Zero Trust Network Access (ZTNA): The cure for the common VPN
0 분 읽기

Editor's Note: This is part of our ongoing series about Zero Trust.
Zero Trust is quickly becoming one of the hottest topics in cybersecurity (check out the Cyber Voices Zero Trust Summit taking place tomorrow and Wednesday) as people adapt to "a new normal."
When the world turned upside down in March 2020, many IT organizations performed heroic acts to get their employees working from home. Often, this meant teaching newly remote workers how to use VPN clients to connect back into the enterprise network for access to internal private applications or to safely use the internet through existing on-premises security gateways.
That approach had been okay for small numbers of people working outside an office. But when everybody suddenly had to work from home, it became clear that VPNs were a short-term fix at best.
VPNs and users don’t mix well
Here’s a sentiment I’ve hinted at before: I love VPNs” said nobody. Ever.

It used to be that VPNs were necessary for road warriors to get email from Exchange or Lotus, use important applications like Oracle, and comply with acceptable use guidelines enforced by on-premises security gateway. But, with cloud-based apps such as Microsoft Office 365, Salesforce, and others rapidly becoming the standard for enterprise productivity and collaboration, connecting back to HQ just to go back out to the internet is beginning to get in the way.
Forcing users to remember which apps need VPNs and which don’t changes how they’re used to working. This creates confusion and even resentment, both of which gets in the way of doing their jobs. Worse yet, VPNs are notorious for slowing down cloud apps, especially highly interactive ones. The very ones that enterprises have been switching to. People’s frustration gets taken out on helpdesk teams and motivates users to avoid turning on their VPNs. Instead, they often look for cloud-based alternatives to internal private applications—magnifying the classic challenge of shadow IT.
Worse yet, VPNs often end up creating new security problems. Users sometimes go to great lengths to avoid using VPNs, leaving themselves unprotected by internal gateways (which we covered in our SASE series a few months ago). Then, when they do connect to the VPN, often they are given the same full range of access on internal networks that they would have in the office. They can get to any application, any server, any database, and so on. But it also means that anybody who is pretending to be an authorized user, or who has compromised the user’s laptop or the public Wi-Fi network where they’re connecting from, also can get to anything.
This isn’t a new problem, but it is made worse when people work remotely especially as the line between work and life begins to blur. We all have probably had times when we use our business laptop to go to a recreational website, order dinner, or stream content that we might not do from a machine in the office. This opens the door to attackers who compromised devices and use them as a springboard for getting into otherwise-protected networks.
Ditch the VPN, keep the apps with Zero Trust Network Access
Limiting what remote users can access can be done with network security technologies such as firewalls. But setting up intricate rules for controlling which users can get to which parts of the network—called microsegmentation—requires expertise and can lead to errors as resources move around.
That’s where Zero Trust Network Access (ZTNA) comes in. Often delivered as a cloud-based service such as Forcepoint Private Access, ZTNA systems tailor each user’s access to just the specific applications they need. Everything else on the internal network remains hidden. This approach makes it possible for networking teams to provide remote access to line-of-business applications while security teams retain the visibility and control they need to keep the enterprise safe.
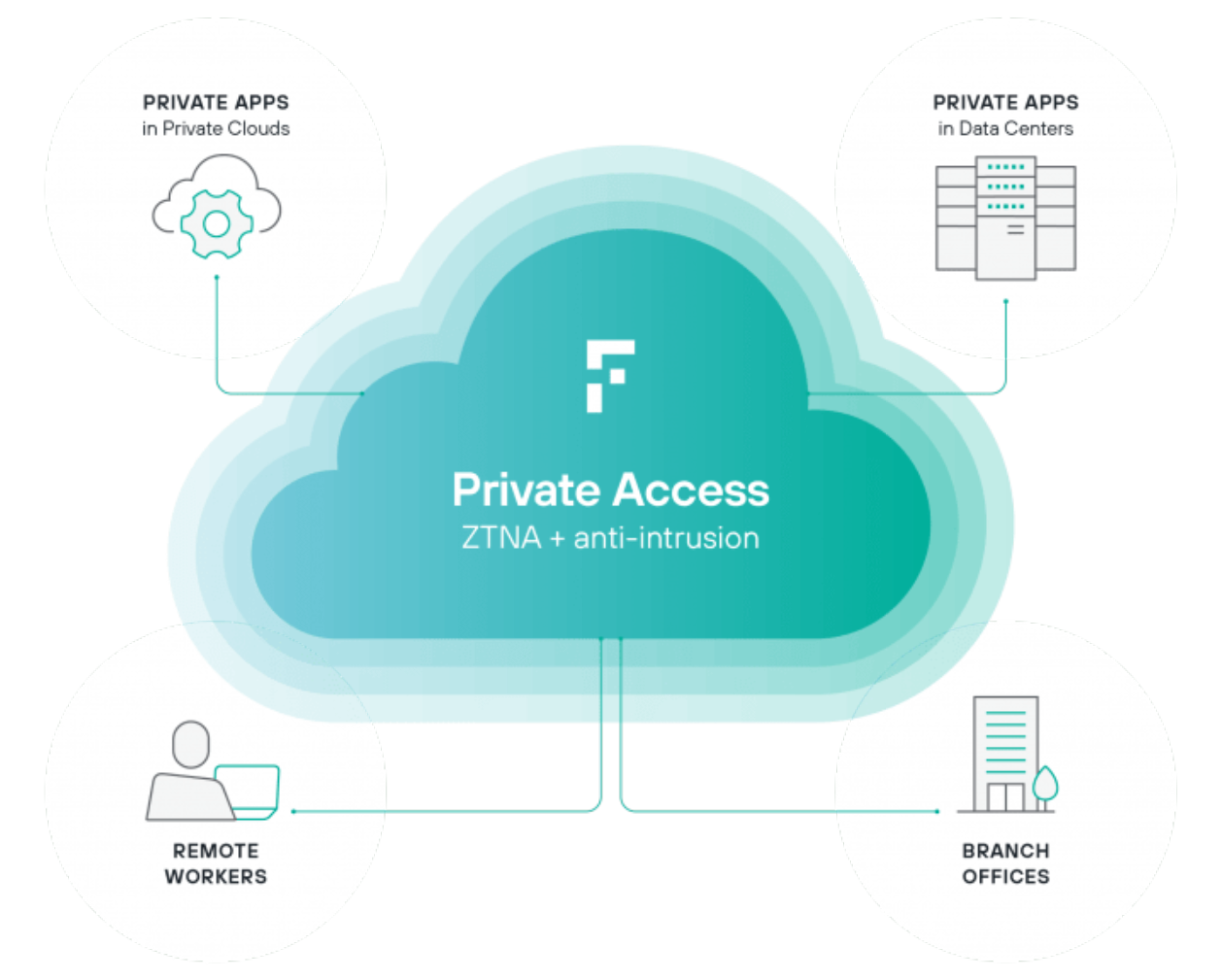
And that’s just the start. Controlling access is just the beginning of Zero Trust. Check out other Zero Trust-related posts, including Ashish’s recent post that covers controlling usage of data. If you'd like to hear more on this topic, tune in Wednesday, December 9 at 11am CST (17:00GMT) to hear me and Fabio Rosa, Consulting Systems Engineer discuss SASE, Zero Trust and more. Click on the green Register Now button to do so.

You can also learn more about Zero Trust in the following:
- Forcepoint Private Access product page to get an overview of our solution or to schedule a demo.
- Your Path to Zero Trust eBook to understand why Zero Trust is dominating cybersecurity discussions, the pillars modern Zero Trust and more.
- Zero Trust product page that shows how Forcepoint’s products work together to help you take a modern approach to implementing Zero Trust.
기사에서
X-Labs
내 받은 편지함으로 인사이트, 분석 및 뉴스 바로 받기
