
Plus de 12 000 clients ne peuvent pas se tromper










































Pour une meilleure visibilité et un meilleur contrôle des données sensibles
Mettez en lumière les dark data grâce à une découverte étendue des données et une classification hautement précise.
Le logiciel Forcepoint DSPM analyse n'importe quelle source de données et fait appel à la technologie propriétaire AI Mesh pour identifier, catégoriser et remédier aux données à haut risque.
C’est une solution idéale si vos équipes de sécurité rencontrent des difficultés avec :
De grandes quantités de données fantômes
Des autorisations trop larges d'accès aux données
À des risques de fuite de données par IA générative
À des emplacements de données non identifiés
Forcepoint DSPM Software Leads the Pack
Forcepoint is the only Data Security Posture Management vendor that uses AI Mesh technology to deliver highly accurate data classification. Read the full comparison chart to learn why organizations trust the leading data security provider to discover and catalogue data and remediate risk at scale.
20%
40%
60%
80%
100%
Forcepoint
Traditional Vendor
Data Governance Vendor
Forcepoint DSPM est un outil de sécurité de premier plan
Améliorer la visibilité des données
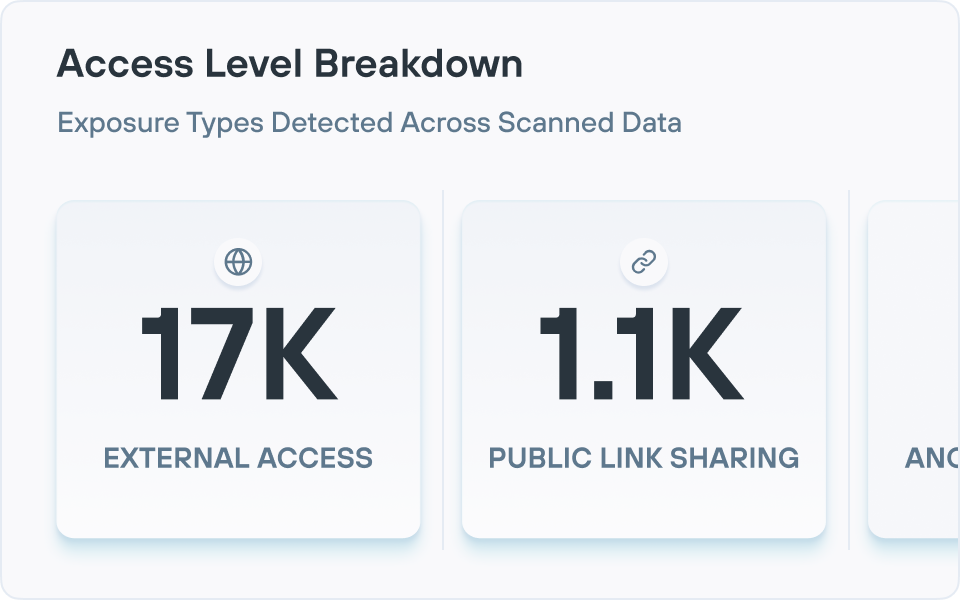
Obtenez une visibilité complète sur les données structurées et non structurées dans le cloud et sur site pour suivre et gérer les données de nature sensible où qu’elles se trouvent.
Découvrir et classifier avec l’IA
Faites appel à la technologie AI Mesh et à sa haute précision pour découvrir et classifier de façon efficace et fiable des données, en réduisant les faux positifs et en améliorant la précision des alertes
Corriger les risques de manière proactive
Des informations exploitables vous permettent de gérer les autorisations, de déplacer les données mal classifiées et régler les problèmes de souveraineté des données, d’accès, de duplication ou de données ROT.
Automatiser la gestion de la conformité
Simplifiez les processus de conformité grâce à l’automatisation afin d'assurer un alignement cohérent et continu sur des réglementations en constante évolution, réduisant ainsi la charge de travail manuel.


Précision pointue et rapports transparents
Enda Kyne, CTOO chez FBD Insurance, déclare que ses équipes de sécurité informatique et de protection des données ont adopté DSPM ET DDR pour leur capacité à contrôler les données critiques et à rendre compte des activités aux régulateurs.
Strengthen Your Data Security Posture



Rapidly and precisely identify sensitive data-at-rest with AI Mesh technology that fine-tunes its classification accuracy relative to your unique organizational needs.

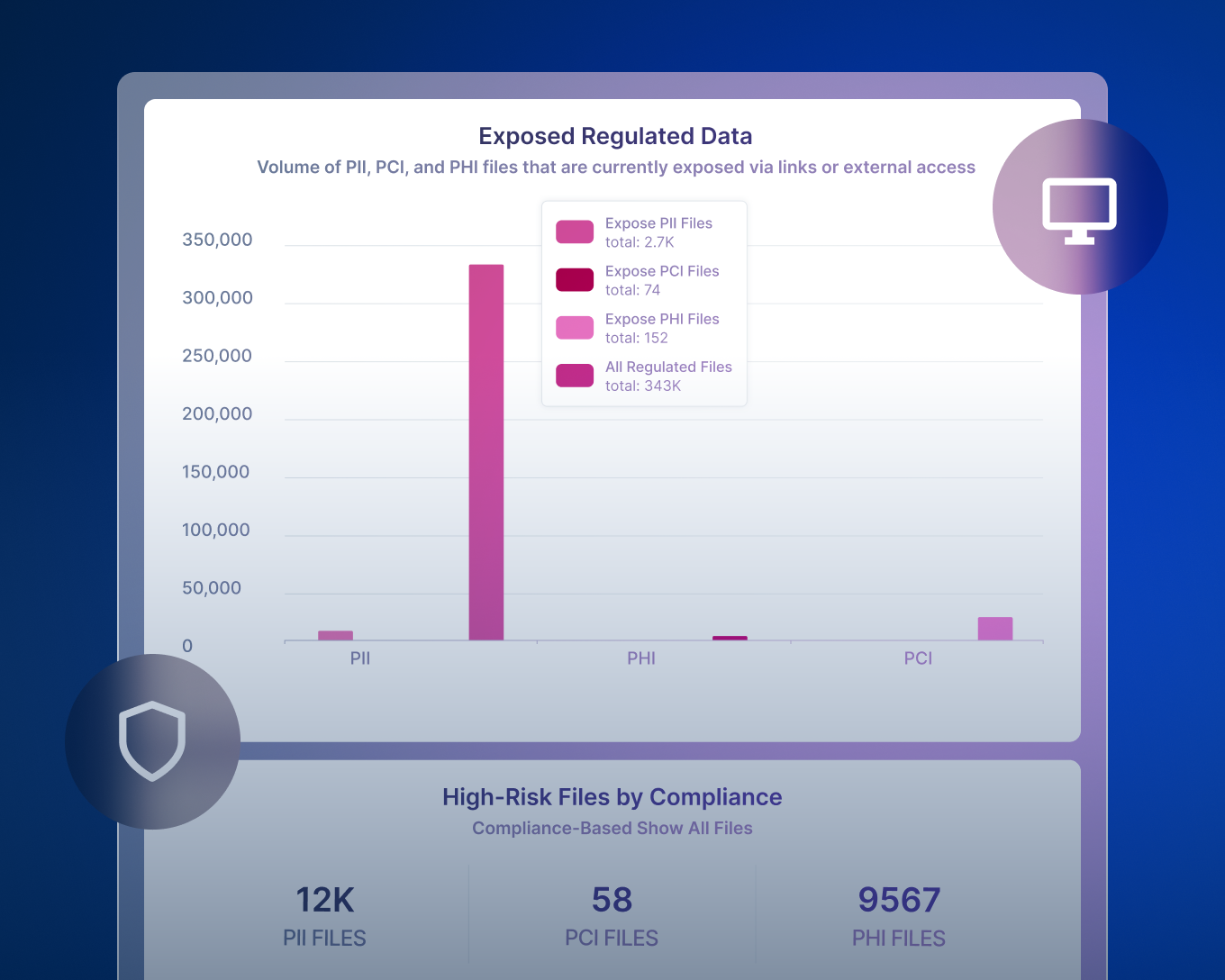
Extend visibility and control over all your regulated data, eliminate gaps and generate automated reports to demonstrate compliance.

Gain a centralized view of your data and enforce the Principle of Least Privilege across cloud, SaaS and on-prem systems for effective governance.


Vos données sont-elles en danger ?
Une évaluation des risques liés aux données permet de détecter de manière proactive les menaces qui pèsent sur vos données, qu'il s'agisse de fichiers sensibles non classifiés ou d'utilisateurs ayant reçu une autorisation excessive. Obtenez une évaluation gratuite des risques liés aux données avec Forcepoint pour voir la gestion de la posture de sécurité des données (DSPM) en action et savoir à quel point vos données sont sûres.



Capacité à intégrer DLP, DSPM et DDR pour la découverte, la classification, la protection et la remédiation des données.

Fournit un rapport des risques efficace, vous permettant de voir les données ROT (redondantes, obsolètes, triviales), les données ayant reçu une autorisation excessive, les problèmes de souveraineté des données et bien d'autres qui rendent la posture globale des données risquée.

Offre une visibilité et un contrôle de la préparation des données pour toutes les applications GenAI. Il est également capable de sécuriser l'utilisation de Copilot et ChatGPT Enterprise.
Témoignages de nos clients
Témoignages de nos clients
"As part of Forcepoint’s broader data security ecosystem, DSPM has integrated seamlessly with our existing solutions. It’s an essential component of our overall data security strategy."
Indonesia Financial Group (IFG)
Recommandé par les analystes.
Approuvé par les utilisateurs.
Forcepoint est régulièrement classé parmi les meilleurs logiciels de prévention de la perte des données et fournisseurs de logiciels de sécurité des données par les utilisateurs et les analystes de l'industrie.
Forcepoint a été nommé leader dans l’évaluation IDC MarketScape: Worldwide DLP 2025 Vendor Assessment.
Pour la deuxième année consécutive, Forcepoint a été nommée 2024 Global DLP Company of the Year par Frost & Sullivan.
Forcepoint reconnu comme un acteur de premier plan dans The Forrester Wave™ : Data Security Platforms, T1 2025.
Adoptez les meilleures pratiques en matière de Data Security Posture Management
Questions les plus fréquemment posées
Qu'est-ce que Data Security Posture Management (DSPM)?
Data Security Posture Management est une solution de sécurité qui découvre en permanence où se trouvent les données sensibles, comment elles sont classifiées et qui peut y accéder dans les environnements cloud, SaaS et sur site.
Le DSPM native de Forcepoint, basé sur l'IA, suit ce même modèle : il inventore en permanence les données structurées et non structurées, utilise la technologie AI Mesh pour classifier avec précision ces données sur les stockages de fichiers, les applications cloud et les emplacements sur site, et évalue si l'une de ces données est à risque grâce à une variété d'objectifs.
Forcepoint DSPM aide à augmenter la productivité, à réduire les coûts, à réduire les risques et à simplifier la conformité en transformant une posture d'un audit périodique en une vue pratique des risques liés aux données.
Comment fonctionne DSPM?
La plupart des plateformes DSPM suivent un cycle de vie récurrent : découvrir les données (structurées et non structurées sur plusieurs clouds et sur site local), classifier les données par sensibilité et contexte commercial, évaluer et hiérarchiser les risques (tels qu'un accès trop privilégié ou des données mal localisées), remédier aux erreurs de configuration ou à l'accès non sécurisé, puis surveiller en permanence pour maintenir la posture à jour.
Forcepoint DSPM met en œuvre cela avec AI Mesh, une architecture de classification d'IA utilisant de petits modèles de langage et des réseaux de neurones profonds. Forcepoint DSPM analyse les sources de données intégrées, identifie et catégorise les données à haut risque et recommande les prochaines étapes pour les remédier afin que l'équipe puisse ajuster les autorisations, déplacer les données égarées, nettoyer les données redondantes, obsolètes ou triviales (ROT) et résoudre les problèmes de souveraineté au lieu de s'arrêter aux rapports.
Les mises à jour récentes étendent Forcepoint DSPM au-delà des fichiers aux bases de données d'entreprise et aux lacs de données. Le même modèle de découverte, de classification et d'application adaptative couvre désormais les données structurées et non structurées sur une plateforme unique et unifiée aux côtés de Forcepoint DDR et DLP.
Comment fonctionnent les capacités de découverte des données du logiciel DSPM?
DSPM recherche en permanence les données sur le cloud, le réseau et les emplacements de stockage sur site pour découvrir et cataloguer chaque élément de données dont dispose votre entreprise. Trouver les données sensibles est la première étape cruciale pour les protéger. Les solutions DSPM analysent l'ensemble de votre écosystème de données, notamment:
- Les plateformes cloud (AWS, Azure, GCP)
- Les applications SaaS (Microsoft 365, Salesforce)
- Les stockages et bases de données sur site
Le logiciel DSPM moderne maintient une visibilité continue à mesure que les données se déplacent et changent grâce aux fonctionnalités existantes ou aux intégrations de solutions.
Quelles capacités de classification des données et d'évaluation des risques DSPM fournit-elle?
Une solution mature de DSPM offre une chaîne de capacités :
- Découverte des données et classification alimentée par l'IA : analyse automatisée du cloud, des SaaS, des terminaux et des magasins sur site, grâce à une IA affinée pour classifier avec précision les données structurées et non structurées par sensibilité et objectif commercial, tout en proposant des modèles adaptables pour réduire les faux positifs.
- Évaluation des risques liés aux données, analyse et priorisation : création d'un inventaire des données sensibles, puis note les risques en fonction de l'exposition, de l'accès trop permissif et de l'impact sur l'entreprise pour que les équipes se concentrent d'abord sur les ensembles de données les plus critiques ; Forcepoint utilise le score et les estimations de l'impact financier pour prioriser l'atténuation
- Gouvernance de l'accès : identifiez qui a accès à quelles données, en mettant en évidence le partage public ou externe, les comptes inactifs et les dossiers surpartagés, avec une visibilité approfondie sur les autorisations grâce à l'intégration des répertoires.
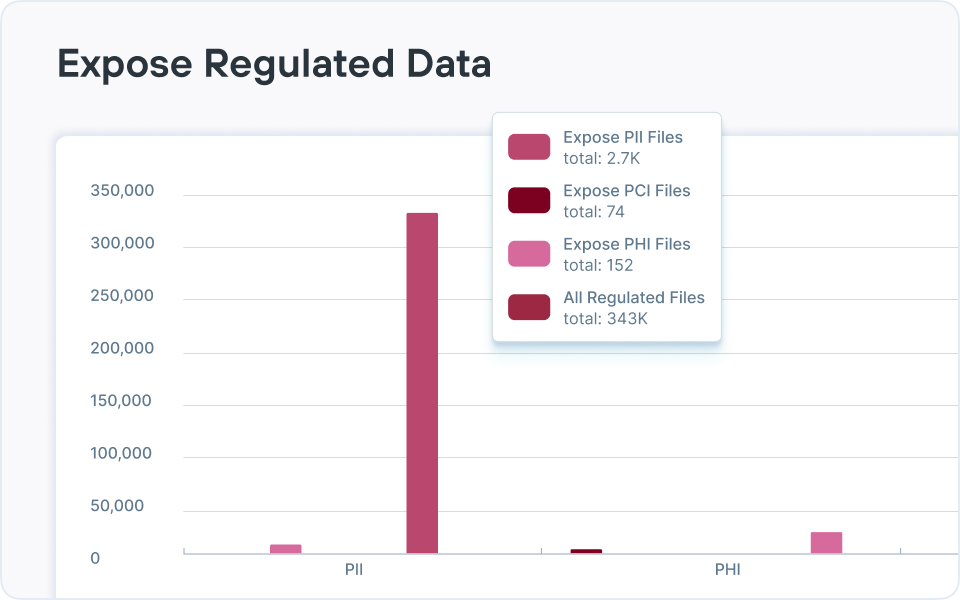
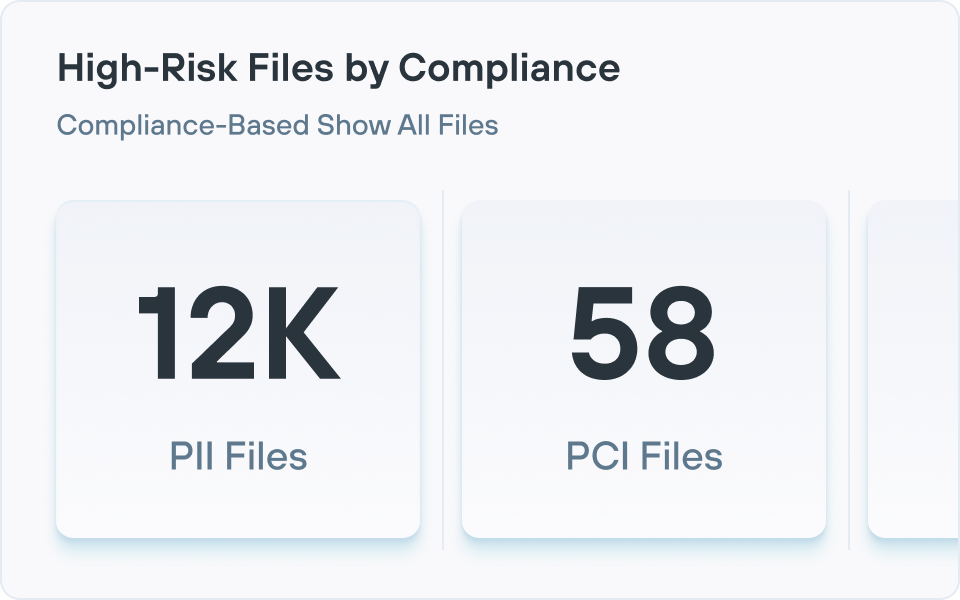
- Conformité et rapports : génération de tableaux de bord, de pistes d'audit et de rapports alignés sur les cadres (pour les réglementations comme le RGPD ou HIPAA) qui cartographient les données réglementées, documentent les contrôles et simplifient les audits ; Forcepoint ajoute des modèles de politiques, des rapports automatisés et une classification explicative par IA pour simplifier la démonstration de la conformité dans les environnements hybrides.
Comment une plateforme de gestion de la posture de sécurité des données (DSPM) aide-t-elle les entreprises à gérer et à remédier aux risques?
Identifier les problèmes sans résolution crée peu de valeur. Les plateformes modernes de gestion de la posture de sécurité des données (DSPM) répondent à cette nécessité avec des contrôles personnalisables qui s'adaptent aux besoins et aux défis uniques de votre entreprise. Ces contrôles incluent la gestion des autorisations pour mettre en œuvre le principe du moindre privilège (PoLP), en garantissant que les utilisateurs n'accèdent qu'aux fichiers nécessaires pour leurs tâches et en remédiant aux données sur-autorisées ou accessibles au public. Les capacités supplémentaires incluent la cartographie des données qui catégorise correctement les informations sensibles, la remédiation des données mal localisées pour traiter les fichiers stockés dans les référentiels inappropriés et les processus d'archivage/suppression des données pour la gestion des fichiers à risque après les périodes de rétention ou classés comme Redondants, Obsolètes ou Triviaux (ROT).
Comment fonctionnent les rapports et les analyses dans le logiciel de gestion de la posture de sécurité des données (DSPM)?
Les solutions de gestion de la posture de sécurité des données (DSPM) incluent des outils de rapport et d'analyse qui fournissent une visibilité sur l'état général de la sécurité des données d'une entreprise. Ces capacités de rapports comprennent généralement des tableaux de bord montrant où se trouvent les données sensibles dans les environnements, en soulignant les facteurs de risque spécifiques comme les données Redondantes, Obsolètes ou Triviales (ROT), les fichiers sur-autorisés, les informations mal localisées et les doublons. Les équipes de sécurité peuvent utiliser ces informations pour suivre les indicateurs au fil du temps et donner la priorité aux efforts de remédiation là où ils auront le plus grand impact.
Forcepoint DSPM est-il déployé sur site ou dans le cloud ?
Les solutions de gestion de la posture de sécurité des données (DSPM) offrent des options de mise en œuvre flexibles:
- SaaS sur cloud pour un déploiement rapide
- Modèles hybrides pour les environnements sensibles
- Sur site pour un contrôle de la souveraineté des données
- Architectures sans agent pour minimiser les frais généraux
La plupart des entreprises commencent par leurs référentiels de données les plus critiques et élargissent la couverture par étapes.
Comment Forcepoint DSPM utilise-t-il l'IA et l'automatisation ?
L'automatisation permet la découverte et l'analyse continues et à grande échelle des données dans les environnements d'entreprise. Les entreprises peuvent maintenant classifier automatiquement les données en temps réel au fur et à mesure qu'elles sont créées, déplacées ou modifiées, ce qui élimine les retards et les lacunes inhérentes aux examens manuels. La principale valeur ajoutée de l'intelligence artificielle réside dans la classification des données très précise tout en réduisant les faux positifs. L'IA apporte la précision nécessaire pour distinguer en toute confiance les données vraiment sensibles des informations bénignes qui pourraient déclencher une alerte sur des systèmes traditionnels basés sur des règles. Pour que les solutions de gestion de la posture de sécurité des données (DSPM) intègrent pleinement ces capacités, les solutions modernes doivent traiter un large éventail de types de fichiers, des PDF aux vidéos, et comprendre un éventail encore plus large de champs de données pour leur attribuer les classifications correctes et répondre aux exigences de conformité. Cela inclut l'exploitation des capacités de l'IA générative, des classificateurs de réseaux neuronaux profonds et d'autres technologies d'IA prédictive associées entre elles.
Quels sont les principaux avantages que les entreprises peuvent tirer de la mise en œuvre d'une plateforme de gestion de la posture de sécurité des données (DSPM)?
Les avantages de la gestion de la Data Security Posture Management peuvent se résumer en quatre résultats:
- Augmentation de la productivité
- Réduction des coûts
- Réduction des risques
- Rationalisation de la conformité
DSPM s'intègre-t-il avec d'autres technologies de sécurité?
DSPM fonctionne rarement de manière isolée. La plupart des organisations l'intègrent avec des technologies de sécurité complémentaires pour créer une stratégie globale de protection des données. Les informations fournies par le logiciel Data Security Posture Management (DSPM) sur l'emplacement des données, la sensibilité et les risques améliorent naturellement les autres outils de sécurité tels que:
- Data Detection and Response (DDR)
- Data Loss Prevention (DLP)
- Cloud Access Security Broker (CASB)
- Identity and Access Management (IAM)
- Cloud Security Posture Management (CSPM)
En quoi DSPM diffère-t-il des outils de classification des données existants?
Contrairement aux outils traditionnels qui fonctionnent avec les référentiels de données connus sur la base de règles prédéfinies, DSPM découvre en permanence les données connues et inconnues dans tous les environnements, en tirant parti de l'IA pour une classification plus précise et en fournissant un contexte concernant les modèles d'accès et les contrôles de sécurité.
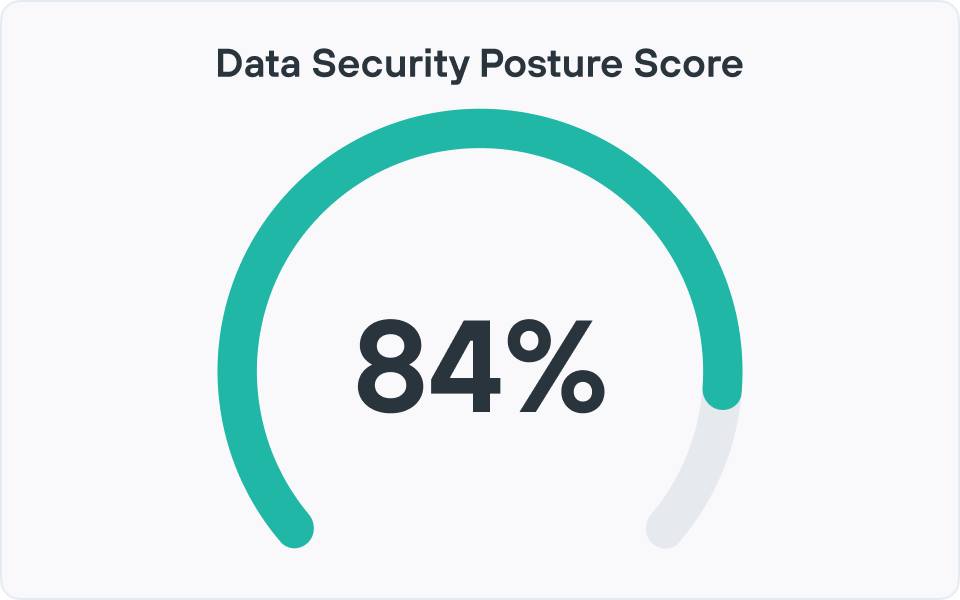
Comment le DSPM aide-t-il à évaluer la posture de sécurité ?
Data Security Posture Management (DSPM) évalue la posture de sécurité en découvrant en permanence où se trouvent les données sensibles (cloud, SaaS, sur site), en les classifiant par sensibilité et en cartographiant qui y a accès.
Forcepoint DSPM utilise son moteur AI Mesh ainsi que de larges connecteurs pour inventorier les données structurées et non structurées. Il met en évidence les fichiers surexposés, les données ROT et les autorisations à risque et les corréle dans une évaluation des risques liés aux données. plus
Il fournit ensuite une surveillance et des analyses haute performance pour montrer quelle quantité de données sensibles sont à risque, quels sont les emplacements et les unités d'entreprise les plus exposés et comment les changements au fil du temps ont un impact sur les risques globaux liés aux données. Ces informations sont présentées dans des tableaux de bord et des rapports détaillés, offrant aux équipes de sécurité et de conformité une vue actuelle et mesurable de leur posture en matière de sécurité des données au lieu d'audits ponctuels.
Quelle est la différence entre SSPM, CSPM et DSPM ?
CSPM (Cloud Security Posture Management) se concentre sur l'infrastructure cloud : configurations, contrôles réseau, identités et services de plateforme. Il identifie et aide à corriger les erreurs de configuration dans les environnements IaaS, PaaS et SaaS, mais pas le contenu des données elles-mêmes.
SSPM (SaaS Security Posture Management) est une solution centrée sur les applications SaaS : paramètres de sécurité, accès et intégrations entre services comme Microsoft 365, Salesforce et plus encore.
Le DSPM (Data Security Posture Management) se concentre spécifiquement sur les données : découvrir, classifier et évaluer les risques liés aux informations sensibles où qu'elles soient stockées. Il répond à « quelles données avons-nous, où sont-elles, qui peut y accéder et quels sont les risques d'une telle exposition ? »
Forcepoint DSPM offre-t-il une surveillance en temps réel et une détection des risques ?
Oui.Forcepoint DSPM fournit une évaluation des risques en temps réel ou à haute fréquence lors de l'analyse, met à jour les tableaux de bord avec les niveaux d'exposition et tire parti d'un système d'alerte avancé pour signaler automatiquement les anomalies et les violations potentielles. plus plus
Comment le DSPM améliore-t-il la sécurité cloud ?
Le DSPM améliore la sécurité cloud en offrant une visibilité complète sur les données sensibles stockées sur le stockage cloud, les plateformes SaaS et les bases de données. Il montre exactement quelles données existent, leur degré de sensibilité, où elles se trouvent et comment elles sont partagées. plus plus
Forcepoint DSPM analyse les principaux fournisseurs de cloud et les sources d'identité pour découvrir les données surexposées, les autorisations excessives et les contenus sensibles mal localisés que les outils cloud traditionnels manquent.
Dans ce contexte, les équipes de sécurité peuvent appliquer l'accès le moins privilège dans le cloud, prioriser les mesures correctives en fonction de l'impact réel sur les activités et la réglementation et intégrer les résultats du DSPM au DLP et à d'autres contrôles.
Quels sont les avantages de l'utilisation du DSPM pour la sécurité cloud ?
L'utilisation du DSPM dans les environnements cloud offre des résultats concrets : une exposition réduite des données (grâce à la détection des surexpositions et au nettoyage des autorisations), une réduction des angles morts sur les multicloud et les SaaS et une meilleure protection de la PI et des données réglementées. plus plus
Forcepoint AI Mesh améliore la précision de la classification de Forcepoint DSPM, ce qui réduit directement les faux positifs et aide les équipes à se concentrer sur les risques réels.
Il améliore également l'efficacité opérationnelle grâce à l'automatisation, aux tableaux de bord intégrés et aux rapports. Il raccourcit les cycles d'enquête et de remédiation, réduit les coûts de stockage et de gouvernance en traitant les données ROT et en préparant la conformité aux audits et aux réglementations en matière de protection des données.
Le DSPM aide-t-il à la détection des menaces liées à l'identité et à la réponse à ces menaces ?
DSPM n'est pas une plateforme de détection des menaces d'identité et de réponse (ITDR), mais Forcepoint DSPM détecte les risques liés à l'identité liés aux données. Il identifie les utilisateurs et les groupes pouvant accéder aux fichiers sensibles, met en évidence les utilisateurs à risque excessif ou à haut impact et identifie les modèles d'accès suspects grâce à des analyses et des alertes. plus
Ces informations permettent aux équipes de sécurité d'enquêter rapidement sur les abus potentiels d'identité (par exemple, un utilisateur ayant un accès excessif à des données critiques) et de prendre des mesures ciblées comme révoquer l'accès, restreindre le partage ou déclencher des workflows dans les outils de sécurité existants – renforçant la protection des données centrées sur l'identité sans avoir à deviner.
Comment le DSPM détecte-t-il et évalue-t-il l'exposition des données sensibles ?
Forcepoint DSPM utilise des connecteurs pour analyser les stockages de données dans le cloud et sur site à grande échelle, puis applique la classification AI Mesh et des détecteurs configurables pour identifier les données sensibles (PII, PCI, PHI, IP, etc.) en fonction du contenu et du contexte.
Il évalue ensuite l'exposition en analysant les paramètres de partage et les autorisations pour signaler les données publiques, partagées à l'externe, surpartagées en interne, mal localisées ou associées à des utilisateurs à risque, et quantifie ces risques dans des tableaux de bord et des rapports afin que les équipes puissent prioriser la remédiation.
Comment le DSPM simplifie-t-il les rapports de conformité ?
Forcepoint DSPM centralise les preuves nécessaires pour les réglementations comme le RGPD, le HIPAA et d'autres exigences en matière de confidentialité et de souveraineté en documentant en permanence où se trouvent les données réglementées, comment elles sont protégées et qui peut y accéder. Sa fonction de rapports et sa suite d'analyses montrent le degré de préparation à la conformité et les risques liés aux données sur les cadres les plus populaires.
Quels tableaux de bord Forcepoint DSPM inclut pour les équipes de conformité ?
La suite Forcepoint DSPM Analytics inclut des tableaux de bord prédéfinis tels que l'analyse de la surexposition, l'analyse de l'exposition aux ransomware, la duplication des données critiques, la détection des utilisateurs à risque, la rétention des données, les données égarées, l'évaluation des risques liés aux données et le suivi des incidents pour les violations du contrôle des données.
Les équipes de conformité peuvent également créer des tableaux de bord personnalisés à l'aide de widgets intégrés (compteurs, graphiques, tableaux, vues d'incidents, etc.) basés sur le langage de requête de DSPM, et exporter ces vues sous forme de rapports pour leur permettre d'adapter la surveillance à des réglementations spécifiques, aux unités opérationnelles ou aux catégories de données sans besoin de développement personnalisé. plus



