Cybercriminals Exploit Brazil’s PIX Instant Payment Platform in New Phishing Attack
0 분 읽기

When any new technology comes along, scammers often jump on the opportunity to use it as a lure to steal personal information. When the technology is backed by a large organization and intended for use by an entire country, we are bound to see it used in nefarious ways.
PIX, a new instant money transfer service, is being launched to the public on 16th November 2020 by the Central Bank of Brazil (BCB). Forcepoint X-Labs have seen several email phishing campaigns using this service as a lure to steal banking details and passwords from would-be victims.
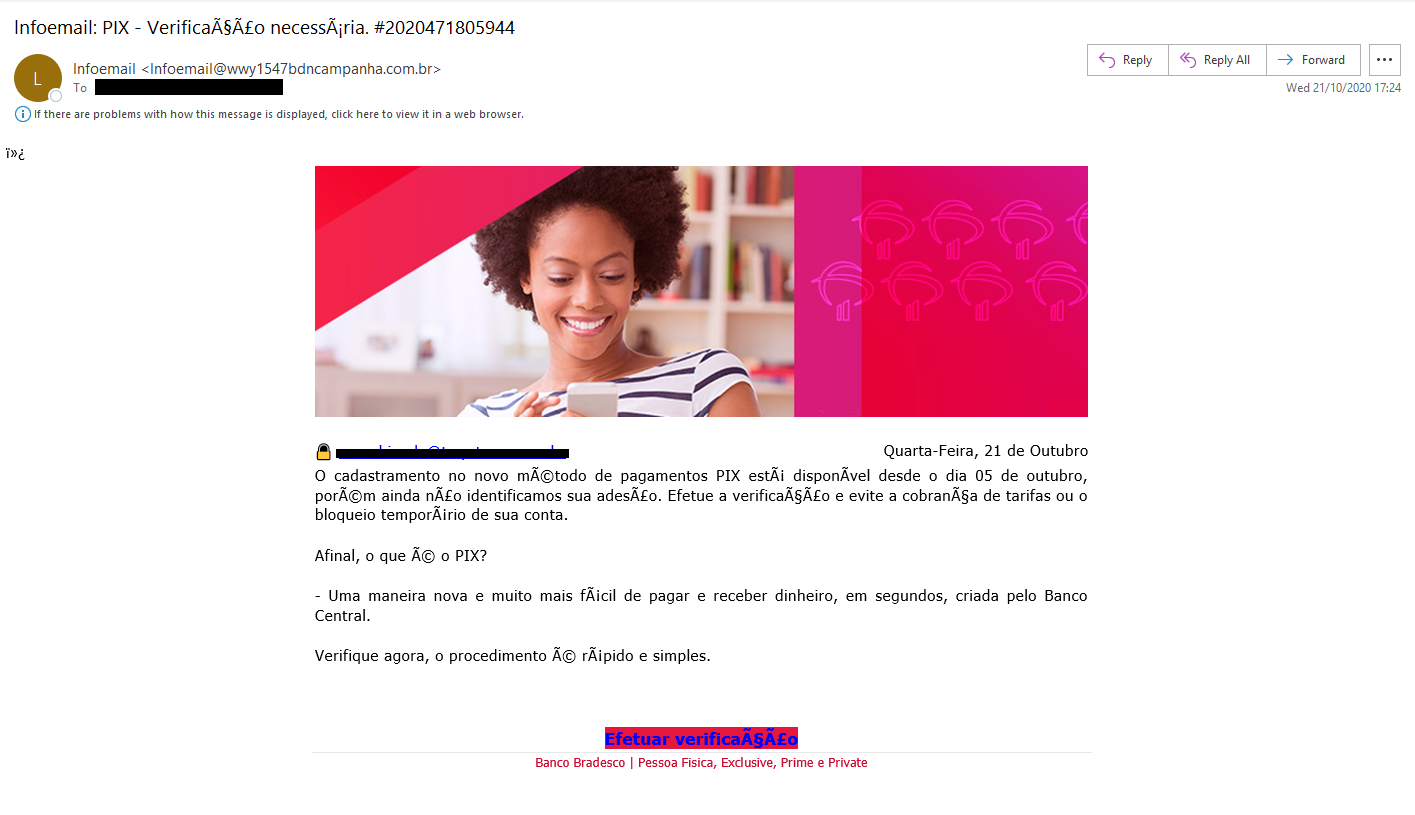
The largest campaign we have uncovered, with over 4,000 phishing emails sent (and blocked by Forcepoint Email Security) on 21st October 2020, urges users to register with the service with warnings of additional charges and blocked accounts if they do not act fast.
Here's the contents of the phishing email:
“Registration for the new PIX payment method has been available since October 5th, but we have not yet identified its membership. Perform the verification and avoid charging fees or temporarily blocking your account.
After all, what is PIX?
- A new and much easier way to pay and receive money, in seconds, created by the Central Bank.
Check now, the procedure is quick and simple.”
Here's what the phishing email looks like:
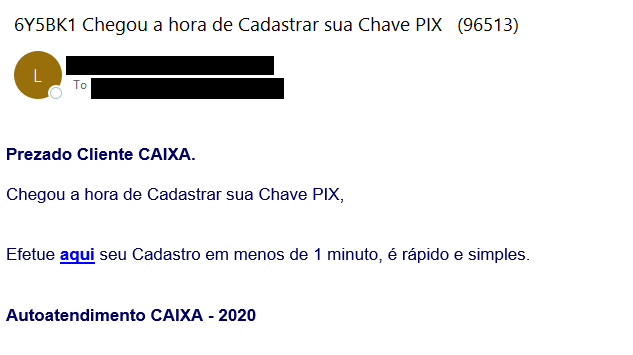
A smaller second campaign was uncovered on 6th October 2020 with over 1500 emails and was a simple call to register for the service. This is timely, and misleading, given that the registration for keys (e-mail, mobile number, etc) is due to commence on 3rd November 2020 according to public documents.
Here's the contents of the second phishing email:
“Dear CAIXA Customer.
It's time to Register your PIX Key,
Make your registration here in less than 1 minute, it is quick and simple.
CAIXA Self-Service – 2020”
And here's the second phishing email itself:
This campaign used a call to action URL from Google's free hosting service to lend some legitimacy to the phishing email and circumvent security scanning
In recent years, researchers across the industry have seen a huge uptick in the malicious use of free host services such as Google’s Firebase, Microsoft’s Azure and others. This has been covered widely by many security publications, but the services continue to be abused with very little attention from their admins.
Web Phishing
The phishing URLs in the above campaigns did not serve any content at the time of writing, however Forcepoint X-Labs are constantly updating and creating new analytics for our Forcepoint Advanced Classification Engine (ACE) to detect credential harvesting phishing pages as they discovered.
Conclusion
As we have outlined in our COVID-19 being used as a lure for malicious and phishing campaigns blog post, we stress the use of caution when unexpected emails are received regarding a well-publicized event or technology.
Attacker tactics, techniques and procedures (TTP) stay consistent over time with the theme of the lure changing to leverage current events. If kept up to date, your web and email security stack should remain effective against these adjustments in the threat landscape.
Protection Statement
Forcepoint customers are protected against this threat at the following stages of attack:
- Stage 2 (Lure) – Malicious emails associated with these attacks are identified and blocked.
- Stage 4 (Exploitation) – Malicious websites are identified and blocked.
- Forcepoint Advanced Classification Engine (ACE)솔루션 개요 읽기
X-Labs
내 받은 편지함으로 인사이트, 분석 및 뉴스 바로 받기
