
1.2万多客户的选择不会错










































了解并控制敏感数据
借助全方位的数据发现与高度准确的分类技术,让暗数据无所遁形。
Forcepoint DSPM 软件可扫描任何数据源,并使用专有的 AI Mesh 技术来识别、分类和修复高风险数据。
如果您的安全团队在以下方面遇到困难,这是一个完美的解决方案:
大量影子数据
过度许可的数据
GenAI 数据泄漏风险
数据位置不明
Forcepoint DSPM Software Leads the Pack
Forcepoint is the only Data Security Posture Management vendor that uses AI Mesh technology to deliver highly accurate data classification. Read the full comparison chart to learn why organizations trust the leading data security provider to discover and catalogue data and remediate risk at scale.
20%
40%
60%
80%
100%
Forcepoint
Traditional Vendor
Data Governance Vendor
为什么 Forcepoint DSPM 是顶级安全工具
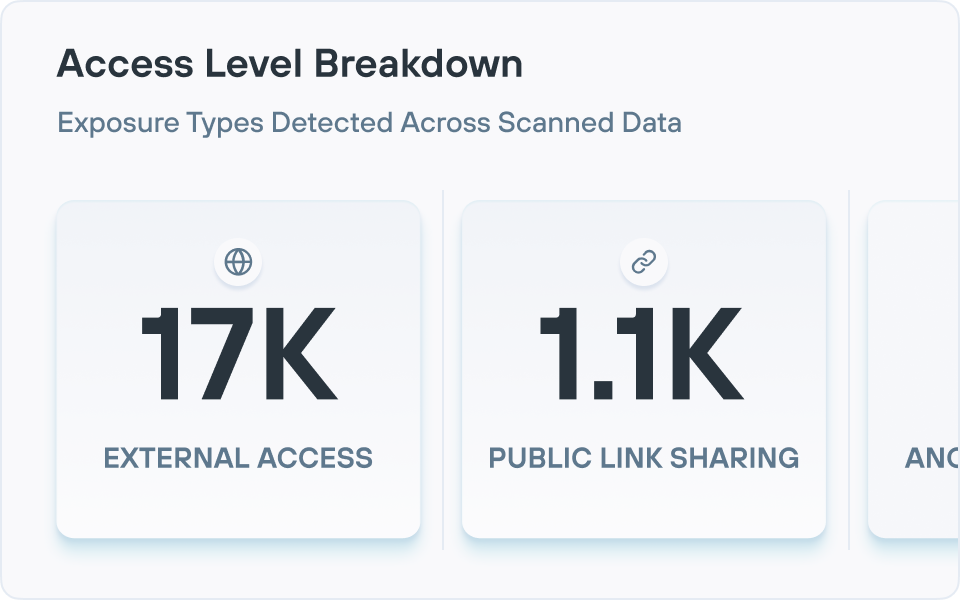
提升数据可见性
获得对云和本地环境中的结构化和非结构化数据的全面可见性,从而跟踪和管理敏感数据,无论其位于何处。
借助 AI 发现和分类
运用高度准确的 AI Mesh 技术实现高效、可靠的数据发现和分类,减少误报并提高事件警报的准确性
主动化解风险
借助可实施的洞察,您能够管理权限,移动放置错误的数据,并解决数据主权、访问权限以及重复或过时琐碎 (ROT) 数据问题。
自动化合规管理
利用自动化简化合规流程,确保始终符合不断变化的法规要求,减少人工投入。


精准掌握与透明化报告
FBD Insurance 首席技术运营官 Enda Kyne 表示,DSPM 和 DDR 能够控制关键数据并向监管机构报告相关活动,因而受到其 IT 安全和数据保护团队的青睐。
Strengthen Your Data Security Posture



Rapidly and precisely identify sensitive data-at-rest with AI Mesh technology that fine-tunes its classification accuracy relative to your unique organizational needs.

Extend visibility and control over all your regulated data, eliminate gaps and generate automated reports to demonstrate compliance.

Gain a centralized view of your data and enforce the Principle of Least Privilege across cloud, SaaS and on-prem systems for effective governance.


您的数据存在风险吗?
一份能够主动发现数据威胁的数据风险评估,无论是未分类的敏感文件还是过度授权的用户。借助 Forcepoint 提供的免费数据风险评估,观看 DSPM 的运作方式,并了解您的数据是否安全。



能够集成 DLP、DSPM 和 DDR,实现数据发现、分类、保护和补救。

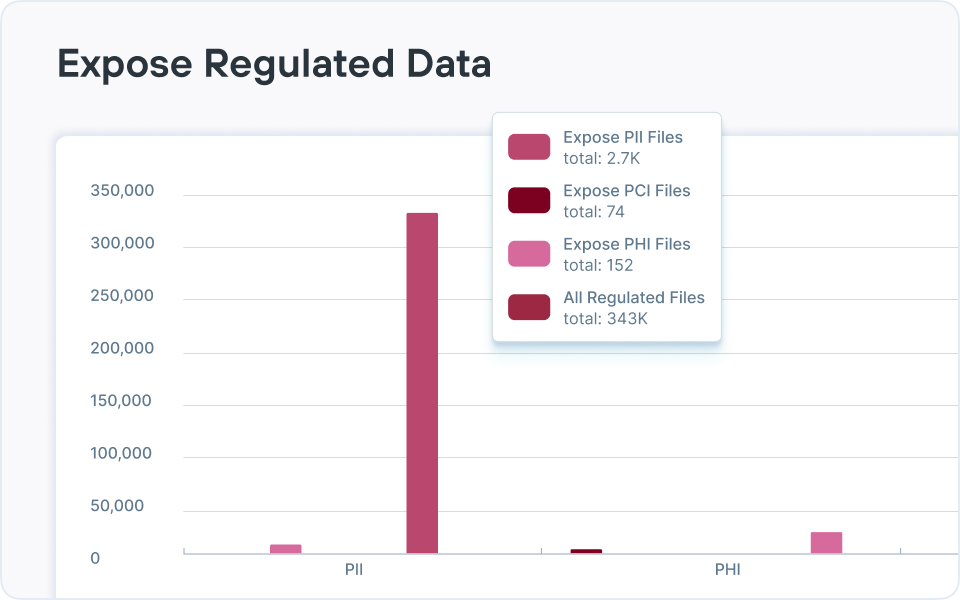
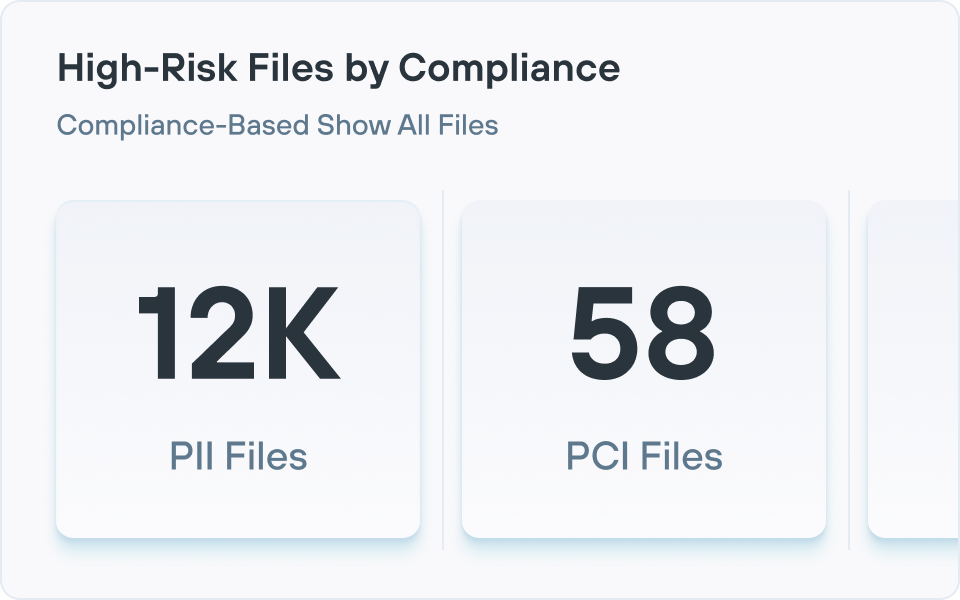
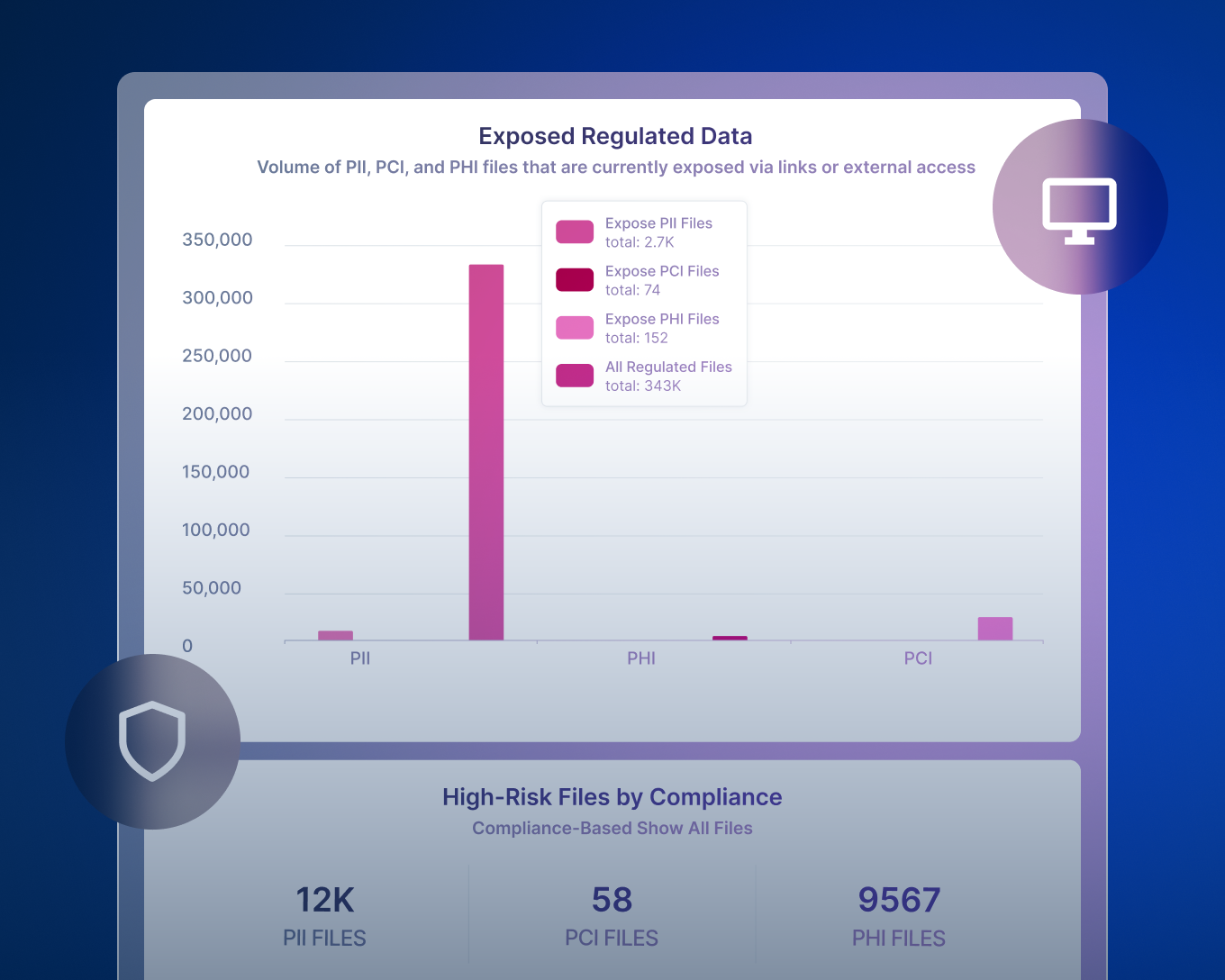
提供有效的风险报告,使您能够发现 ROT(冗余、过时、琐碎)数据、过度授权的数据、数据主权问题以及许多其他使整体数据态势面临风险的问题。

提供对所有 GenAI 应用的数据准备情况的可见性与控制。 它还能够确保 Copilot 和 ChatGPT Enterprise 的使用安全。
我们的客户案例
我们的客户案例
"As part of Forcepoint’s broader data security ecosystem, DSPM has integrated seamlessly with our existing solutions. It’s an essential component of our overall data security strategy."
Indonesia Financial Group (IFG)
由分析师所推荐。
用户认可。
Forcepoint 一直被用户和行业分析师评为顶级数据泄露防护软件和数据安全软件提供商之一。
Forcepoint 在 IDC MarketScape: Worldwide DLP 2025 Vendor Assessment 中荣获“领导者”称号。
Forcepoint 连续第二年被 Frost & Sullivan 评为 2024 年全球 DLP 年度公司。
Forcepoint 荣获 2025 年第一季度 The Forrester Wave™: Data Security Platforms 表现卓越的企业。
实施 Data Security Posture Management 最佳实践
常见问题
什么是数据安全态势管理 (DSPM)?
Data Security Posture Management 是一种安全解决方案,能够持续发现敏感数据的位置、分类方式以及谁能够在云、SaaS 和本地环境中访问这些数据。 Forcepoint 的 AI 原生 DSPM 遵循相同的模型:它持续清点结构化和非结构化数据,使用 AI Mesh 技术在文件存储、云应用和本地位置准确分类,并通过各种镜头评估这些数据是否存在风险。 Forcepoint DSPM 通过将定期审计态势转变为实时运行的数据风险视图,帮助提高生产力、削减成本、降低风险并简化合规流程。
DSPM 解决方案如何运作?
大多数 DSPM 平台都遵循循环生命周期:发现数据(跨多个云和本地的结构化和非结构化)、按敏感性和业务上下文对其进行分类、评估风险并排定优先级(例如过度特权访问或错位数据)、纠正配置错误或不安全访问,然后持续监控以保持最新态势。 Forcepoint DSPM 使用 AI Mesh 实现这一点,AI Mesh 是一种使用小型语言模型和深度神经网络的 AI 分类架构。
Forcepoint DSPM 将扫描集成数据源,识别高风险数据并对其进行分类,并建议后续补救步骤,以便团队能够调整权限、移动错放的数据、清理冗余、过时或琐碎 (ROT) 数据并解决主权问题,而不会止步于报告。 最近的更新将 Forcepoint DSPM 从文件扩展到企业数据库和数据湖,因此相同的发现、分类和自适应实施模型现在能够涵盖结构化和非结构化数据,以及 Forcepoint DDR 和 DLP。
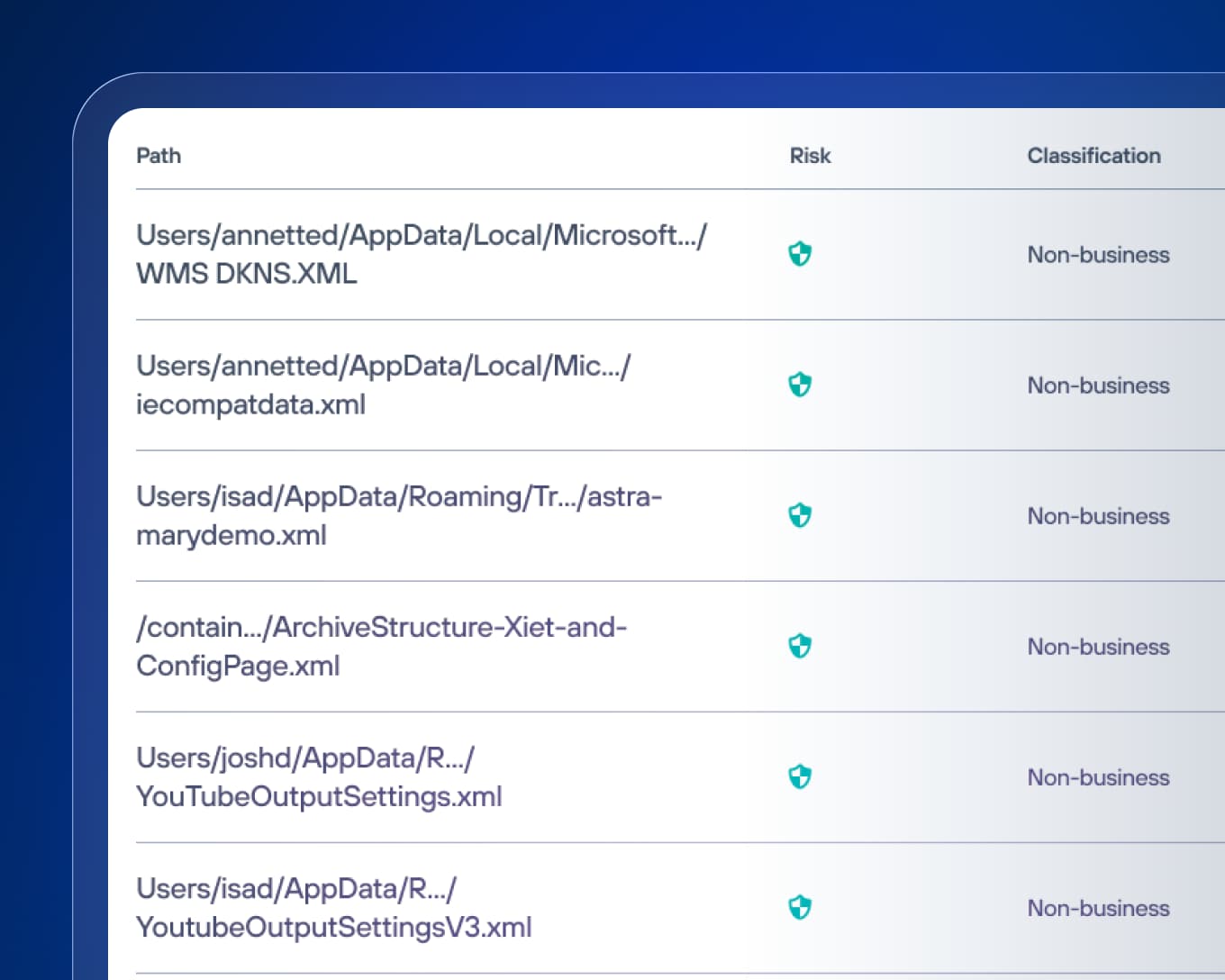
DSPM 软件的数据发现功能是如何工作的?
DSPM 持续发现云端、网络和本地存储中的数据,以揭示并编目您组织拥有的每一条数据。找到敏感数据是保护它的关键第一步。DSPM 解决方案可以扫描您的整个数据生态系统,例如:
- 云平台(AWS、Azure、GCP)
- SaaS 应用(Microsoft 365、Salesforce)
- 本地存储和数据库
现代 DSPM 软件通过内置功能或解决方案集成,在数据移动和变化时保持持续可见性。
DSPM 解决方案提供哪些数据分类和风险评估功能?
成熟的 DSPM 解决方案提供一系列功能:
- 数据发现和 AI 驱动的分类:自动扫描云、SaaS、端点和本地商店,使用经过微调的 AI 根据敏感性和业务目的对结构化和非结构化数据进行准确分类,并提供可调整的模型以减少误报。
- 数据风险评估、风险分析和优先级排序:建立敏感数据清单,然后根据暴露、过度允许的访问和业务影响给风险评分,以便团队首先关注最关键的数据集;Forcepoint 使用风险评分和金融影响估计来优先缓解风险。
- 访问治理:揭示谁有权访问哪些数据,突出显示公共或外部共享、不活跃的帐户和过度共享的文件夹,并通过目录集成对权限进行深入了解。
- 合规和报告:生成仪表板、审计跟踪和框架匹配的报告(适用于 GDPR 或 HIPAA 等法规),能够映射受监管数据、文档控制并简化审计;Forcepoint 添加策略模板、自动化报告和可解释的 AI 分类,以简化混合环境中的合规性展示。
DSPM 平台如何帮助组织管理和化解风险?
发现问题但不解决几乎毫无价值。现代 DSPM 平台通过可自定义控制弥补了这一缺口,以适应您组织的独特需求和挑战。这些控制措施包括实施最小特权原则 (PoLP) 的权限管理,确保用户仅访问其任务所需的文件,并解决过度许可或可公开访问数据的问题。其他功能包括:数据映射,用于正确分类敏感信息;错位数据修复,用于处理存储在不适当存储库中的文件;数据归档/删除工作流,用于管理超过保留期或归类为 ROT(冗余、过时、无用)的高风险文件。
DSPM 软件中的报告和分析如何工作?
DSPM 解决方案包含报告和分析工具,可提供对组织整体数据安全状态的可见性。这些报告功能通常配备仪表板,显示敏感数据在不同环境中的位置,强调特定的风险因素,例如 ROT(冗余、过时、无用)数据、过度许可的文件、错位信息和重复内容。安全团队可以利用这些洞察长期跟踪指标,并优先处理能产生最大影响的补救工作。
Forcepoint DSPM 是部署在本地还是云端?
DSPM 解决方案提供灵活的实施选项:
- 适合快速部署的云原生 SaaS
- 适合敏感环境的混合模型
- 旨在控制数据主权的本地部署
- 可最大限度减少开销的无代理架构
大多数企业从最关键的数据存储库开始,逐步扩大覆盖范围。
Forcepoint DSPM 如何使用 AI 和自动化?
自动化支持在企业环境中进行持续、大规模的数据发现和扫描。组织现在可以在创建、移动或修改数据时对其进行实时自动分类,从而消除人工审核固有的延迟和漏洞。人工智能的主要价值在于提供高度准确的数据分类,同时减少误报。AI 带来了所需的准确性,让您能够自信地区分真正敏感的数据与可能触发传统基于规则的系统的无害信息。为了使 DSPM 解决方案能够自信地整合这些功能,现代解决方案必须处理从 PDF 到视频的各种文件类型,并能理解更广泛的数据字段,以便进行正确的分类并根据合规要求进行调整。这包括利用 GenAI 功能、深度神经网络分类器和其他预测性 AI 技术协同工作。
实施 DSPM 平台可为组织带来哪些关键优势?
数据安全态势管理的优势可归纳为四大成效:
- 提高生产力
- 削减成本
- 降低风险
- 精简合规性
DSPM 是否与其他安全技术集成?
DSPM 很少独立运行。大多数企业将其与互补的安全技术相集成,以创建全面的数据保护策略。DSPM 软件提供的有关数据位置、敏感性和风险的洞察自然而然地增强了其他安全工具,例如:
- Data Detection and Response (DDR)
- Data Loss Prevention (DLP)
- Cloud Access Security Broker (CASB)
- Identity and Access Management (IAM)
- Cloud Security Posture Management (CSPM)
DSPM 与传统数据分类工具有何不同?
与使用预定义规则处理已知数据存储库的传统工具不同,DSPM 持续发现不同环境中的已知与未知数据,利用 AI 实现更准确的分类,并提供有关访问模式和安全控制的上下文。
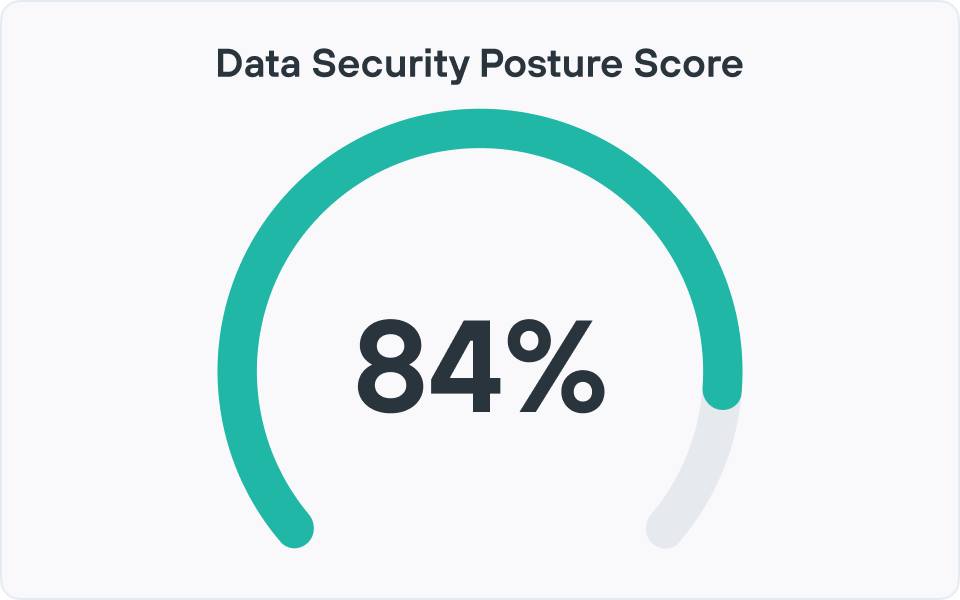
DSPM 如何帮助评估安全态势?
Data Security Posture Management (DSPM) 通过持续发现敏感数据的位置(云、SaaS、本地)、根据敏感性对其进行分类并映射有权访问该数据的人员来评估安全态势。
Forcepoint DSPM 使用其 AI Mesh 引擎和广泛的连接器来清点结构化和非结构化数据。 它突出显示过度暴露的文件、ROT 数据和有风险的权限,并将其与数据风险评估相关联。
然后,它提供高性能的监控和分析,以显示敏感数据存在风险的程度、哪些位置和业务部门导致风险最大,以及随着时间的推移而发生的变化如何影响整体数据风险。 这些洞察通过详细的仪表板和报告得以呈现,让安全和合规团队能够了解其数据安全态势的最新、可衡量的视图,而不是进行时间点审计。
SSPM 和 CSPM 以及 DSPM 之间有什么区别?
CSPM (云安全态势管理) 专注于云基础设施:配置、网络控制、身份和平台服务。 它查找并帮助修复 IaaS、PaaS 和 SaaS 环境中的配置错误,而不是数据本身的内容。
SSPM (SaaS 安全态势管理) 专注于 SaaS 应用:安全设置、访问以及与 Microsoft 365、Salesforce 等服务集成。
DSPM (Data Security Posture Management) 专门关注数据,发现、分类和评估敏感信息的风险,无论这些信息存储在何处。 它回答“我们拥有哪些数据,数据位于何处,谁可以访问数据,以及暴露数据的风险有多大?”
Forcepoint DSPM 是否具有实时监控和风险检测功能?
是。 Forcepoint DSPM 在扫描时提供实时或高频风险评估,根据暴露级别更新仪表板,并利用高级警报系统自动标记异常和潜在漏洞。
DSPM 如何增强云安全?
DSPM 通过提供对云存储、SaaS 平台和数据库中存储的敏感数据的全面可见性来增强云安全。 它准确显示存在哪些数据、数据有多敏感、数据位于何处以及如何共享。
Forcepoint DSPM 扫描主要云提供商和身份源,发现过度暴露的数据、过度授权和错位敏感内容,而传统云工具却忽略了这些内容。
在这种上下文中,安全团队可以在云端实施最小权限访问,根据实际业务和监管影响优先考虑补救,并将 DSPM 发现与 DLP 和其他控制集成。
在云安全中使用 DSPM 有哪些优势?
在云环境中使用DSPM可以提供切实的结果:减少数据泄露(通过过度暴露检测和权限清理),减少多云和SaaS的盲点,并更好地保护IP和受监管数据。
Forcepoint AI Mesh 提高了 Forcepoint DSPM 的分类准确性,直接杜绝误报,并帮助团队专注于真正的风险。
它还通过自动化、集成仪表板和报告提高运营效率。 它缩短调查和补救周期,通过解决 ROT 数据问题降低存储和治理成本,并满足审计和数据保护法规的合规准备要求。
DSPM 是否有助于身份威胁检测和响应?
DSPM 不是身份威胁检测和响应 (ITDR) 平台,但 Forcepoint DSPM 确实检测到与数据相关的身份相关风险。 它绘制出哪些用户和群体可以访问敏感文件,突出显示过度授权或影响大的“风险用户”,并通过分析和警报揭示可疑的访问模式。
这些洞察使安全团队能够快速调查潜在的身份滥用(例如,用户过度访问关键数据),并采取有针对性的措施,例如撤销访问权限、收紧共享或触发现有安全工具的工作流程,从而在不加猜测的情况下加强以身份为中心的数据保护。
DSPM 如何检测和评估敏感数据泄露?
Forcepoint DSPM 使用连接器大规模扫描云和本地数据存储,然后应用 AI Mesh 分类和可配置的检测器根据内容和上下文识别敏感数据(PII、PCI、PHI、IP 等)。
然后,它通过分析共享设置和权限来评估风险,对公共、外部共享、内部过度共享、位置错误或与风险用户相关联的数据进行标记,并在仪表板和报告中量化该风险,以便团队优先采取补救措施。
DSPM 如何简化合规报告?
Forcepoint DSPM 通过持续记录受监管数据的位置、受保护的方式以及谁可以访问数据,集中化 GDPR、HIPAA 等法规以及其他隐私和主权要求所需的证据。 其报告功能和分析套件显示流行框架的合规准备情况和数据风险。
面向合规团队的 Forcepoint DSPM 包含哪些仪表板?
Forcepoint DSPM 分析套件包括预定义的仪表板,例如过度暴露分析、勒索软件暴露分析、关键数据重复、风险用户检测、数据保留、错放数据、数据风险评估和数据控制违规事件跟踪。
合规团队还可以使用由 DSPM 查询语言驱动的内置小部件(计数器、图表、表格、事件视图等)创建自定义仪表板,并将这些视图导出为报告,从而允许他们根据特定法规、业务部门或数据类别定制监督,无需自定义开发。



