The APT attack kill chain: seven stages, five strategies, one solution
0 分鐘閱讀
Forcepoint
Kill Chain
Originally, the term advanced persistent threat (APT) was used to describe nation-state cyberattacks designed to achieve strategic advantage. Today, the term has broadened to encompass a wide variety of attacks targeted at businesses for monetary gain. Cybercriminals have elevated the sophistication of their attacks and have become adept at stealing intellectual property.
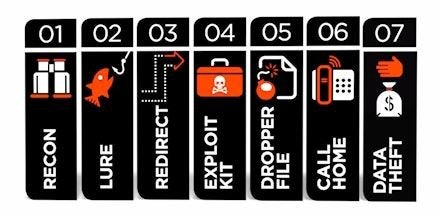 Seven Stages
Seven Stages
APTs consist of seven customary attack stages used by cybercriminals to enhance their theft success rate.
It's important for security professionals to be aware of this shift and recognize that traditional defenses are no longer effective. Antivirus, firewall and IDS/IPS products do not have the technology to address today's advanced threats. Organizations require a heightened level of protection to meet cybercriminals head-on and thwart inbound and outbound data theft attempts.
Five Strategies
APTs typically play out in multiple phases. In some cases, they may take months or even years to fully execute and successfully extract data from a network. To sufficiently prepare your organization for these vicious and effective cybercrime techniques, we have prepared the following five strategies:
- Real-Time Threat Analysis-To combat against spear-phishing, exploit kits, dynamic redirects and other types of APT attacks, organizations must employ more than traditional defenses. Real-time analysis provides security teams with a constant stream of data, which can be used to make vital and immediate decisions about an organization's security posture.
- Global Threat Awareness-Simply put, organizations benefit from large threat detection networks. The larger the network, the greater the threat awareness.
- DLP Capabilities-A fully contextually aware DLP solution must be deployed to protect sensitive data against exfiltration.
- Sandboxing-Effective analysis and reporting has become crucial for security professionals to make informed decisions about their organization's security posture.
- Forensic and Behavioral Reporting-A successful security deployment will include forensic and behavioral analysis and yield actionable reports. The more actionable the report, the more valuable it is to the organization.
One Solution
Due to increasingly complex attack and evasion techniques being used by bad actors, organizations need to have a dynamic approach to security. APTs and other targeted attacks are becoming more prevalent, but there are security solutions available to stop them. Be sure to choose a security solution that monitors inbound and outbound traffic for malicious behavior and provides real-time forensic reports. Identifying the threat in the early stages will help mitigate data loss, save countless man-hours and save your security team many sleepless nights.
Are you relying on dated security and/or point solutions to protect your organization from APTs? We'd love to hear the challenges your company might be facing and in return, offer advice on how you can better secure your data.

Forcepoint
閱讀更多文章 ForcepointForcepoint-authored blog posts are based on discussions with customers and additional research by our content teams.
在文章中
X-Labs
直接將洞察力、分析與新聞發送到您的收件箱
