Secure Access Service Edge (SASE) mimarisi, son birkaç yılda popülerlik kazanmıştır ve popülerliğin yakında azalacağına dair bir işaret yoktur.
Güvenlik ekipleri, tehditleri önlemek ve daha iyi bir kullanıcı deneyimi sunmak için politika uygulamalarını uca yaklaştırmaya çalışırken, SASE, güvenlik stratejilerini uygulama ve sürdürme şekillerini basitleştirmek için önde gelen seçenek olarak görünmeyi sürdürüyor.
Bu Kılavuzda
Secure Access Service Edge (SASE) mimarisinin siber güvenlik etkilerini ve kurumsal avantajlarını derinlemesine kılavuzumuzla keşfedin.
- SASE‘ye Giriş
- SASE Mimarisi Nasıl Çalışır?
- SASE‘nin Beş Temel Bileşeni
- SASE ile Herhangi Bir Yerden ve Her Yerde Erişimi Güvence Altına Alma
- Data-first SASE ile Daha İyi Veri Güvenliği
- Geçiş ve Devreye Alma En İyi Uygulamaları
- Uyumluluk ve Data-first SASE
- Data-first SASE ile Dönüşümü Hızlandırın
- Kaynaklar ve Referanslar
SASE‘ye Giriş
SASE, ağ ve güvenlik çözümlerini ve işlevselliği bulut tabanlı tek bir hizmet modelinde birleştirir. Bu özelliklerin birleştirilmesi maliyetleri azaltır, uygulama performansını artırır ve kuruluşlar için daha iyi koruma sağlar.
Gartner®, SASE konseptini ilk olarak 2019 yılında kaleme aldı ve pandemi koşullarıyla BT ekiplerinin giderek artan şekilde dağınık hale gelen iş güçlerini ve BT ağlarını desteklemeye çalışması adaptasyonu hızlandırdı.
SASE, birkaç yıl içinde akademik bir konseptten siber güvenlik endüstrisi liderleri tarafından desteklenen en yaygın mimari haline geldi. Gartner, 2025 yılına kadar genel olarak kullanılabilir tek tedarikçili SASE tekliflerine sahip tedarikçi sayısında 2023 ortasına kıyasla yüzde 50 artış bekliyor.
Ağ iletişimi ve güvenliği bir araya getirmek, SASE'nin trafiği denetim için merkezi bir veri merkezinden geçirmek yerine doğrudan buluta bağlantıları etkinleştirerek son kullanıcılar için performansı hızlandırmasına olanak tanır. Benzer şekilde, birleşik güvenlik hizmetleri, işlerini yapmak için ihtiyaç duydukları uygulamalarla etkileşime giren çalışanlar için daha basit bir kullanıcı deneyimini desteklemektedir.
Kuruluşlar, SASE ile yeni çözümler sunuyor ve Sanal Özel Ağ (VPN) erişimi gibi eski teknolojilerden uzaklaşıyor. Zero Trust Network Access (ZTNA), SASE‘nin kritik bir parçasıdır ve kuruluşların, VPN‘lerin dahili uygulama erişimi için kullanıcıları ve cihazları doğrulaması sırasında oluşan gecikme süresinden kaçınmasına olanak tanır.
Evden çalışan ve dünyanın dört bir yanından aynı çatıda toplanan insan sayısının fazlalığı ile SASE çözümleri, kuruluşlar için üretkenliği korumak ve güçlü bulut güvenliği sağlamak için esas hale gelmiştir. SASE; uzaktan çalışmayı destekler, ölçeklenebilirliği artırır ve "Kendi Cihazını Getir" (BYOD) politikalarını daha güvenli hale getirir.
SASE Mimarisi Nasıl Çalışır?
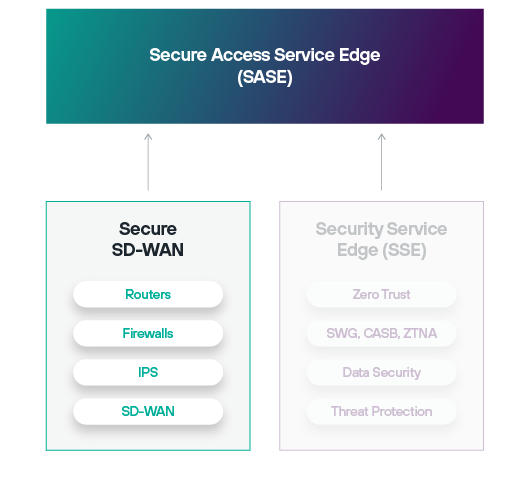
SASE‘nin güvenlik ve ağ oluşturma alanları sırasıyla Security Service Edge (SSE) ve Software-Defined Wide Area Networking (SD-WAN) olarak bilinir.
Bunlar tek bir tedarikçi tarafından birlikte sunulduğunda, bugün en yaygın şekilde kullanılan ve Gartner® tarafından tanımlanan en etkili SASE modelini oluşturur:
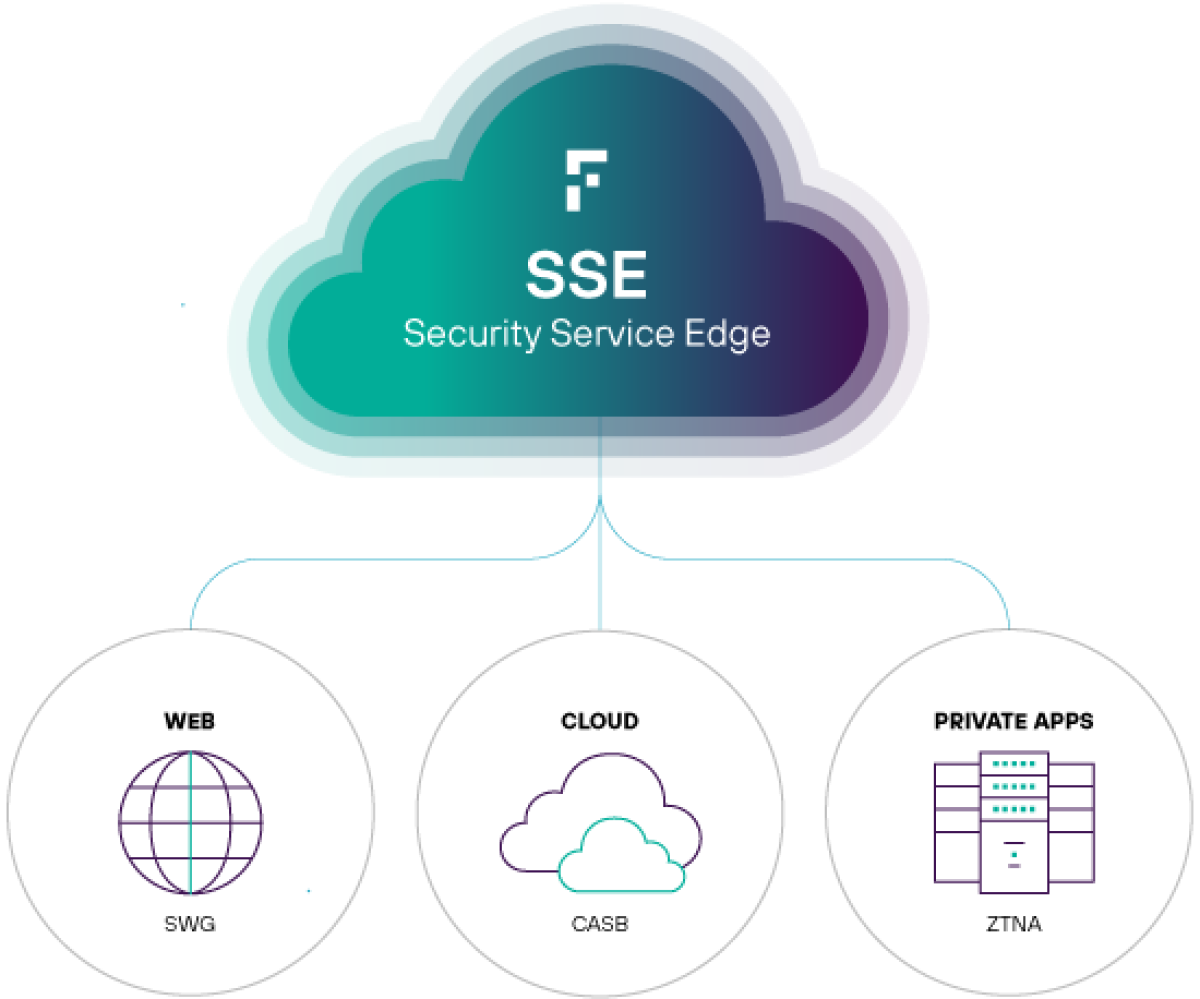
Security Service Edge
SSE, üç temel erişim noktasını güvence altına alır: web, bulut ve özel uygulamalar. Saldırganları dışarıda tutarken hassas verileri barındırmakta üstündür.
Bu güvenlik işlevselliğinin birleştirilmesi, kuruluşların; erişim kontrolü, veri güvenliği, tehdit koruması ve izlemeyi tek bir platform altında birleştirmelerini sağlar. SSE‘nin bireysel bileşenleri, nihayetinde hepsini bir araya getirme hedefi ile ihtiyaç duyulduğunda bir güvenlik stratejisine dahil edilebilir.
SASE, bağlantıyı optimize edip gecikme süresini azaltarak SSE‘nin verimli ve yüksek kaliteli bir kullanıcı deneyimi ile performans göstermesine olanak tanır
Software Defined Wide Area Networking
SD-WAN, kuruluşun trafiği daha etkin ve kolay bir şekilde yönlendirip yönetmesini ve kullanıcıların bulunduğu her yerde ağ politikaları oluşturup ve bunları genişletmesini sağlar.
Kullanıcılar için uygulamalara ve kurumsal kaynaklara en hızlı erişimi sunmak üzere MPLS, LTE ve geniş bant internet hizmetleri dahil olmak üzere herhangi bir bağlantı türü kombinasyonunu kullanarak ağ oluşturma maliyetlerini azaltabilir. SD-WAN teknolojisi, bant genişliği tüketimini optimize etmek için trafiği daha verimli bir şekilde yönlendirerek performansı da artırabilir.
Secure SD-WAN çözümleri, sorunsuz ve güvenli bir kullanıcı deneyimi sunmak için güvenlik odaklı bir SASE platformuyla iyi bir şekilde bir arada kullanılabilen IPS ve Advanced Malware Detection gibi bazı yerleşik güvenlik özellikleri içerir
Kuruluşlar, geleneksel bir güvenlik modeli altında, hibrit iş güçlerini tehditlerden korumak için çok noktalı ürünler kullanır. Buna karşın çeşitlilik içeren güvenlik modeli, kapsam boşluklarına, yanlış pozitif uyarılara ve kullanıcılar için kötü performansa yol açar. Bu, tehditlerin tespit edilmeden gözden kaçmasına olanak tanır ve çalışanları kuralları es geçmeye iterek kuruluşu daha fazla riske maruz bırakır
SASE bunların hepsini değiştirir. Güvenlik düzeyinde, politika yapılandırmasını ve uygulamasını tek bir konsolda birleştirerek yönetim ve bakımı kolaylaştırır. Buluttan sunulan güvenlik hizmetleri ve gelişmiş ağlar, bulut uygulamaları için daha iyi performans ve güvenlik sağlar ve aracısız kapsam daha sorunsuz bir kullanıcı deneyimine katkıda bulunur.
SASE‘nin Beş Temel Bileşeni
SASE‘yi başarıyla devreye almak için benimsemeniz gereken beş temel bileşen vardır. Bunlardan bazıları:

Secure Web Gateway (SWG)
SWG, kötü amaçlı web sitelerine karşı koruma sağlar ve kullanıcı tarafından başlatılan trafiği korumak için içerik denetim filtreleri aracılığıyla şirket genelinde web‘de gezinme politikaları devreye alır. Bir bulut proxy‘si kullanabilir veya doğrudan uç noktada çalışabilir. Forcepoint ONE SWG, SASE güvenliğini iki temel ürün ve işlevsellikle artıran Zero Trust Web Access‘in (ZTWA) bir parçasını oluşturur:
Remote Browser Isolation (RBI): RBI, riskli siteleri uzak bir sanal kapsayıcıda işle
Zero Trust Content Disarm & Reconstruction (CDR): Zero Trust CDR dosyalardan geçerli iş bilgilerini ayıklar, bunların güvenli olduğunu doğrular ve iş bilgilerini aktarmak için yeni dosyalar oluşturur; böylece gelişmiş sıfır gün saldırılarını ve istismarları önler
Cloud Access Security Broker (CASB)
CASB, bulut uygulamalarına erişimi güvence altına alır ve bu uygulamalar içinde veri güvenliği politikaları devreye alır. Forcepoint ONE CASB, korumayı herhangi bir cihaza genişletmek için aracı tabanlı ve aracısız bir koruma sunar. Ayrıca, bulut uygulaması kullanımını (onaylanmış veya onaylanmamış) otomatik olarak keşfeder, riskleri analiz eder ve 800.000‘den fazla SaaS ve üretim uygulaması için uygun kontroller devreye alır.


Zero Trust Network Access (ZTNA)
ZTNA, yönetimli veya yönetimsiz cihazlarda kullanılmakta olan veriler üzerinde gelişmiş kontroller sağlayarak, özel web uygulamalarına her yerden kontrollü erişim sağlanmasına imkan tanır. Forcepoint ONE ZTNA, en az ayrıcalık ilkesini kullanarak ve genel olarak Çok Faktörlü Kimlik Doğrulama (MFA) ve Çoklu Oturum Açma (SSO) gibi işlevler sunarak kullanıcının belirli bağlamına göre erişim sağlar.
Hizmet Olarak Güvenlik Duvarı (FWaaS) / Bulut Güvenlik Duvarı
SWG, CASB ve ZTNA bir araya gelerek SSE‘yi oluştururken, güvenlik duvarı teknolojisi de güvenliğin ve ağların kesişimini temsil eder. Next-Generation Firewall (NGFW) teknolojisi hem fiziksel hem de sanal cihazlarla kullanılabilir ancak uzaktan çalışmayı bir SASE mimarisi içinde ölçeklendirmek isteyen yöneticilerin öncelikle Hizmet Olarak Güvenlik Duvarı (FWaaS) olarak bilinen bulut tabanlı çözümlere yönelmeleri muhtemeldir. Bunlar bulut aracılığıyla dünyanın herhangi bir yerinden devreye alınabilir ve merkezi yönetim ve otomasyon yoluyla görünürlük ve kontrol sağlar.


Software-Defined Wide Area Networking (SD-WAN)
Donanım kurulumunu ortadan kaldırmanın ve mevcut olan herhangi bir bağlantıyı esnek bir şekilde kullanmanın yanı sıra secure SD-WAN, çok katmanlı denetim, izinsiz giriş önleme ve DNS sinkhole gibi yerleşik güvenlik işlevselliği sunar. Forcepoint Secure SD-WAN ayrıca görev açısından kritik uygulamaların gerekli bant genişliğini almasını sağlamanın yanı sıra gecikme ve titremeyi azaltmak için trafik yönlendirme ve uygulama sağlığını izleme gibi özellikleri uygulayabilir.
SASE ile Herhangi Bir Yerden ve Her Yerde Erişimi Güvence Altına Alma
Son yıllarda aşama kaydeden tek güvenlik çerçevesi SASE değildir. Ayrıca dikkat edilmesi gereken bir diğer husus da, tüm kullanıcıların ve cihazların bir ağ içindeki BT kaynaklarına erişim sağlamadan önce sürekli olarak doğrulanmasını gerektiren Zero Trust çerçevesidir. Bu yaklaşım, güvenli ağ çeperindeki herhangi bir kişinin veya herhangi bir şeyin güvenilir olarak kabul edildiği geleneksel ağ güvenliği uygulamalarının tersidir.
Ancak mesele bir SASE veya Zero Trust mimarisi arasında seçim yapmak değildir. Aslında, göz önünde bulundurulan herhangi bir SASE platformu, Zero Trust ilkelerini de içerecektir. Bu iki konseptin birleşimi, geleceğe dönük veri güvenliği uygulamaları için temel oluşturur.
Veri güvenliğine yönelik bu entegre yaklaşım, Forcepoint tarafından öncülük edilen Data-first SASE konsepti için temel oluşturur.
Data-first SASE, sadece erişim güvenliğini sağlamanın ötesine geçer. Bunu, iş verilerinin kullanımını sürekli olarak koruyup verimliliği en üst düzeye çıkarmak ve işletme maliyetlerini azaltmak için güvenliği basitleştirerek başarır. Data-first SASE‘nin temel avantajları şunlardır:
Her Yerde Veri Güvenliği - Veri güvenliği politikalarını web, bulut, e-posta, ağ ve uç nokta genelinde sorunsuz bir şekilde yalnızca birkaç tıkla genişletin
Dağıtılmış devreye alım - Bulut, ve uç noktalar genelinde politikaları daha fazla performansla devreye alın
Güvenilir ölçeklenebilirlik - Bir AWS hiper ölçekleyici platformunun esnekliği ile büyüyün

Data-first SASE ile Daha İyi Veri Güvenliği
Data-first SASE Forcepoint ONE ile başlar. Hepsi bir arada bulut tabanlı güvenlik platformu, performansı tek bir konsolda güvenlik ile eşleştirir.
Forcepoint ONE, kuruluşların ihtiyaç duyulduğunda hizmet eklemelerini ve yapılandırma ve eğitim için harcanan süreyi en aza indirmelerini sağlayan modüler bir yapı sunar. Güvenlik ekipleri bunu, SSE‘ye ve SD-WAN‘a Zero Trust Data Security‘nin ek unsurunu ekleyerek adım adım Data-first SASE mimarisi oluşturmak için kullanabilir.
Forcepoint ONE, Forcepoint ONE ve Forcepoint DLP arasındaki entegrasyon yoluyla Her Yerde Veri Güvenliği sunar. Politika yapılandırmasının bulut, web, e-posta, ağ ve uç nokta genelinde sadece birkaç tıkla çoğaltılmasına olanak tanır. Konumuna bakılmaksızın kullanıcılar için verilere daha güvenli erişim sağlamak üzere SASE‘nin sunduğu bütünlükten yararlanır.
Verilerinizi her yerde ne kadar kolay bir şekilde güvence altına alabileceğinizi keşfedin.
Data-first SASE için Temel Kabiliyetler ve Kullanım Durumları
2023 Gartner® Critical Capabilities for Single-Vendor SASE‘de Gartner, üç temel kullanım örneği tanımlamıştır: Temel SASE, Ağ Odaklı SASE ve Gelişmiş Güvenlik ile SASE.
Gartner‘ın gözlemine göre: "across all offerings, most vendors provide strong branch networking and branch security capabilities. However, the level of advanced security features across all offerings is only mediocre for most enterprises."*
Bu raporda Forcepoint, Advanced Security Use Case için en üst sıradaki tedarikçi olarak seçildi.
Hangi kuruluşlar Gelişmiş Güvenlik ile SASE‘yi göz önünde bulundurmalı? Gartner bu konuda açıktır: "This is typically a highly regulated enterprise or one that deals with sensitive information, such as financial services, insurance and healthcare. It is an organization that requires advanced security capabilities, not simply “good-enough” security."

Data-first SASE‘nin Faydaları ve Avantajları
SWG, RBI ve Zero Trust CDR ile bilinen ve bilinmeyen web tabanlı saldırıları önleyin.
CASB ile herhangi bir bulut uygulamasında güçlü veri kontrolleri uygulayın.
ZTNA ile VPN olmadan özel web uygulamalarına Zero Trust erişimi sağlayın.
Secure SD-WAN ile ofisleri, şubeleri ve uzak tesisleri bağlayın ve koruyun.
Data Loss Prevention (DLP) ile verilere erişilen her yerde veri güvenliği politikalarını tutarlı bir şekilde uygulayın.
Forcepoint ONE Insights ile ekonomik değer ve güvenlik analizlerini gerçek zamanlı olarak izleyin.
Geçiş ve Devreye Alma En İyi Uygulamaları
Bir şirketi yeni bir güvenlik modeline taşımak göz korkutucu bir ihtimal olabilir ancak bu yeni sistemleri devreye sokmak için ipuçları ve en iyi uygulamaları bulabilirsiniz. Aşağıda Forcepoint‘in süreci daha sorunsuz hale getirmek için bir araya getirdiği iki kılavuz bulunmaktadır.

Bireysel ürünler aynı tedarikçiden geldiğinde ve birlikte çalışmak üzere tasarlandığında Data-first SASE güvenlik modelinin uygulanma kolaylığı önemli ölçüde artar. Benzersiz, Data-first SASE Platformu Forcepoint ONE, tek tedarikçili SASE‘nin avantajlarını, Forcepoint‘in diğer SASE tedarikçilerinden nasıl ayrıştığını ve Forcepoint ONE‘un Data-first SASE‘nin benimsenmesini nasıl kolaylaştırdığını açıklar.
Uyumluluk ve Data-first SASE
Data-first SASE, şirketlerin dünya çapında veri düzenlemelerine uyum sağlamalarına yardımcı olma konusunda üstündür. Forcepoint DLP, 80‘den fazla ülkenin veri gizliliği gereksinimlerine uyan 1.700‘den fazla önceden tanımlanmış sınıflandırıcı ve politika şablonu sunar. Forcepoint ONE aracılığıyla bu politikalar kuruluşun farklı uçlarına genişletilebilir ve denetimler için geniş bir kapsam ve görünürlük sağlar.
Kuruluşlar, ilgili düzenlemeleri anlamak ve bunlarla uyumu sağlamak için adımlar atmakla yükümlüdür. İşletmenizle ilgili olabilecek bazı temel düzenlemeler:
Veri Gizliliği Uyumluluğu - Basitleştirilmiş
Kuruluşlar, güvenlik işlevlerini tek tedarikçili SASE platformunda konsolide ederek bir çok kanal genelinde politikaları daha kolay uygulayabilir. Bu, değişen veya geçerli yeni yasal zorunluluklarla esnek bir şekilde başa çıkmayı kolaylaştırır.
Her Yerde Veri Güvenliği Forcepoint‘in SWG, CASB ve ZTNA‘nın yanı sıra uç nokta ve e-posta genelinde bir politika belirlemek, değişiklikleri hızlandırmak ve iş gücü tasarrufu yapmak için sunduğu bir özelliktir.
Data-first SASE ile Dönüşümü Hızlandırın
Dünya çapında kuruluşlar, iş verimliliğini artırmak ve işletme maliyetlerini azaltmak için yeni fırsatlar aradıkları dijital transformasyon üzerine odaklanmıştır. Giderek daha fazla dağınık hale gelen kuruluşlar, kullanıcılara şirket kaynaklarına daha hızlı ve daha uygun maliyetli erişim sunmak üzere en değerli verilerini ve uygulamalarını buluta taşımak için ağlarını ve güvenliklerini yeniden yapılandırıyor.
Birçok kuruluş, bulut için gerekli olan güvenilir ve güvenli bağlantıyı SASE aracılığıyla sağlar. SASE, kuruluş çapında şunlar dahil olmak üzere birçok avantaj sağlar:
İş geliştirici SaaS/bulut uygulamalarının benimsenmesini hızlandırarak üretkenliği artırın
Davetsiz misafirleri dışarıda tutmak için doğrudan buluta SD-WAN kurulumuna güvenlik ekleyerek riski azaltın
Pahalı MPLS bağlantılarına duyulan ihtiyacı önleyerek maliyetleri düşürün
Binlerce sitede bağlantı ve güvenliği entegre ederek operasyonları kolaylaştırın













