12,000명 이상의 고객이 잘못할 수 없습니다










































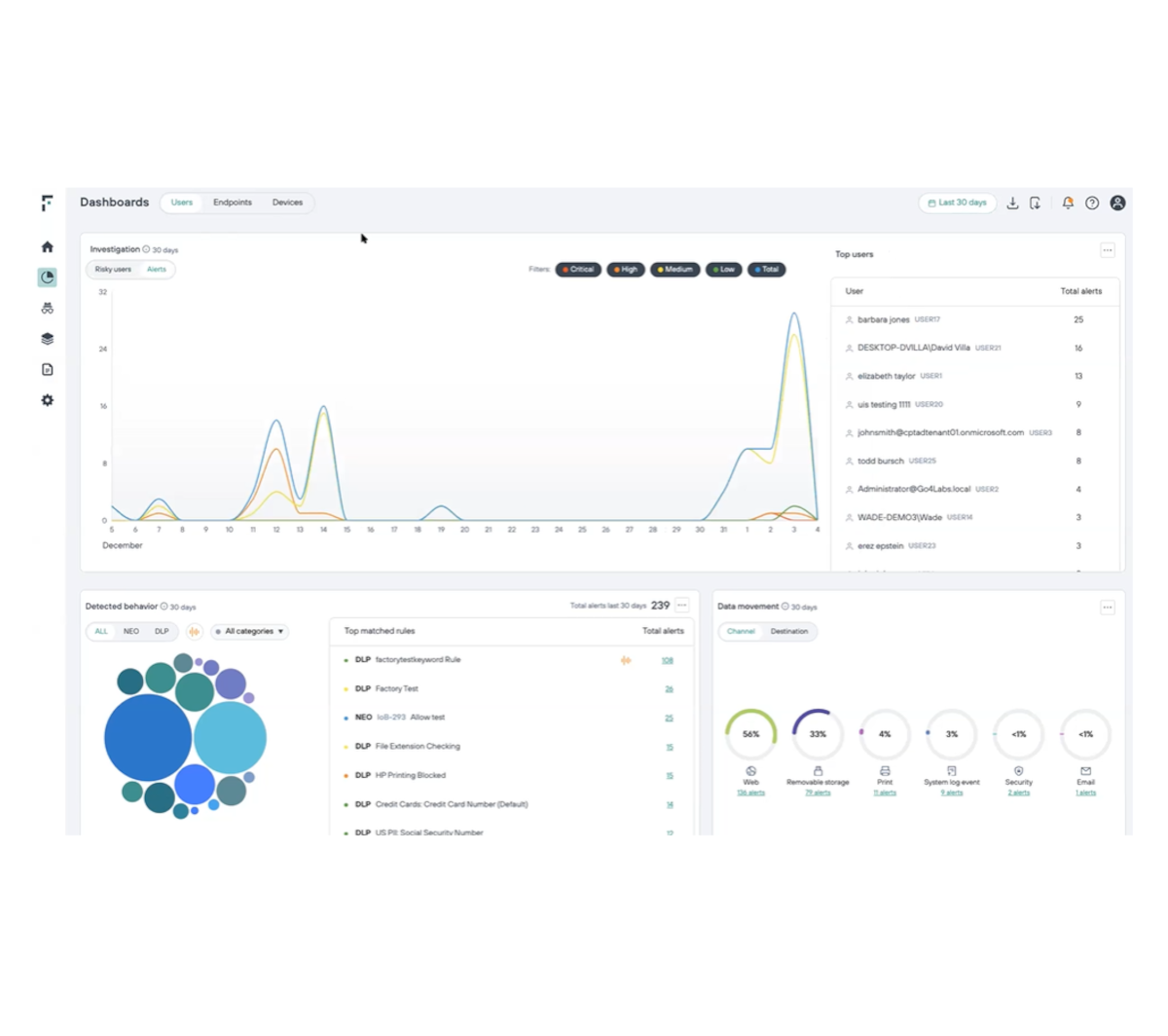
탐지의 최초 지점에서 내부자 위험 발견
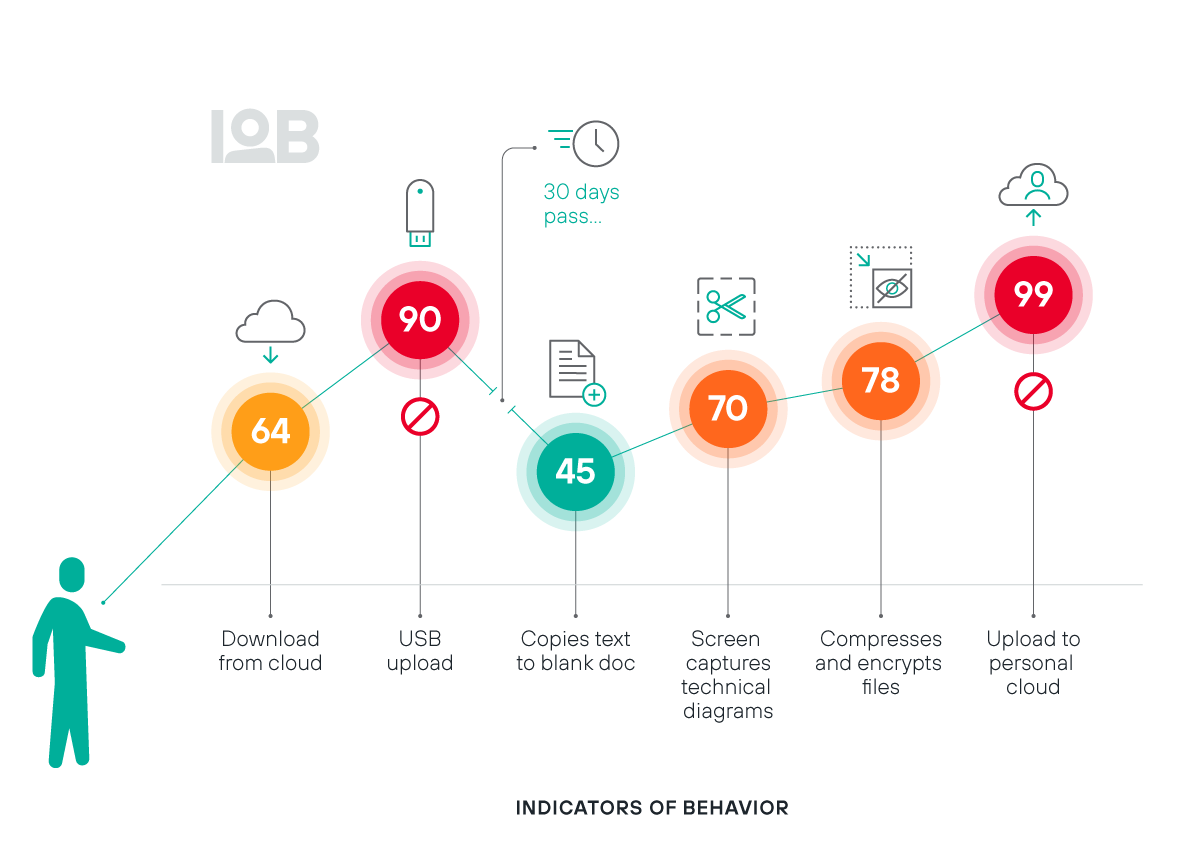
중요 데이터와 사용자의 상호 작용에 대해 실효적인 가시성 확보
위험한 사각 지대를 없애고 사용자가 주로 의심스럽게 행동하는 시점을 완벽하게 조사합니다.
항상 최신 위험 점수로 평가하면서 사용자 행동 및 의도를 파악합니다.
100개 이상의 행동 지표(IOB)와 관련하여 광범위한 모니터링 기능을 실행시킵니다.
DATASHEET
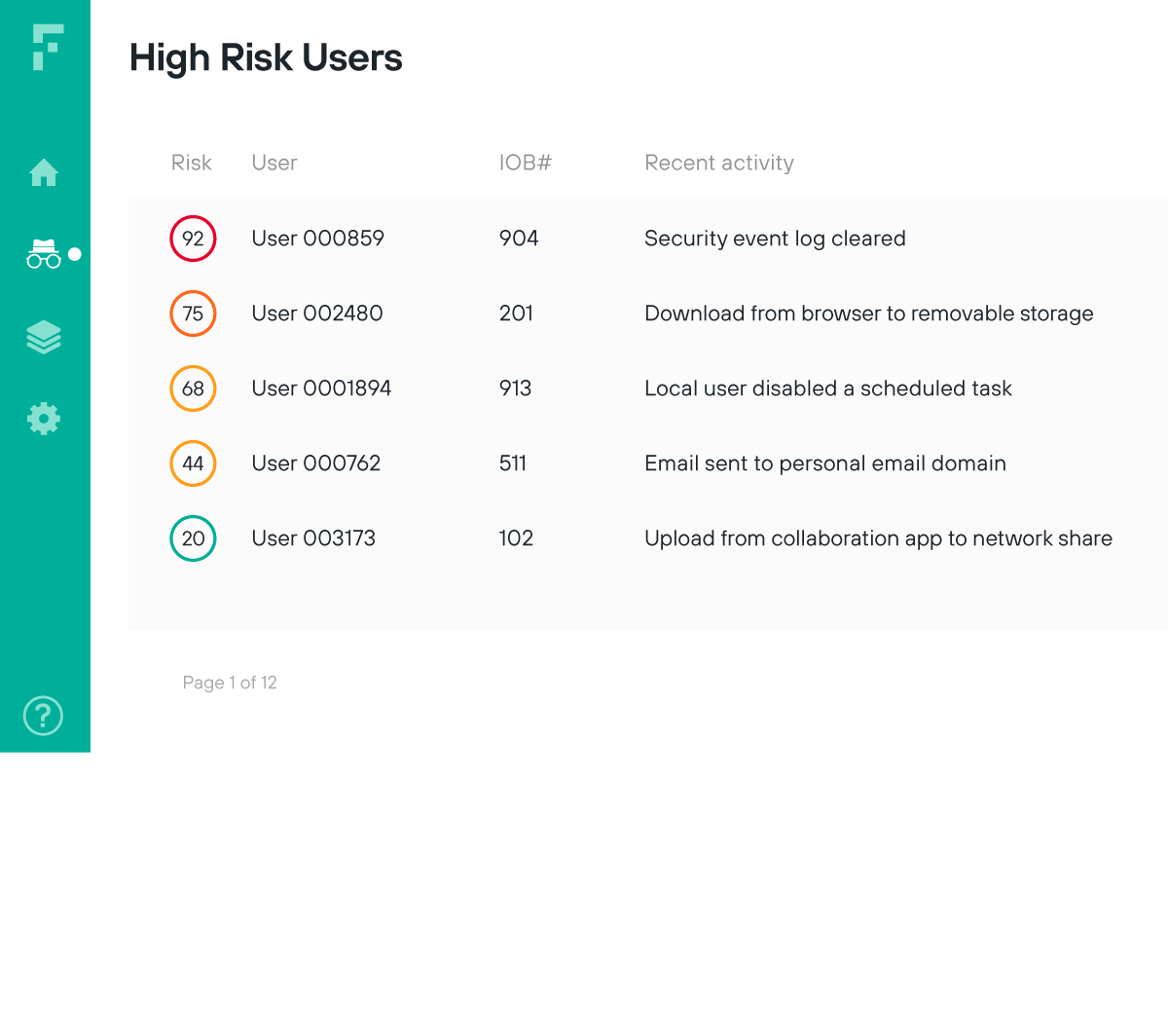
지속적인 사용자 검증으로 제로 트러스트 모델 구현
보안에 대한 진정한 제로 트러스트 접근 방식을 위해 제재된 사용자의 위험을 드러내고 최초 탐지 지점에서 비정상적인 행동을 분석가에게 경고합니다.
침해를 의미할 수 있는 비정상적인 사용자 활동을 토대로 액세스를 제한합니다.
사용자와 데이터의 상호 작용을 실시간으로 계속 모니터링하여 사용자 위험성을 검증합니다.
INFOGRAPHIC
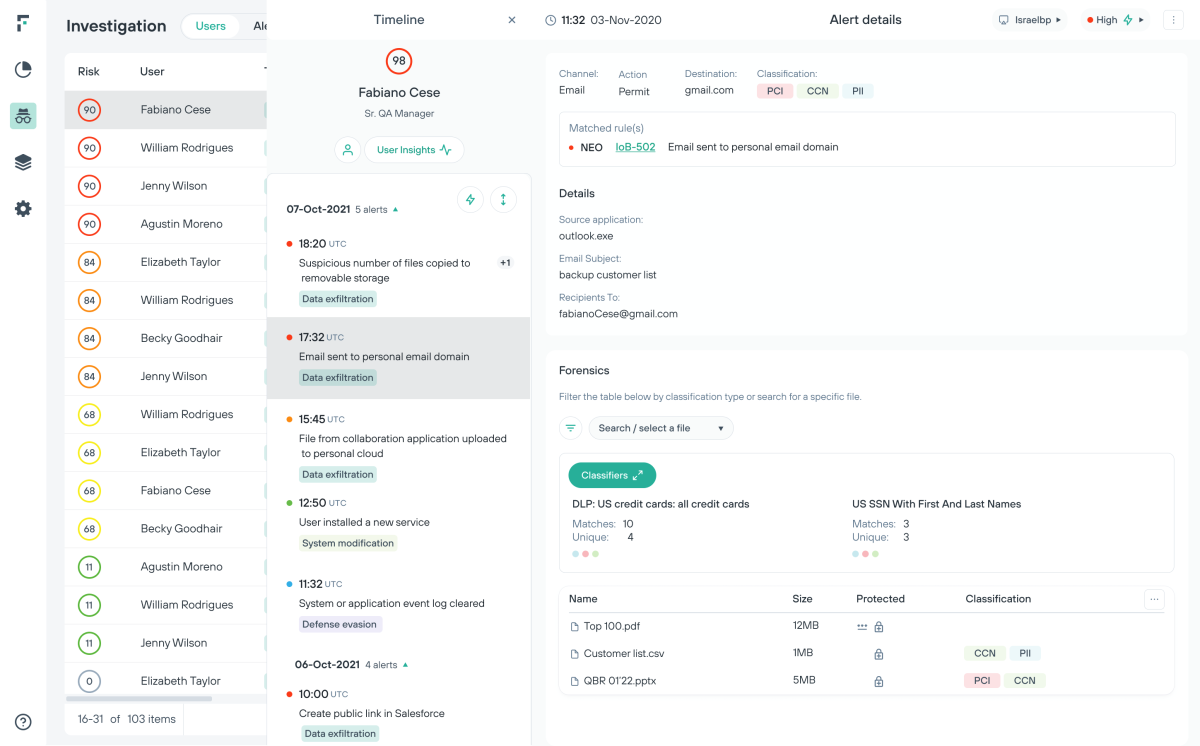
보안 분석가 효율성 극대화 및 경보 피로 감소
리스크 적응형 보안은 조직의 데이터 보안을 이벤트 중심에서 위험 중심적 접근 방식으로 전환합니다.
사용자 수준에 따라 정책 조정을 최적화하면서 데이터 유출 이벤트를 선제적으로 대비합니다.
조사 효율성을 확보하고 학습 능력을 향상시킵니다.
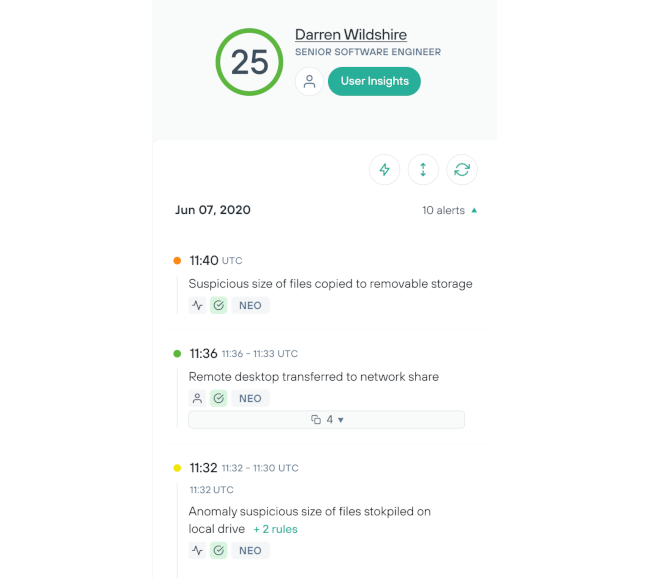
내부자 위험을 효율적으로 간편하게 조사합니다.
원활한 구현 과정과 개별 자동화를 통해 수동 터치포인트의 필요성을 줄입니다.
자동화 및 오탐지 축소를 통해 사용자를 조사할 수 있는 분석가의 역량을 증대시킵니다.
클라우드에서 쉽게 유지 관리되는 인프라와 30초 에이전트 배포를 통해 직원의 업무 부담을 줄입니다.
새롭게 등장하는 위협에 실시간으로 대응
보안 정책을 자동으로 조정하여 위험한 사용자 행동을 차단하여 데이터 유출을 방지합니다.
허위 긍정적 경고를 줄이고 사고 발생에 소요되는 시간을 되찾을 수 있습니다.
위험 요소가 적은 사용자가 필요한 정보를 액세스할 수 있도록 지원하면서 잠재적인 위협을 차단합니다.
사용자 활동에 대한 지속적인 모니터링을 통해 실시간으로 데이터 보안을 자동화합니다.


데이터 손실 방지를 위한 실용적인 경영진 가이드
실무 가이드를 통해 Data Loss Prevention (DLP) 소프트웨어를 모든 규모의 기업에 구현하기 위한 8가지 테스트된 검증된 단계를 알아보세요.
분석가를 추천합니다.
사용자가 승인했습니다.
Forcepoint는 사용자와 업계 분석가들이 선정한 최고의 Data Loss Prevention 소프트웨어 및 데이터 보안 소프트웨어 공급업체 중 하나로 꾸준히 선정되었습니다.
Forcepoint가 IDC MarketScape: Worldwide DLP 2025 Vendor Assessment에서 리더로 선정되었습니다.
Forcepoint가 Frost & Sullivan에서 선정한 2024년 글로벌 DLP 올해의 기업 으로 2년 연속 선정되었습니다.
Forcepoint가 2025년 1분기 The Forrester Wave™: Data Security Platforms에서 우수 성과 를 거두는 기업으로 선정되었습니다.'
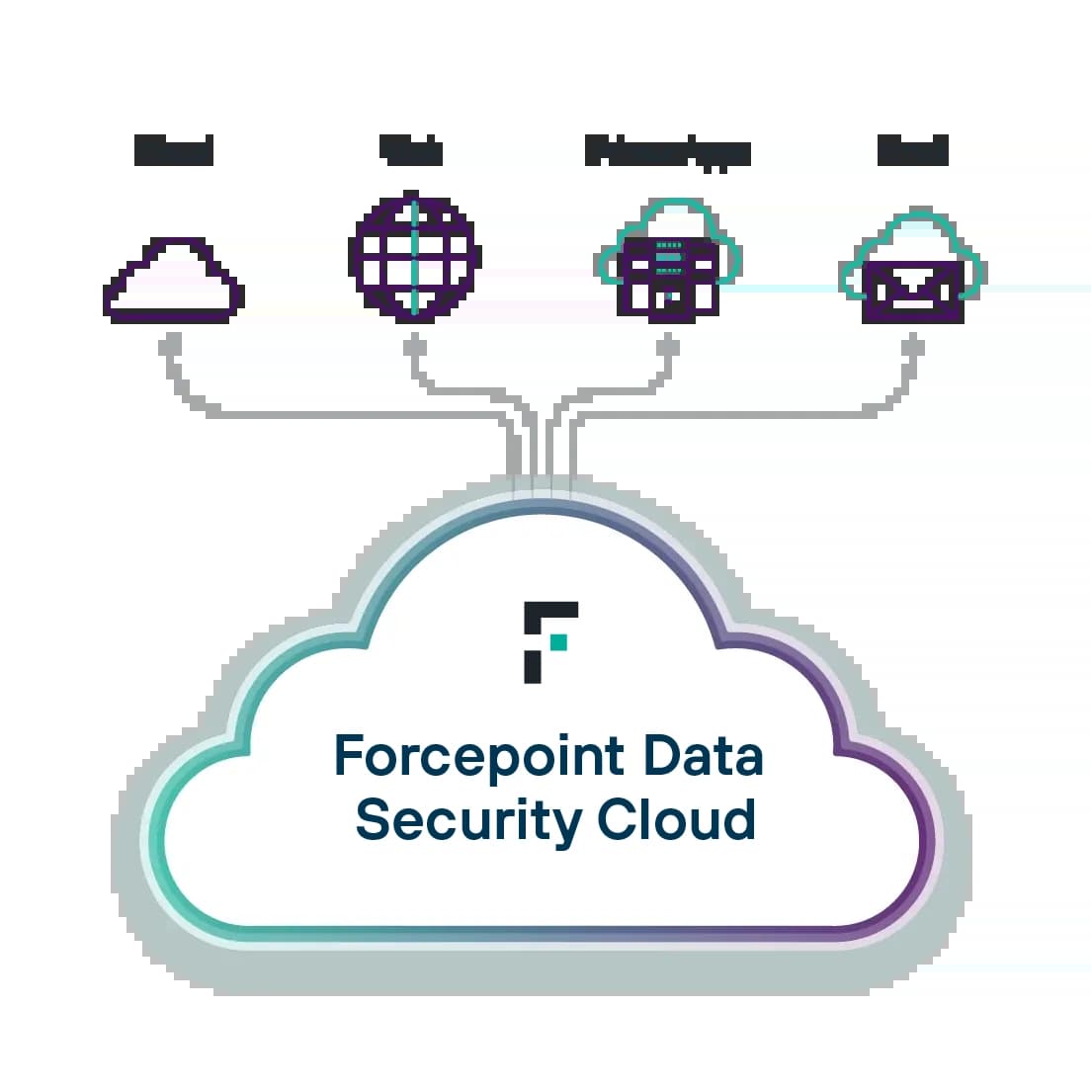
차세대 데이터 보안
Forcepoint를 사용하여 어디에서나 데이터를 보호하세요. AI를 활용해 데이터 검색 및 분류를 강화하고 정책 관리를 통합하고 실시간으로 위험에 대응하여, 데이터 유출을 방지하고 규정 준수를 간소화할 수 있습니다.
Enterprise DLP: 사용하기 쉬운 중앙 집중식 플랫폼에서 데이터 보호 정책을 수립, 확장, 자동화합니다.
Forcepoint Data Visibility: 조직 전반의 비정형 데이터를 한눈에 파악할 수 있습니다.
Data Classification: 인공지능과 ML을 활용하여 데이터 분류의 정확성과 효율성을 높일 수 있습니다.
Risk Adaptive Protection 의 최고 실무 읽기


