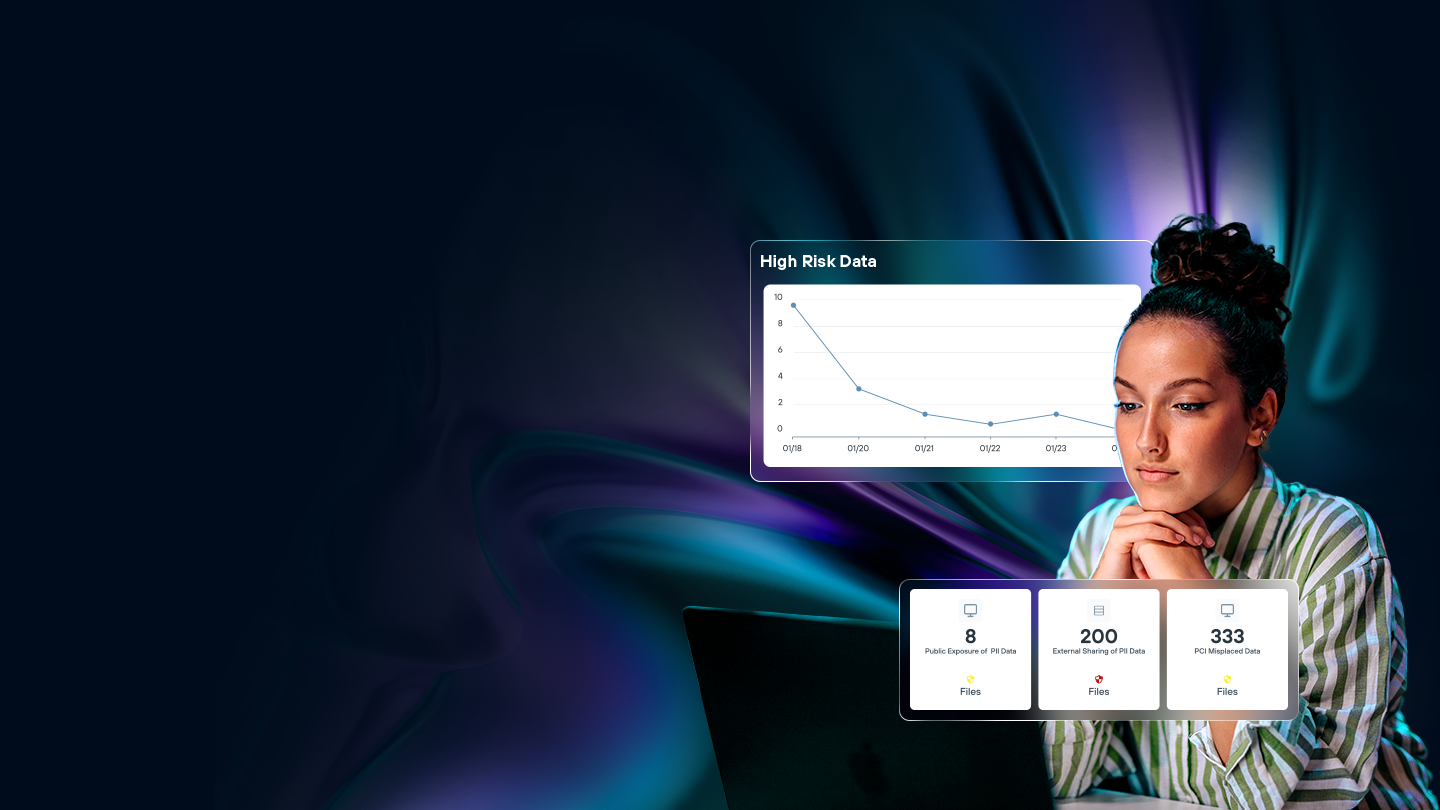
Más de 12.000 clientes no podían equivocarse










































La defensa del perímetro no es suficiente. Proteja los datos en todas partes con precisión de punta.
Nuestro software de Data Detection & Response (DDR) utiliza clasificación impulsada por IA y monitoreo continuo para la detección y prevención dinámicas de la exfiltración de datos. No se limite a identificar riesgos; prioriza y acelera la remediación.
Forcepoint DDR es perfecto para ayudar a las empresas a:
Detectar y responder a fugas de datos y amenazas internas potenciales
Proteger dinámicamente los datos confidenciales en uso
Obtener visibilidad amplia en las nubes y endpoints
Ahorrar dinero a través de la prevención de fugas


Explore Forcepoint DDR
Vea nuestro software de Data Detection & Response (DDR) en acción.Realice un recorrido por la plataforma y aprenda cómo protege datos estructurados y no estructurados.
¿Por qué usar una solución de Data Detection and Response?
Clasifique con confianza
Mejore el contexto de los datos mediante el uso de AI Mesh para comprender su relevancia y confidencialidad únicas.
Detecte amenazas temprano
Reduzca el tiempo medio de detección con el monitoreo continuo del intercambio de archivos, el cambio de nombres y el movimiento.
Cubra el endpoint y la nube
Amplíe la visibilidad y la aplicación a la nube y el endpoint para una cobertura amplia.
Limite los alertas de falsos positivos
Priorice las alertas según la gravedad para mejorar el tiempo promedio a la respuesta.


¿Están sus datos en riesgo?
Data Risk Assessment descubre proactivamente las amenazas para sus datos, ya sean archivos confidenciales no clasificados o usuarios con permisos excesivos. Solicite un Data Risk Assessment gratuita con Forcepoint para ver DSPM en acción y conozca qué tan seguros están sus datos.


Vea el video
Punta la precisión y la elaboración de informes transparentes
Enda Kyne, CTOO de FBD Insurance, dice que DSPM y DDR han sido adoptados por sus equipos de seguridad de TI y protección de datos por su capacidad para controlar datos críticos e informar actividades a los reguladores.
¿Por qué Forcepoint Data Detection & Response?



Monitorea las actividades de datos 24/7 en todo su panorama digital. DDR realiza un seguimiento de los patrones de acceso a archivos, comportamientos de intercambio y movimientos de datos en tiempo real, y alerta a los equipos de seguridad sobre actividades que podrían señalar amenazas internas o intentos de compromiso antes de que los datos confidenciales salgan de su control.

El motor de clasificación que impulsa Forcepoint DDR utiliza nuestra tecnología de AI Mesh patentada para proporcionar una clasificación de alta precisión. AI Mesh utiliza una combinación de un modelo de lenguaje pequeño de GenAI, clasificadores de redes neuronales, IA predictiva y otros componentes de datos para mejorar la precisión.

Forcepoint DDR se puede configurar como un complemento de Forcepoint DSPM. Juntos, proporcionan identificación, clasificación y prevención de amenazas continuas, con una cobertura que se extiende a toda la organización.
Historias de nuestros clientes
Historias de nuestros clientes
Preguntas frecuentes
What are the business benefits of DDR?
Forcepoint DDR helps prevent costly data breaches by detecting real threats earlier and focusing teams on the highest-risk events, which reduces incident impact, investigation time, and overall security operations cost.
It also increases confidence in digital transformation – cloud adoption, remote work, and AI/GenAI use – by providing continuous visibility into sensitive data and clear reporting that supports executive, customer and regulatory requirements.
Why is DDR important?
Forcepoint Data Detection and Response (DDR) is important because it continuously monitors how sensitive data is actually used across endpoints and cloud environments so you can spot and stop indicators of a breach while they’re happening, not months later. Traditional controls often leave a “visibility gap” around data-in-use. DDR closes that gap with real-time monitoring, AI-powered classification and automated responses to suspicious activity. It combines context from data, user behavior and permissions to reduce attacker dwell time, mitigate insider threats and prevent data exfiltration.
How does DDR detect threats or risky behavior?
Forcepoint DDR detects threats by continuously analyzing data events such as reads, views, creations, permission changes, renaming and sharing activities. It rescans items when significant changes occur and evaluates for anomalies and policy violations that indicate misuse, insider threats, compromised accounts or emerging exfiltration patterns.
Forcepoint AI Mesh adds context to distinguish normal business use from risky actions, then generates prioritized alerts and recommended or automated remediation steps to help security teams respond before data leaves your control.
How fast can DDR detect data exfiltration attempts?
DDR is designed for continuous, near-real-time monitoring and alerting. It tracks file access, movement and sharing 24/7 and raises alerts as soon as relevant risky events are observed and evaluated.
¿Cómo ayuda DDR a las organizaciones a detener la pérdida de datos y abordar las vulnerabilidades?
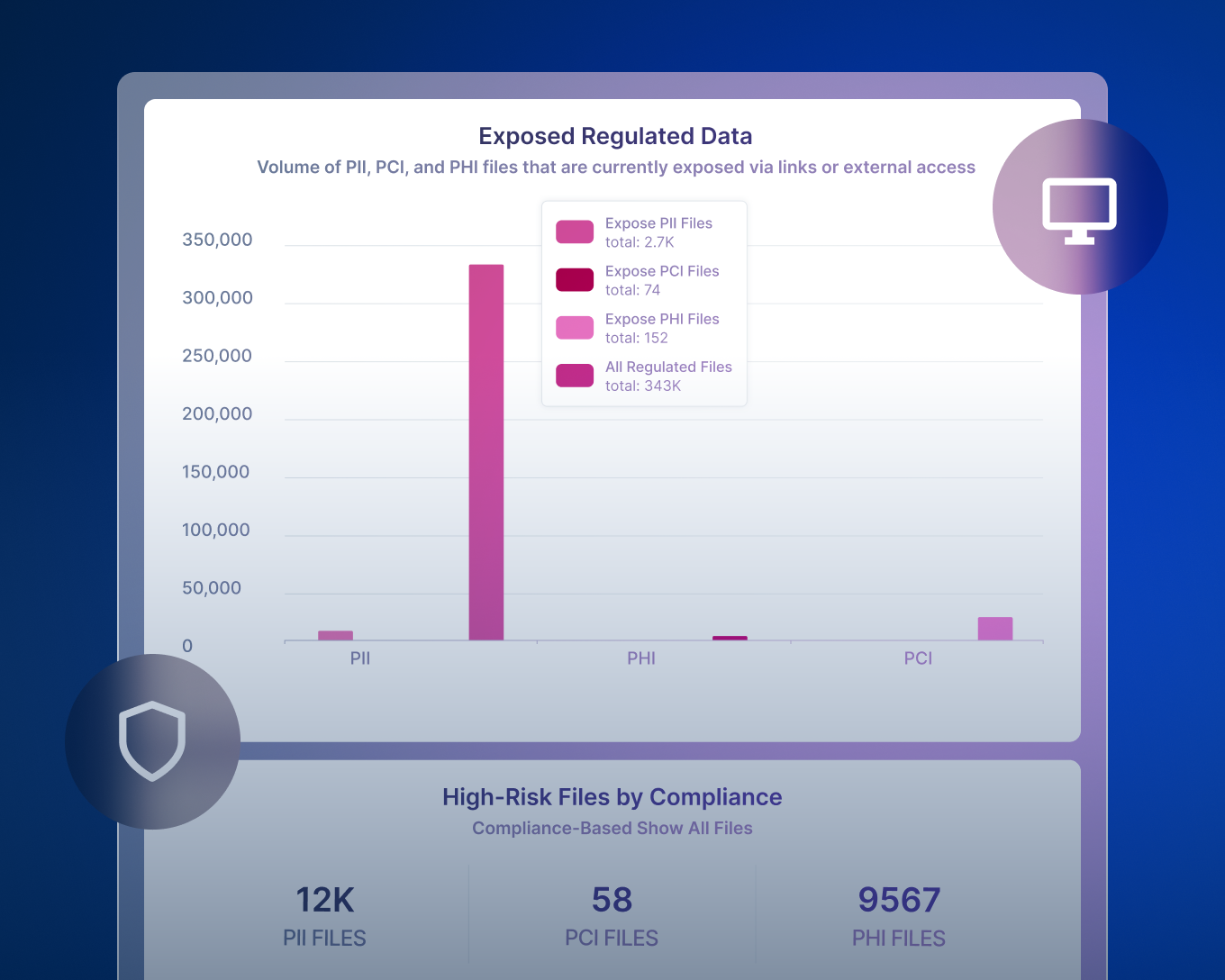
Forcepoint DDR admite plantillas predefinidas para detectar la exposición a datos confidenciales como PII, PCI y PHI. Estas plantillas simplifican las auditorías y los informes de cumplimiento, con monitoreo continuo e historiales de datos detallados.
Can DDR prevent data leaks in cloud apps?
Yes. Forcepoint DDR extends monitoring and protection to supported cloud and SaaS environments, using AI-powered classification and continuous analysis of file activities (such as uploads, shares, and permission changes) to detect and help prevent data exfiltration.
Does DDR use AI in its threat-detection capabilities?
Yes. The classification system in Forcepoint DDR is powered by AI Mesh, which provides high accuracy, a better understanding of context, and risk scores across monitored environments. This AI-native approach improves detection quality (fewer false positives, better prioritization) and enables automated or guided responses to suspicious data activity, making DDR materially more effective than static rule-only monitoring.
What types of data does DDR monitor and protect?
Forcepoint DDR monitors both structured and unstructured data, with specific focus on sensitive information such as PII, PHI and PCI data, as well as business-critical intellectual property. It tracks data across supported cloud and endpoint sources, following how files and records are created, accessed, modified, renamed, shared, or deleted. Using its proprietary AI Mesh data classification, it continuously identifies and prioritizes at-risk data wherever it resides.
¿Cómo se integra Forcepoint DDR con otras herramientas de seguridad?
Forcepoint DDR es un complemento importante para la solución Forcepoint DSPM, que permite el monitoreo continuo de los datos en uso. Combinar Forcepoint DSPM y DDR con Forcepoint DLP crea un ecosistema de seguridad de datos integral, que protege los datos donde sea que residan, cómo se accede a ellos o cómo cambian con el tiempo. Forcepoint DDR también se integra sin problemas con las soluciones de SIEM y SOAR a través de webhooks para mejorar la respuesta a incidentes y la gestión de amenazas.
What does DDR solve that DLP and SIEM don’t do?
Forcepoint DDR focuses on data-in-use and data behavior, delivering continuous monitoring, rich context and dynamic response where traditional DLP and SIEM have blind spots. DLP is optimized to enforce policies on data-in-motion (email, web, endpoints, etc.), and SIEM aggregates logs and alerts from many systems. DDR adds deep, AI-driven understanding of sensitive data and its lineage plus targeted response actions across clouds and endpoints. DDR enhances DLP and SIEM, augmenting them with highly accurate, context-centric intelligence and automating remediation when suspicious activities begin to take place. In combination, the three tools form the foundation for an effective data security strategy.
How does DDR support compliance and auditing?
Forcepoint DDR supports compliance by continuously monitoring exposure of regulated data such as PII, PHI, and PCI, using predefined detection templates and AI-driven classification aligned to common privacy and industry frameworks. This ensures faster identification of non-compliant data handling across monitored sources.
For auditors and regulators, Forcepoint DDR maintains detailed histories of data activities and risk events, enabling transparent reporting on who accessed what, how data moved, and which remediation actions were taken. This directly supports audits for GDPR, HIPAA, PCI DSS, CCPA and similar mandates.
¿Cómo apoya Forcepoint DDR el cumplimiento de las regulaciones de protección de datos globales?
DLP utiliza múltiples herramientas para identificar información confidencial dentro de un entorno de TI, monitorear el flujo de datos dentro y fuera de la organización y bloquear datos confidenciales para que no salgan de la organización en función de políticas de seguridad.



