Angler Exploit Kit – Operating at the Cutting Edge
As we promised in one of our previous blog posts about exploit kits (Nuclear EK), we are going to take a more in-depth look at Angler Exploit Kit. Angler EK is possibly the most sophisticated exploit kit currently used by cyberciminals. It has pioneered solutions that other exploit kits started using later, such as antivirus detection and encrypted dropper files. In addition, Angler tends to be the quickest to integrate the latest zero days, such as the Adobe Flash zero day (CVE-2015-0311) from a few weeks ago, and it employs a notably unique obfuscation. Finally, Angler runs the dropped malware from memory, without ever having to write to the hard drive; this unique technique among exploit kits makes it extremely difficult for traditional antivirus technologies to detect it as they rely on scanning the file system.
While Angler is the most advanced exploit kit in today's threat landscape, Websense customers are protected from this threat with ACE, our Advanced Classification Engine, at the following stages:
- Stage 2 (Lure) - ACE has detection for the compromised websites.
- Stage 3 (Redirect) - ACE has detection for the injected code that redirects the user to the exploit page.
- Stage 4 (Exploit Kit) - ACE has detection for the malicious code that attempts to execute this cyber attack.
- Stage 5 (Dropper Files) - ACE has detection for the binary files associated with this attack
Obfuscation
Angler's landing page consists of four basic parts. Firstly, there is some visible English text, which is used to make the victim of the exploit kit believe they have browsed to a legitimate page. Secondly, it has various deobfuscation routines to deobfuscate the actual malicious scripts. These scripts are located within p class tags and they are encoded as base64. Decoding the base64 strings reveals the actual obfuscated exploit kit code. And finally, the landing page contains several encrypted strings, which contain various URLs leading to the various exploits (Flash, Silverlight, Internet Explorer) included in the kit.
Samples from Angler landing page
.png)
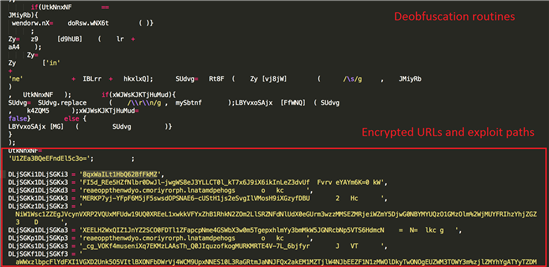
Deobfuscated Exploit Code
Once the landing page is deobfuscated, the true nature of the code is revealed. Angler, just like Nuclear and various other exploit kits, uses a very basic second layer obfuscation to make detection by security products even more difficult.
It also uses antivirus detection in addition to detecting various virtualization solutions (VMWare, VirtualBox, Parallels) as well as a web debugging proxy called Fiddler, which is widely used by security researchers. Implementing these measures makes it very difficult to observe and investigate this exploit kit in the wild, as most security researchers often rely heavily on these tools.
Detecting various .sys and .dll files which belong to AV and virtualization software
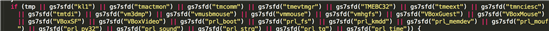
VMWare, VirtualBox, Parallels detection as well as Fiddler web debugging proxy
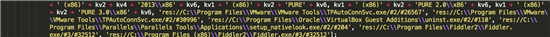
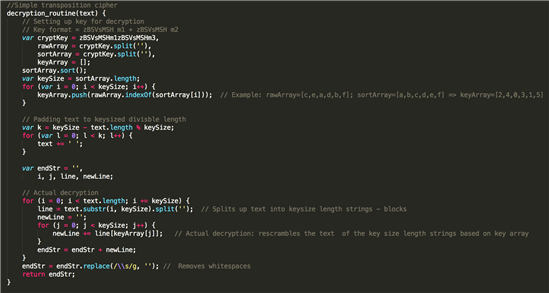
The most unique feature of Angler is the use of these encrypted URL paths. It uses a simple transposition-based cipher (in layman's terms: scrambling the letters) to encrypt and decrypt this data.
The decryption routine is embedded within the obfuscated part of the exploit kit.
Decryption routine as found in the kit
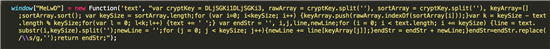
Decryption routine formatted and commented
We will use a very simple example to demonstrate how the decryption works. Suppose our cipher text (encrypted data) is "TEER CSURH TO PLTAOEL IX TP" and our decryption key is "OBFUSCATE". What Angler does is, it takes the alphabetical order of the letters in the key and rearranges the cipher text based on that. For example:
OBFUSCATE → 6,2,5,9,7,3,1,8,4
This gives us the order of letters in the cipher text. Using this we can easily decrypt it by rearranging the letters.
Example decryption
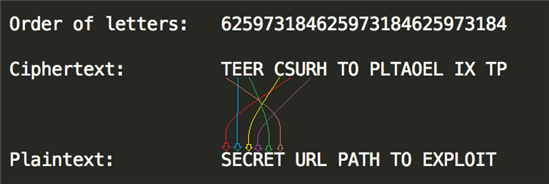
And finally whitespaces are removed from the decrypted string . Obviously, this is an extremely rudimentary form of encryption and would be very easy to crack even without the key if (such as in the above example) the plaintext consisted of actual words. However, Angler uses highly randomised URLs so this kind of encryption is more than sufficient to hide the true nature of these strings and the actual URL paths from various security products.
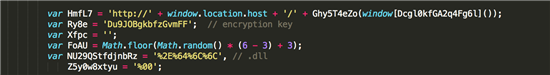
The rest of the deobfuscated code follows usual exploit kit patterns: there are various plugin detection and version check routines so the exploit kit 'knows' which exploit(s) to fire on the target. There are also quite a few shellcode builder routines as Angler uses a multi staged shellcode, where various stages are encoded and get decoded by the previous stages. It also includes a hardcoded encryption/decryption key for the dropper file.
Encryption key for payload
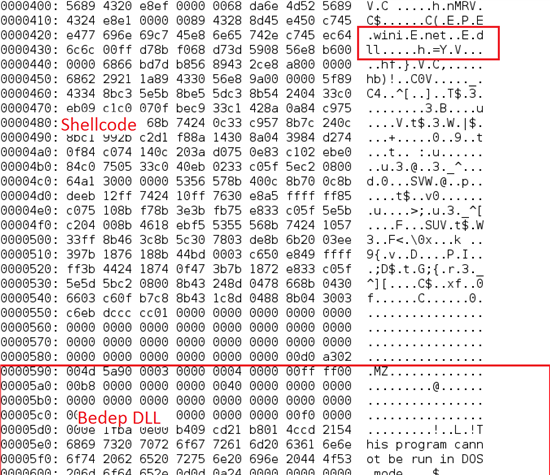
Multi stage Shellcode

Dropper
If the exploit succeeds, Angler's payload is dropped on the victim's system. As the payload travels through the network it is still encrypted and gets decrypted later by the final stage shellcode. This technique is used to make detection of the malicious dropper very difficult for traditional intrusion detection systems (IDS). As we mentioned before, Angler uses 'fileless' droppers, which mean that they are run directly from memory. The dropper used by Angler is called Bedep, which is actually only a downloader - that is, it is not malicious per se, but it is used to download and execute various different malware.
The payload consists of a combination of shellcode and the Bedep DLL. If the first few bytes of the payload are "909090" (NOPs or No Operations in x86 assembly) the DLL will be loaded from the memory, otherwise it will be written to the disk just like a normal dropper file. The shellcode is responsible for running the DLL from memory.
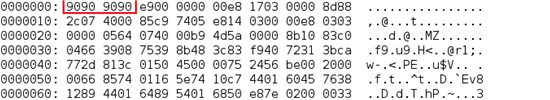
The shellcode resolves APIs such as kernel32.dll and wininet.dll
Summary
Angler Exploit Kit is no doubt one of the most dangerous exploit kits out there in the wild today. It has various techniques in its arsenal to defeat traditional detection methods such as:
- Unique Obfuscation
- Detects antivirus/virtualization software
- Encrypted payload
- Fileless infections
In addition Angler is often the first to adopt the latest exploits, which include zero days from time to time. The constantly evolving nature of Angler also highlights the need for security solutions that provide protection across the entire kill chain instead of only focusing on just one stage of it.
