Cloud Starts with Securing It