Mais de 12 mil clientes não poderiam estar errados










































Identifique o risco de usuários internos no primeiro ponto de detecção

Obtenha visibilidade significativa sobre as interações de usuários com dados críticos
Elimine pontos cegos perigosos e habilite uma visão completa de quando os usuários apresentam tendência a comportamentos arriscados
Entenda os comportamentos e a intenção dos usuários com pontuações de riscos sempre atualizadas
Desbloqueie recursos abrangentes de monitoramento em mais de 100 Indicadores de Comportamentos (IOBs)
DATASHEET
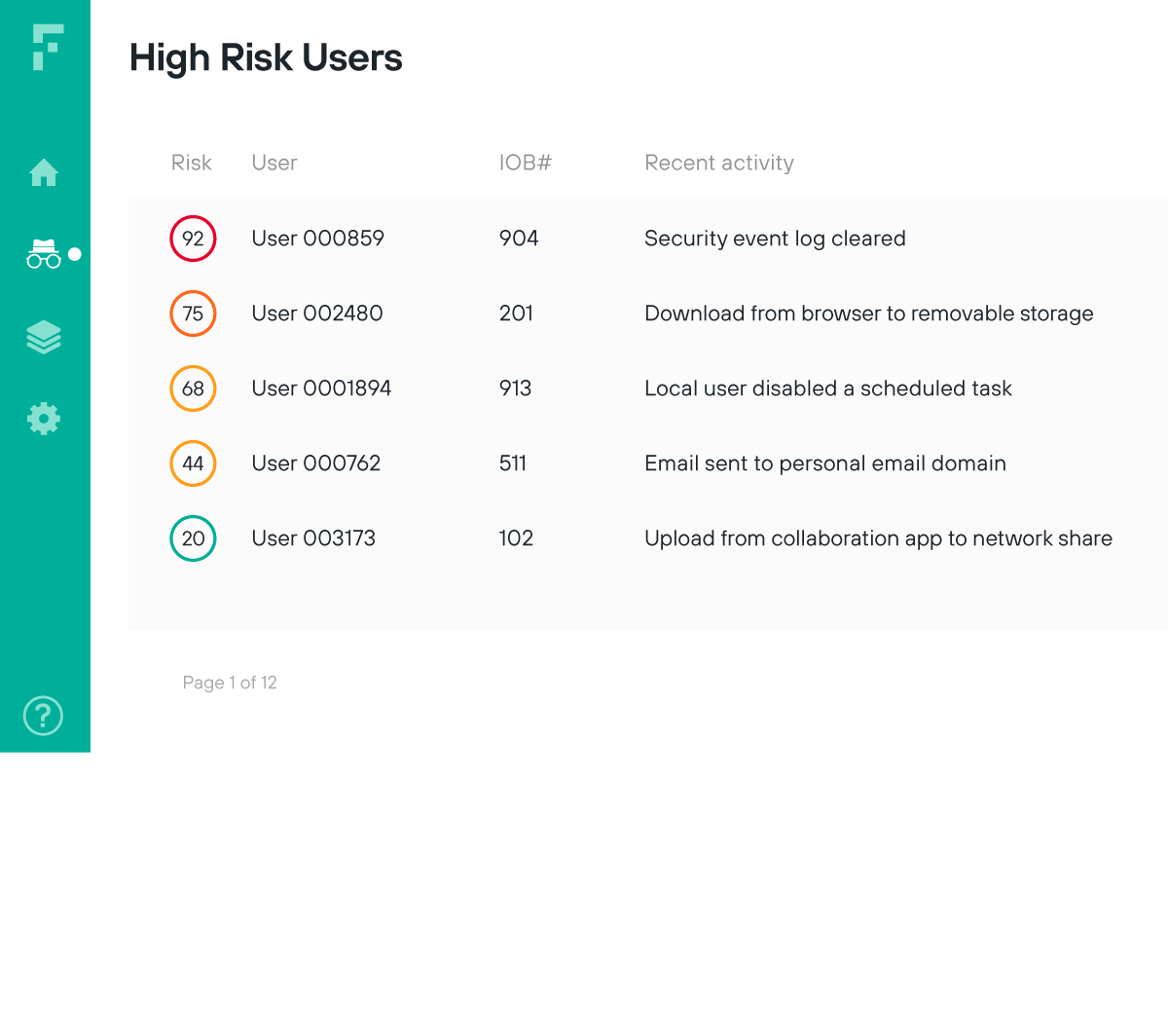
Implemente um modelo de Zero Trust com validação contínua de usuários
Identifique o risco de usuários aprovados e alerte os analistas sobre comportamentos incomuns no primeiro ponto de detecção para uma verdadeira abordagem de Zero Trust para a segurança
Limite o acesso com base em atividades incomuns de usuários que poderiam indicar comprometimento
Valide o risco com monitoramento em tempo real de interação constante de usuários e dados
INFOGRAPHIC
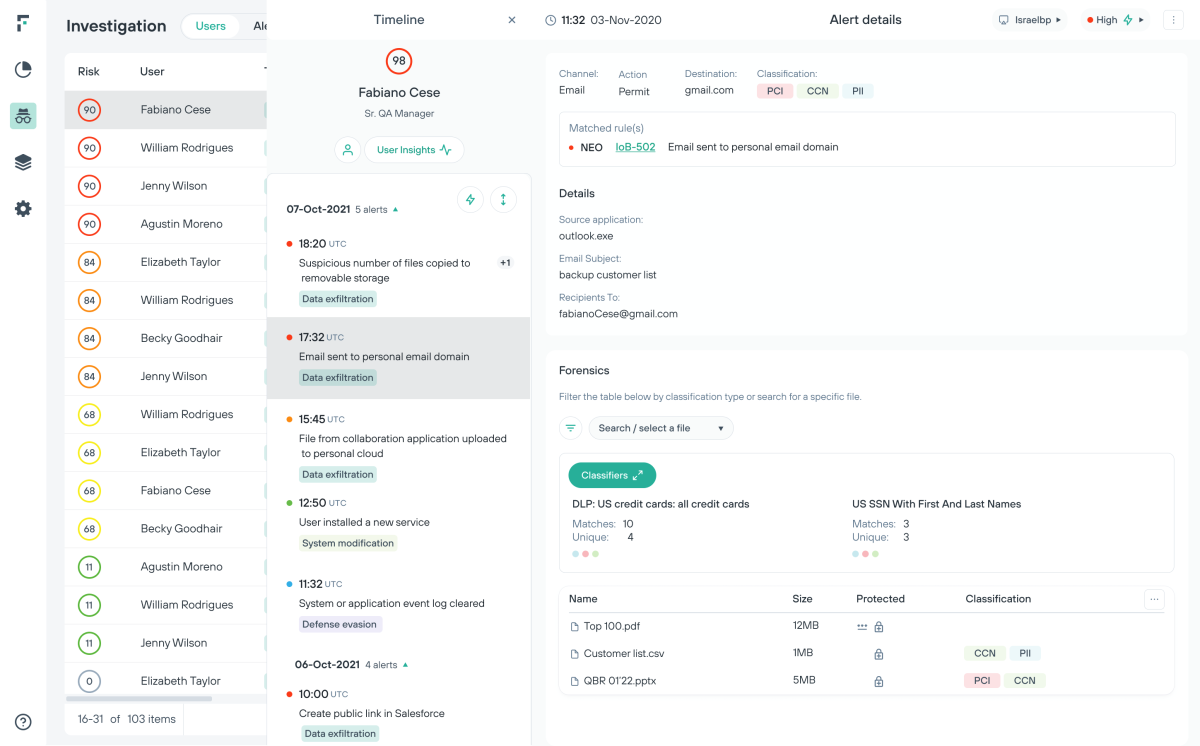
Maximize a eficiência dos analistas de segurança e reduza a fadiga de alertas
A Proteção Adaptável ao Risco desloca as organizações de uma abordagem centrada em eventos para uma abordagem centrada em riscos para a segurança dos dados.
Fique à frente do evento de exfiltração com planejamento de ajustes de políticas em nível do usuário
Obtenha eficiência de investigação e aumente a capacidade de aprendizagem
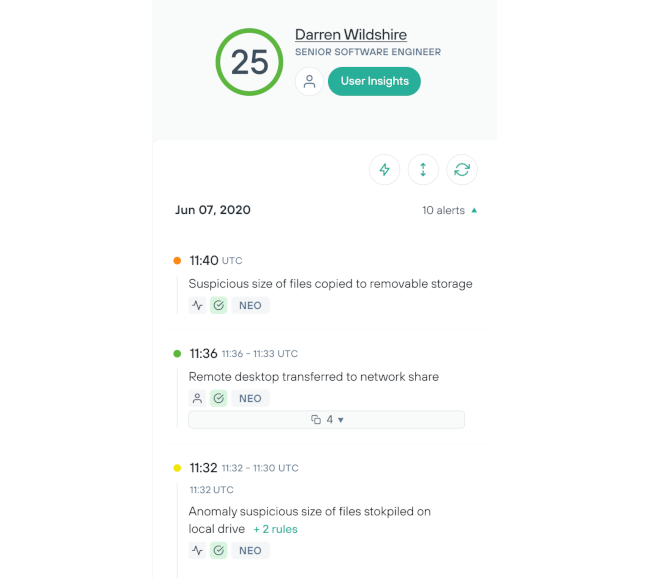
Investigue o risco de usuários internos com eficiência e facilidade
Reduza a necessidade de touchpoints manuais com um processo de implementação sem atrito e automação personalizada.
Amplie a capacidade dos analistas para investigar usuários com automação e eliminação de falsos positivos
Libere a sua equipe com uma infraestrutura na nuvem com manutenção fácil e implementação com um agente em 30 segundos
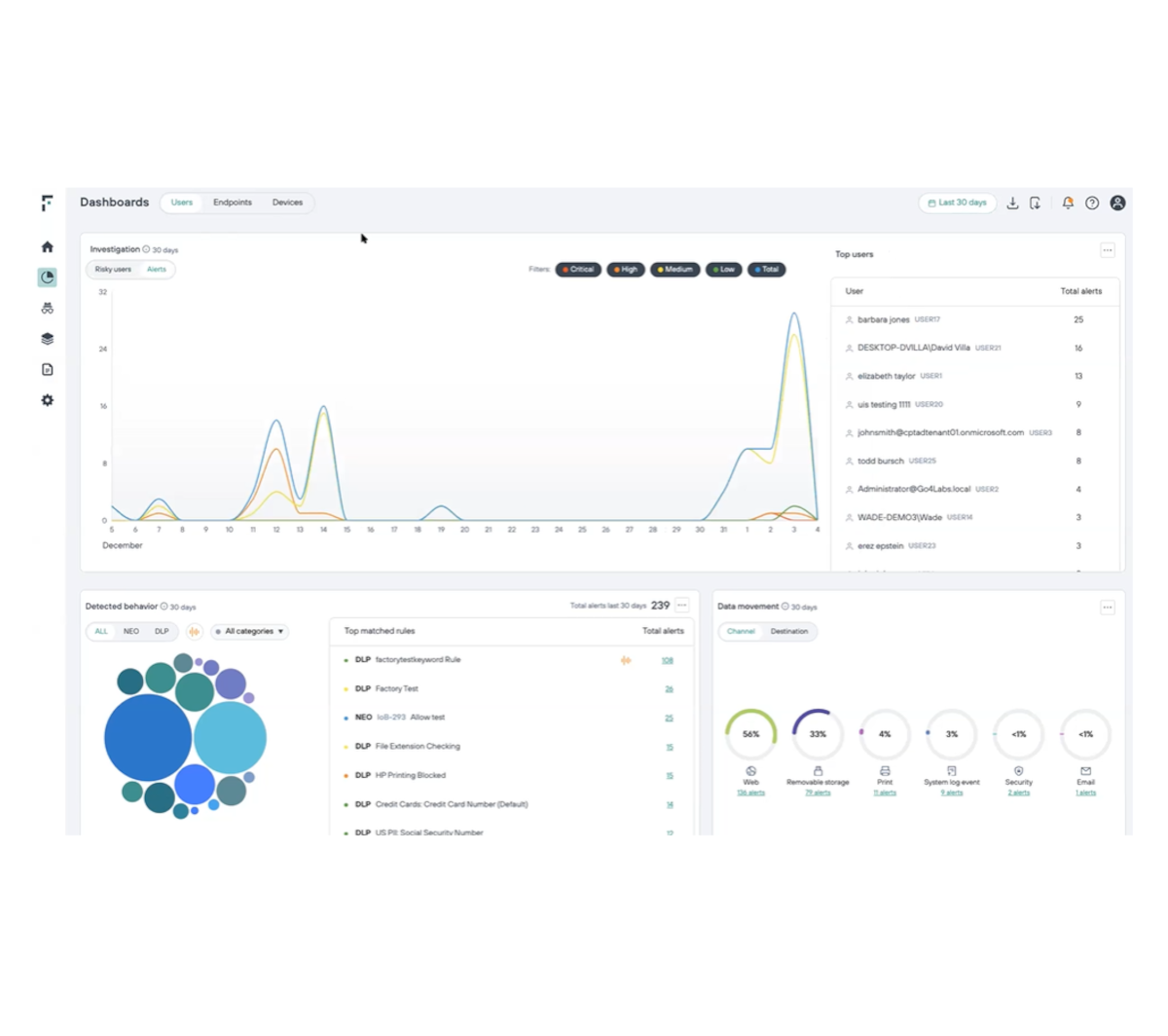
Responda a ameaças que surgem em tempo real
Evite a extração de dados adaptando automaticamente suas políticas de segurança para bloquear comportamentos de risco dos usuários.
Reduza alertas de falsos positivos e economize tempo na análise de incidentes.
Permita que usuários de baixo risco acessem as informações de que precisam, mantendo distância de possíveis ameaças.
Automatize a segurança de dados em tempo real por meio do monitoramento contínuo da atividade dos usuários.


Guia Prático do Executivo para Data Loss Prevention
Descubra os oito passos testados e comprovados para implementar o software Data Loss Prevention (DLP) em empresas de qualquer porte com nosso guia prático.
Recomendada por especialistas.
Aprovada pelos usuários.
A Forcepoint é consistentemente classificada entre os principais fornecedores de software de prevenção contra perda de dados e software de segurança de dados por usuários e analistas do setor.
Forcepoint has been named a Leader in the IDC MarketScape: Worldwide DLP 2025 Vendor Assessment.
A Forcepoint foi nomeada a Empresa Global do Ano de DLP em 2024 pelo segundo ano consecutivo pela Frost & Sullivan.
Forcepoint reconhecida como Strong Performer no relatório The Forrester Wave™: Data Security Platforms, Q1/2025.
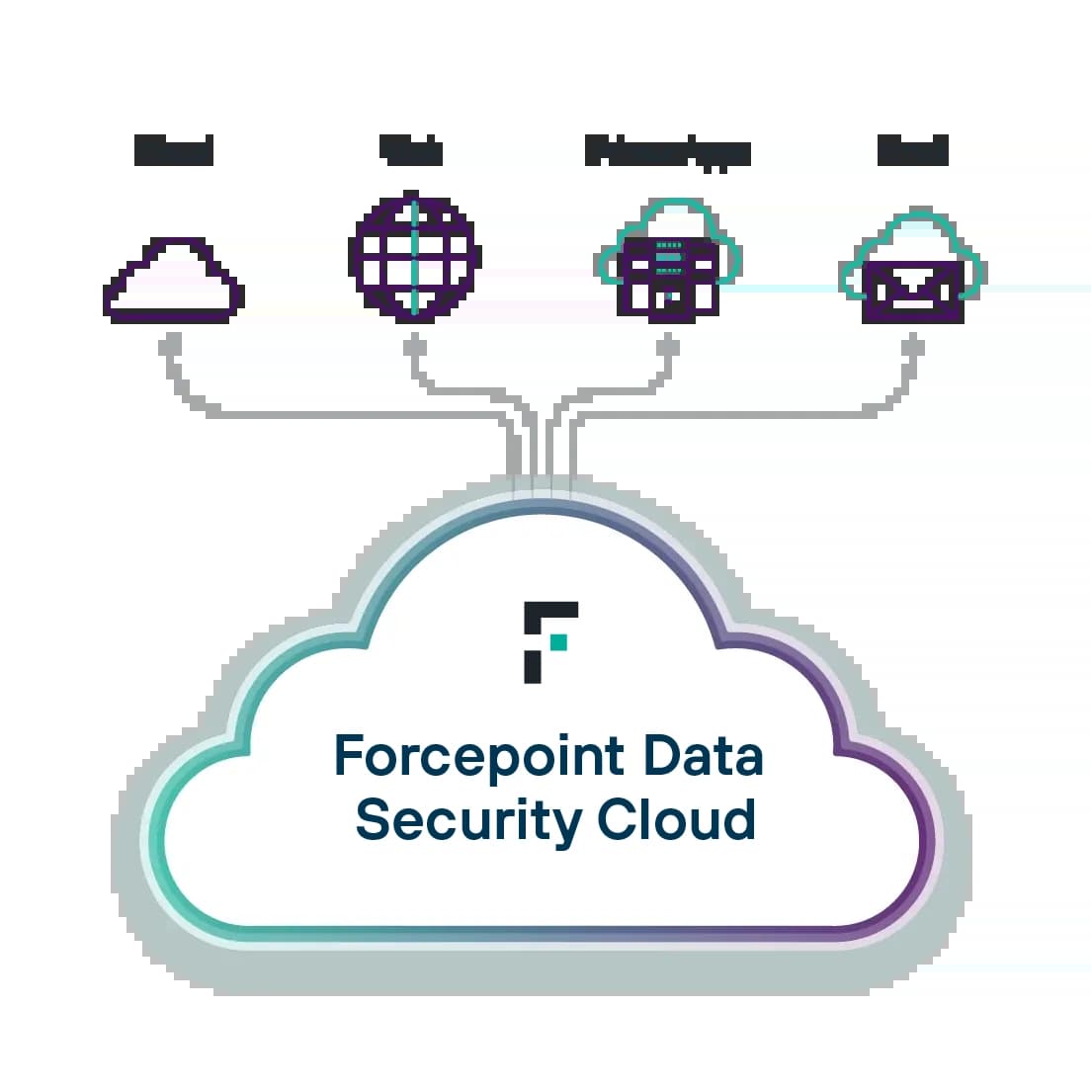
A Próxima Geração da Segurança de Dados
Proteja dados em todos os lugares com o Forcepoint. Evite violações e simplifique a conformidade usando IA para impulsionar a descoberta e a classificação de dados, unificando o gerenciamento de políticas e adaptando-se a riscos em tempo real.
Enterprise DLP : Defina, dimensione e automatize as políticas de proteção de dados a partir de uma plataforma centralizada e fácil de usar.
Forcepoint Data Visibility: Obtenha uma visão panorâmica dos dados não estruturados em toda a sua organização.
Data Classification: Desenvolva maior precisão e eficiência na classificação de dados com a ajuda de IA e ML.
RECURSOS DE RISK ADAPTIVE PROTECTION
Leia sobre as melhores práticas do Risk Adaptive Protection

Data Security Everywhere - Automate Data Security Management with Risk-Adaptive Protection
Assistir ao VídeoCompetitive DLP Risk-Adaptive Protection Feature Comparison
Ver a Ficha TécnicaRisk-Adaptive Protection: Personalized Automation Solution for Forcepoint DLP
Ler o Resumo da Solução

