12K+ müşteri yanılıyor olamaz










































Şirket içindeki riski en erken tespit noktasında ortaya çıkarın
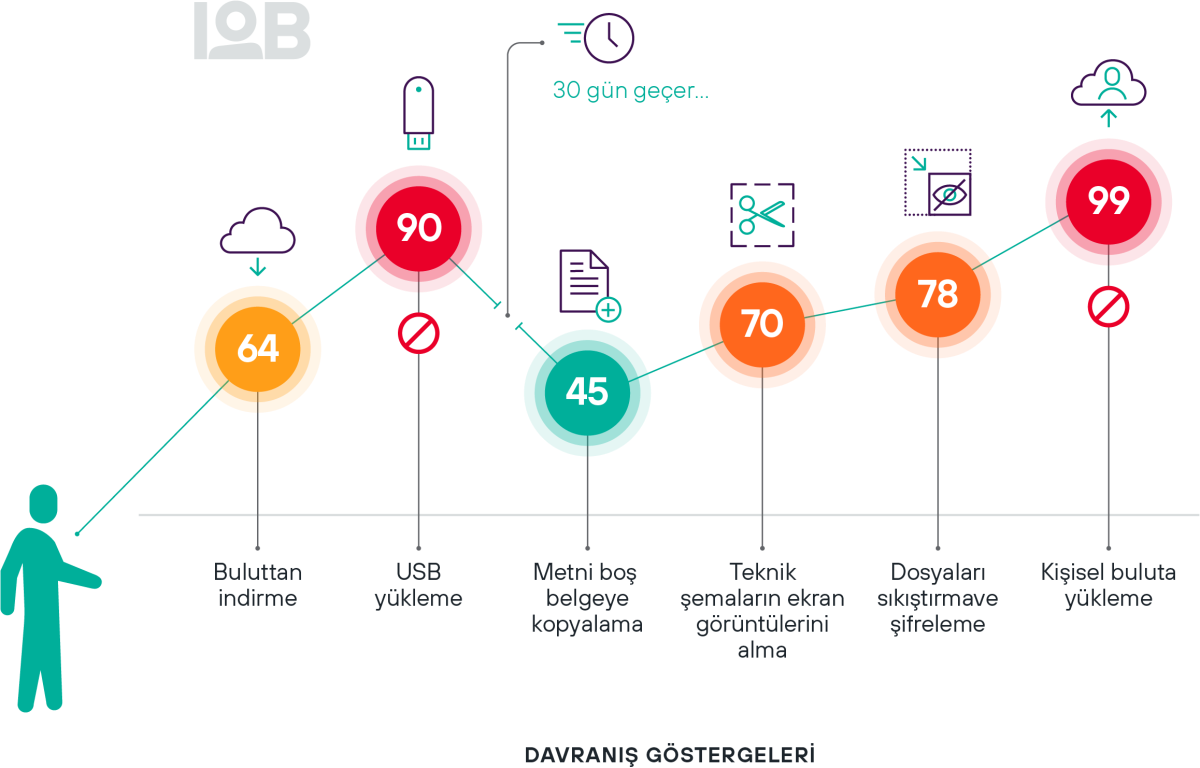
Kullanıcıların kritik verilerle etkileşimlerini daha iyi görün
Tehlikeli kör noktaları ortadan kaldırın ve kullanıcıların riskli davranışa yöneldiği zamanları net olarak öngörün
Her zaman güncel risk puanlaması ile kullanıcı davranışlarını ve niyetini anlayın
100+ Davranış Göstergesi (IOB) sayesinde geniş kapsamlı izleme kabiliyeti kazanın
DATASHEET
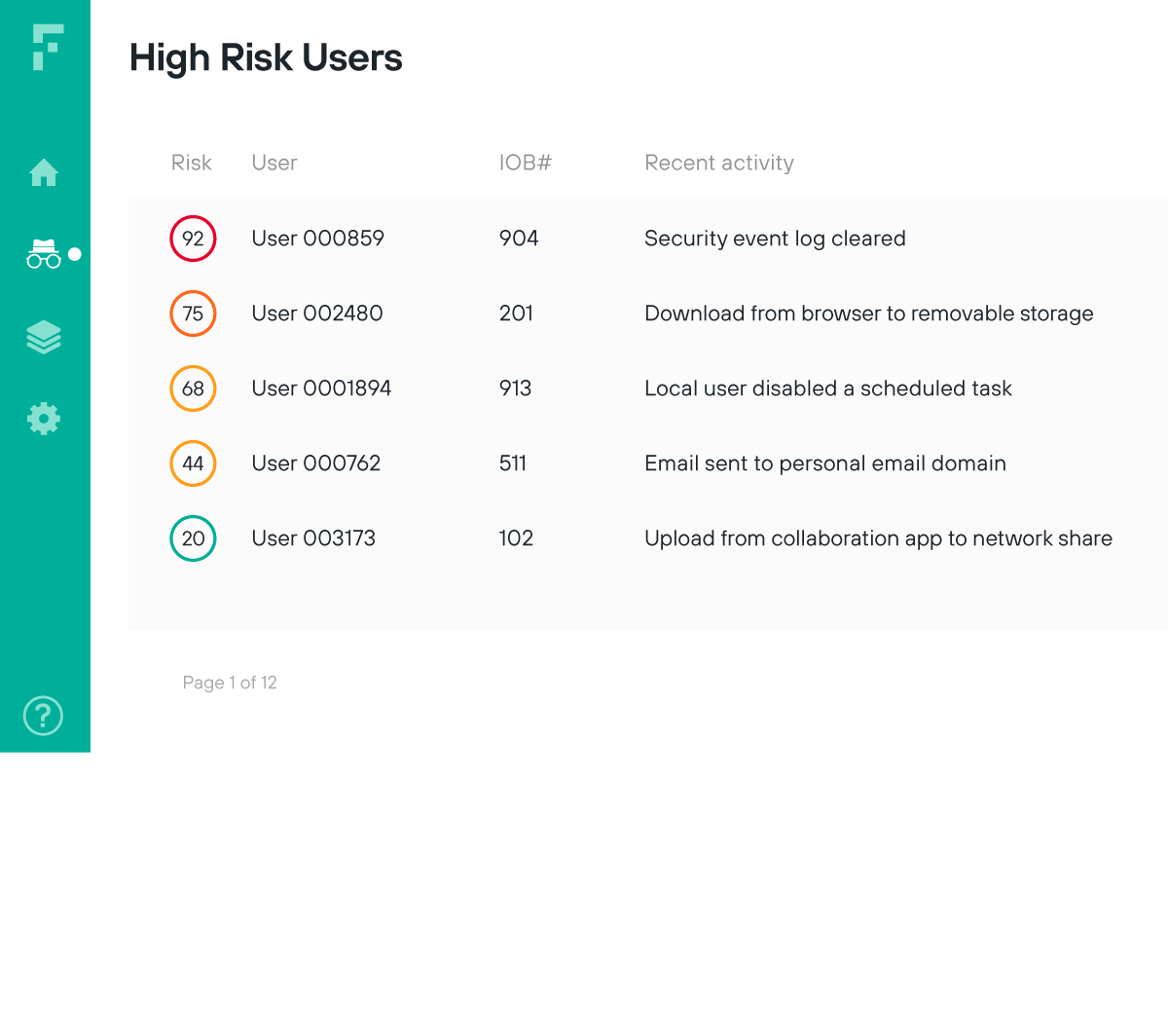
Sürekli kullanıcı doğrulamasını öngören Zero Trust modelini uygulayın
Güvenlik konusunda tam anlamıyla Zero Trust yaklaşımı sergilemek için yasaklı kullanıcılardan kaynaklanan riskleri ortaya çıkarın ve sıra dışı davranışlar konusunda analistlere en erken tespit noktasında bilgi verin
Gizliliğin ihlalini gösterebilecek sıra dışı kullanıcı faaliyetlerine dayanarak erişimi sınırlandırın
Devam eden kullanıcı ve veri etkileşimini gerçek zamanlı olarak izleyerek kullanıcı riskini doğrulayın
INFOGRAPHIC
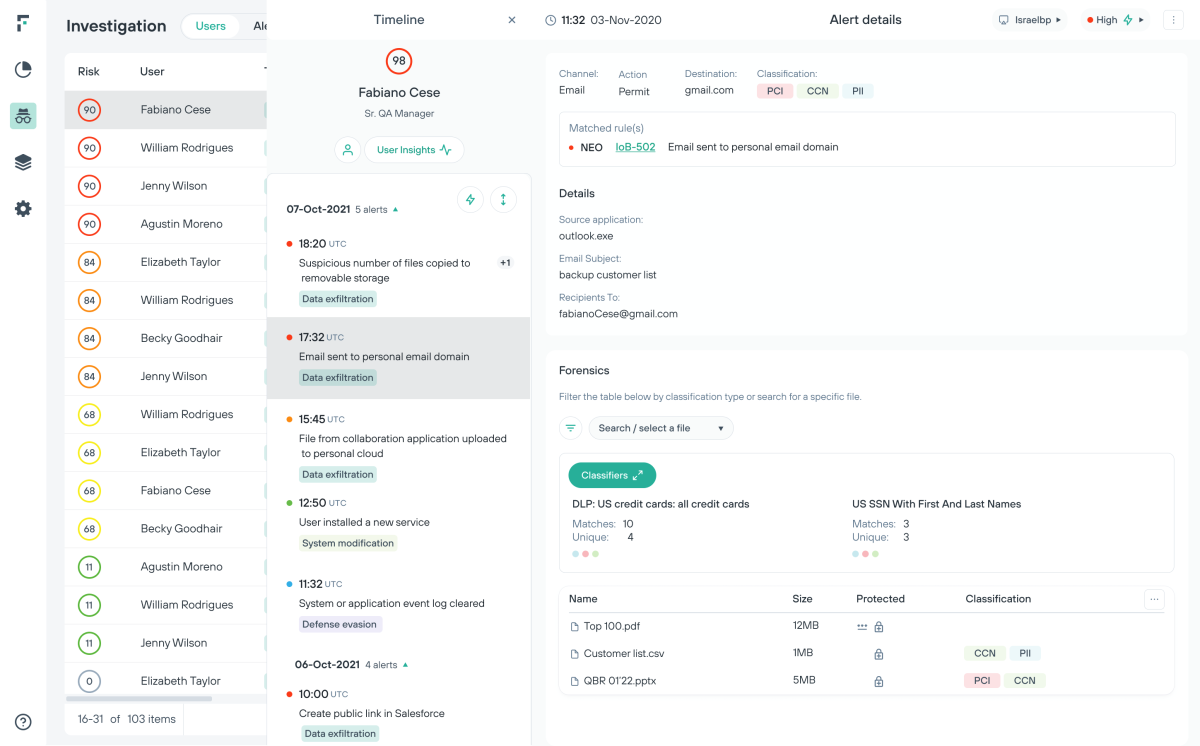
Güvenlik analisti verimliliğini artırın ve uyarı yorgunluğunu azaltın
Risk-Adaptive Protection, kuruluşların veri koruması konusunda olay merkezli bir yaklaşımdan risk odaklı bir yaklaşıma geçmesini sağlar.
Kullanıcı düzeyindeki politika düzenlemelerinin yönetilmesi yoluyla veri sızdırma olaylarının önüne geçin
İncelemelerde etkinlik sağlayın ve öğrenme kapasitesini artırın
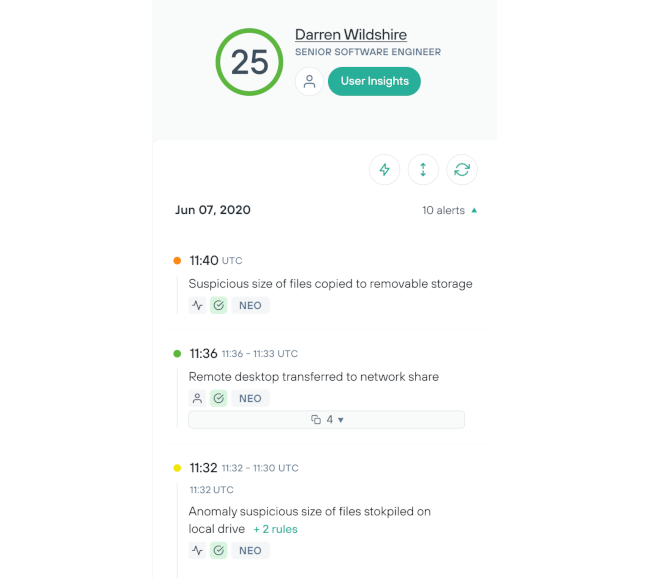
Şirket içinden kaynaklanan riski etkili ve kolay bir şekilde soruşturun
Sorunsuz bir uygulama süreci ve kişiselleştirilmiş otomasyon sayesinde manuel temas noktası ihtiyacını azaltın.
Otomasyon sağlayarak ve hatalı pozitifleri ortadan kaldırarak analistlerin kullanıcıları soruşturma kapasitesini artırın
Bulutta kolayca saklanabilen altyapı ve 30 saniyede aracı kurulumu sayesinde personelinizi verimli çalıştırın
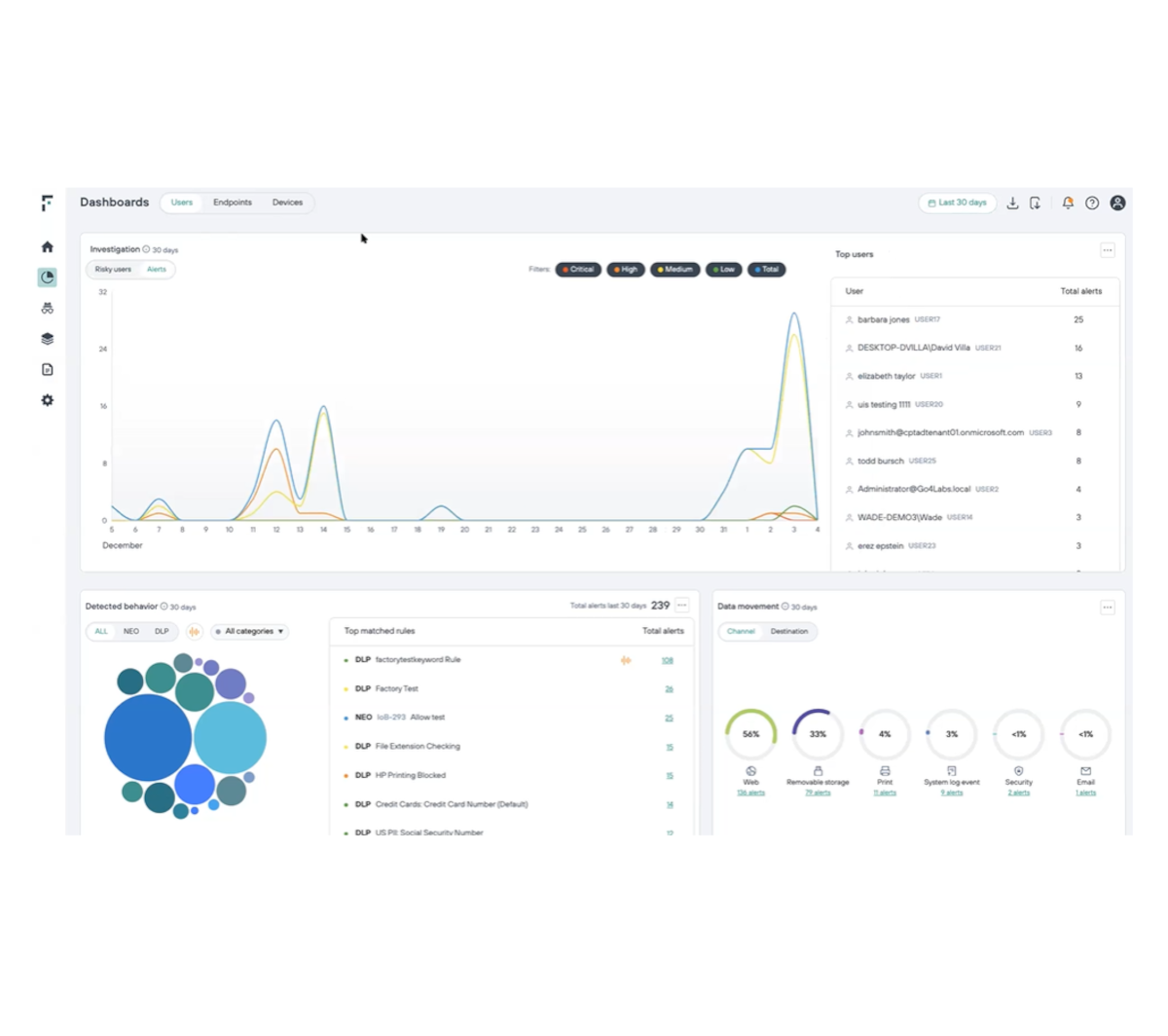
Ortaya çıkan tehditlere gerçek zamanlı olarak yanıt verin
Güvenlik politikalarınızı riskli kullanıcı davranışlarını engelleyecek şekilde otomatik olarak uyarlayarak veri sızıntılarını önleyin.
Sahte pozitif uyarıları azaltın ve olay analizi için harcanan zamanı geri kazanın.
Potansiyel tehditleri uzak tutarken düşük riskli kullanıcıların ihtiyaç duydukları bilgilere erişmelerine olanak tanıyın.
Kullanıcı faaliyetlerinin sürekli izlenmesi yoluyla veri güvenliğini gerçek zamanlı olarak otomatikleştirin.


Veri Kaybını Önlemeye Yönelik Pratik Yönetici Kılavuzu
Uygulamalı kılavuzumuzla her ölçekteki işletme için Data Loss Prevention (DLP) yazılımını uygulamaya yönelik denenmiş ve uygulanmış sekiz adımı keşfedin.
Analiz Uzmanları Tarafından Önerildi.
Kullanıcı onaylı.
Forcepoint, kullanıcılar ve sektörel analistler tarafından sürekli en iyi Veri Kaybı Önleme yazılımı ve veri güvenliği yazılımı sağlayıcıları arasında gösterilmektedir.
Forcepoint, IDC MarketScape: Worldwide DLP 2025 Vendor Assessment'ta Lider olarak gösterildi.
Forcepoint, Frost & Sullivan tarafından üst üste ikinci kez 2024 Global DLP Company of the Year ödülüne layık görüldü.
Forcepoint, The Forrester Wave™: Data Security Platforms, 1. Çeyrek 2025'te Güçlü Performans Gösteren olarak öne çıktı.
Yeni Nesil Veri Güvenliği
Forcepoint ile verileri her yerde güvence altına alın. Veri keşfini ve sınıflandırmasını güçlendirmek, politika yönetimini birleştirmek ve risklere gerçek zamanlı olarak adapte etmek için yapay zeka kullanarak ihlalleri önleyin ve uyumluluğu basitleştirin.
Enterprise DLP: Veri koruma politikalarını merkezi, kullanımı kolay bir platformdan belirleyin, ölçeklendirin ve otomatikleştirin.
Forcepoint Data Visibility: Kurumunuzdaki yapılandırılmamış verileri panoramik bir şekilde görüntüleyin.
Data Classification: Yapay Zeka ve Makine Öğrenimi yardımıyla verileri sınıflandırmada daha fazla doğruluk ve verimlilik elde edin.
RISK ADAPTIVE PROTECTION KAYNAKLARI
Risk Adaptive Protection En İyi Uygulamalarını Okuyun

Data Security Everywhere - Automate Data Security Management with Risk-Adaptive Protection
Videoyu İzleCompetitive DLP Risk-Adaptive Protection Feature Comparison
Veri Sayfalarını GörüntüleRisk-Adaptive Protection: Personalized Automation Solution for Forcepoint DLP
Çözüm Özetini Oku

