5 Steps to SASE: Protecting Remote Workers, a discussion with Dr. Chase Cunningham
0 分鐘閱讀

Part of our ongoing series about SASE.Follow the hashtag #5steps2sase on Twitter and LinkedIn.
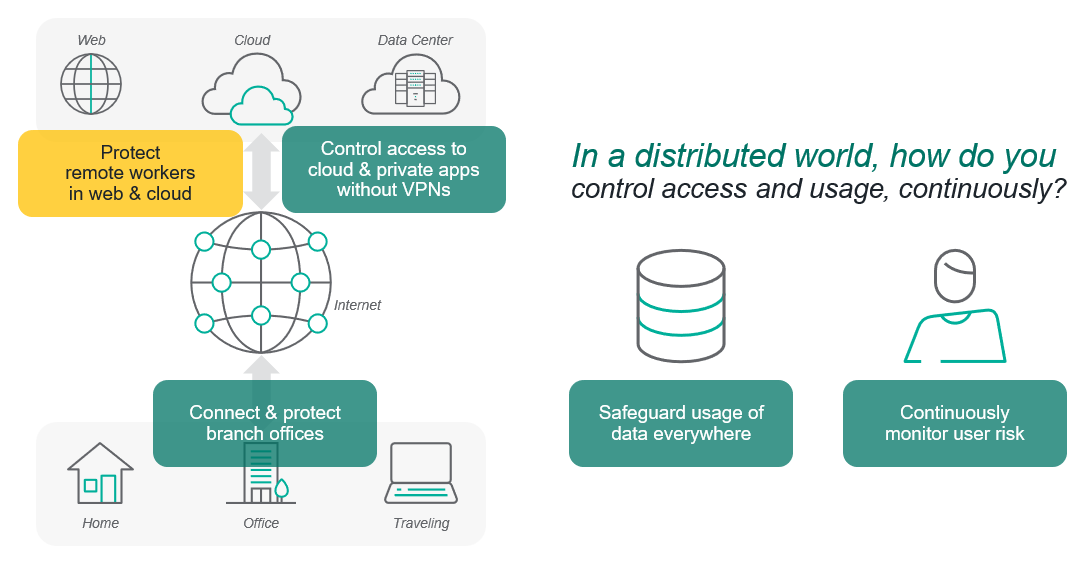
The SASE architecture is giving organizations around the globe a common foundation for thinking about how to do networking and security in today’s highly distributed world. CISOs and CIOs tell us over and over that they know they need to get away from the old infrastructure-centric approach with stacks of hardware at every location—and completely separate software stacks on laptops for remote or traveling users.
But one of the top questions we get is “Where should I begin?”
To shed some light on this crucial topic, I recently sat down with several experts to talk about five of the most common steps that businesses and government agencies tell us they’re taking in their journey to cloud-native connectivity and protection. These are quick conversations, no death by PowerPoint.
We’ll kick off the first session Wednesday, May 12.
The Protecting Remote Workers webcast represents the first step in a five-part series. For it I’ll be joined by Dr. Chase Cunningham, Chief Strategy Officer at Ericom Software Some of you may know him as “Dr. Zero Trust,” or when he was a Principal Analyst at Forrester.
We look at some of the best practices that real-world organizations have put in place in response to the events of the past 12 months for protecting people working on the web and in the cloud from home. We particularly focus on how remote browser isolation (RBI) has become a game-changer and a significant part of how SASE-based security is delivering Zero Trust-as-a-Service (ZTaaS). Several birds with one stone, as the old saying goes.
Chase and I always have fun when we talk. We hope you enjoy it as well. And join the conversation #5steps2sase on LinkedIn and Twitter.
在文章中
X-Labs
直接將洞察力、分析與新聞發送到您的收件箱
