12,000 多名客户不會錯










































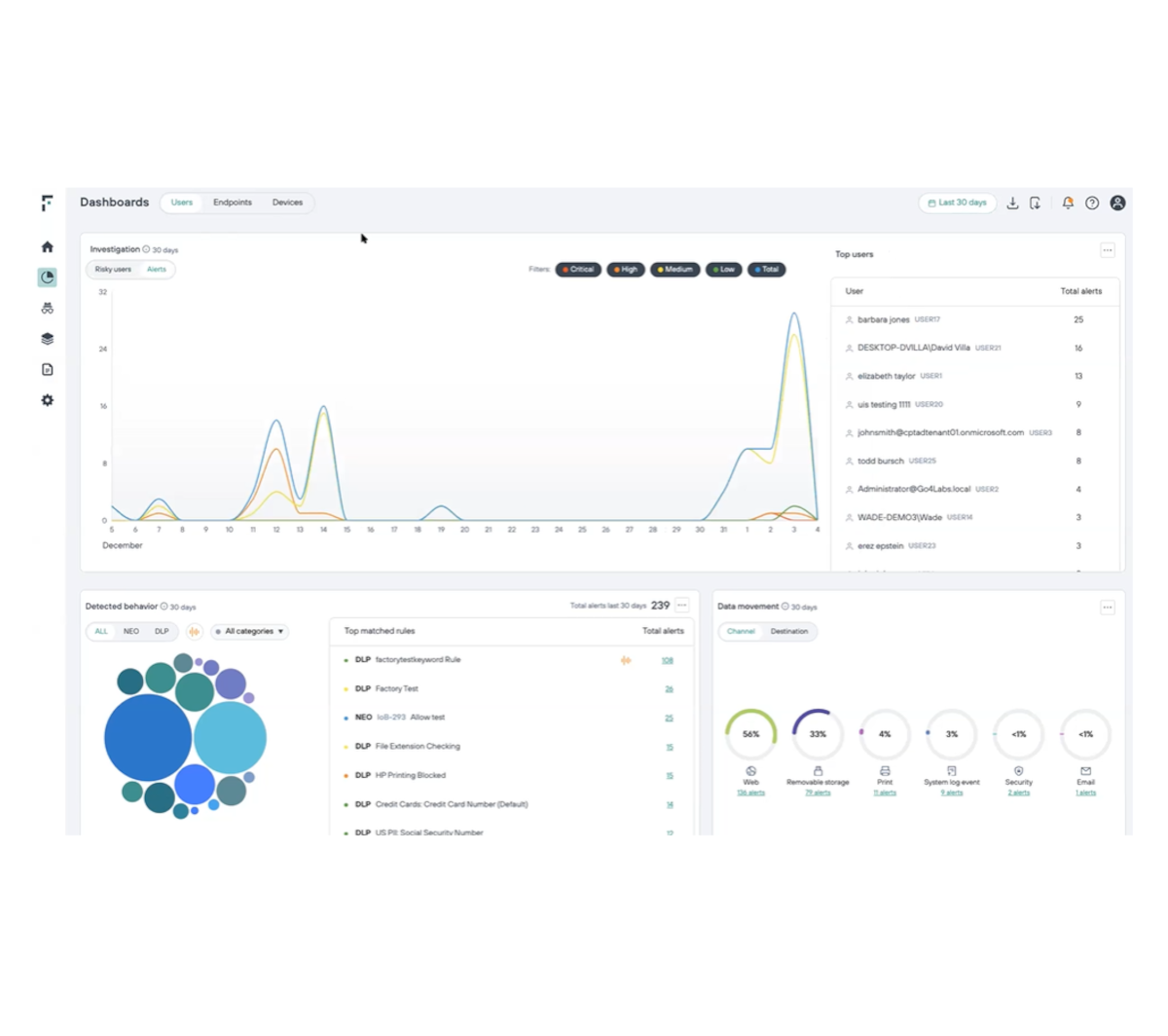
及早發現內部風險
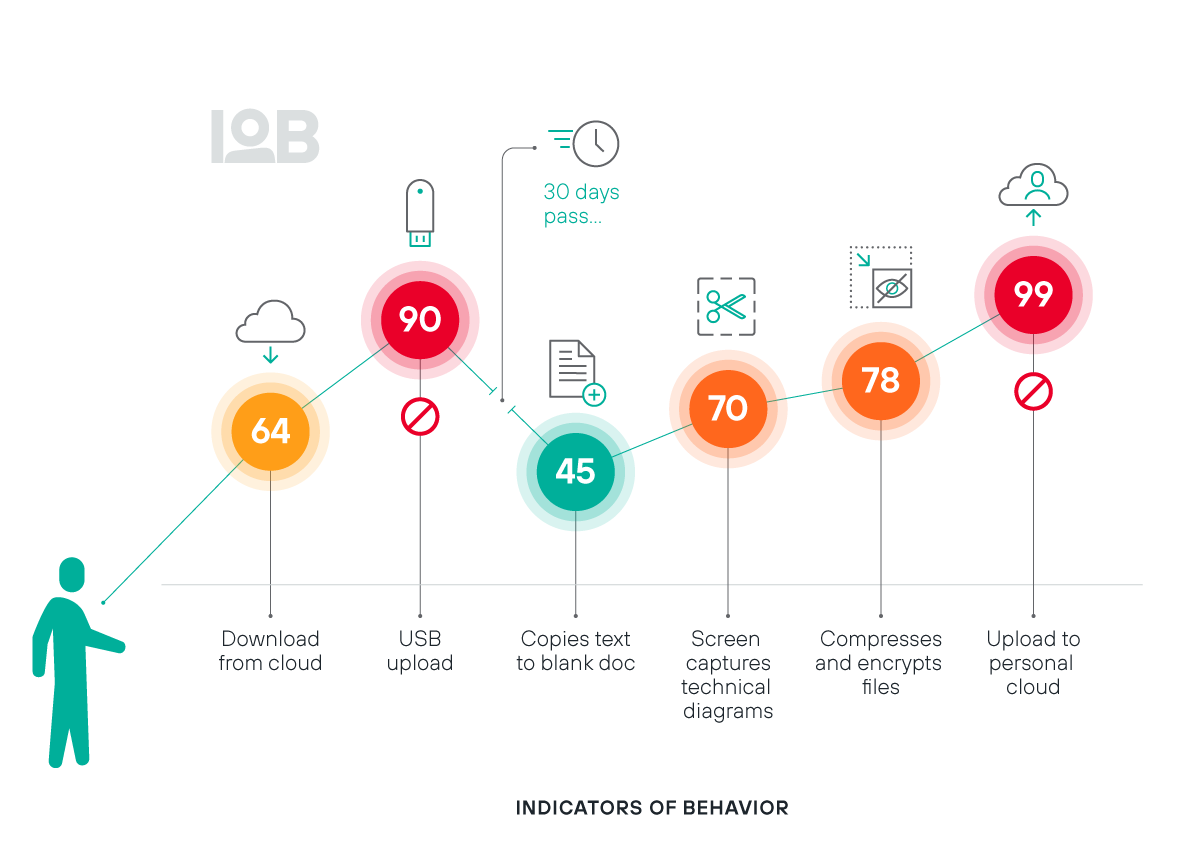
針對使用者與重要資料的互動情況,獲得有意義的能見度
消弭危險盲點,並全面檢視使用者可能做出風險行為的情況
利用持續更新的風險評分,來瞭解使用者的行為與意圖
可提供涵蓋上百個行為指標 (IOB) 的廣泛監控功能
DATASHEET
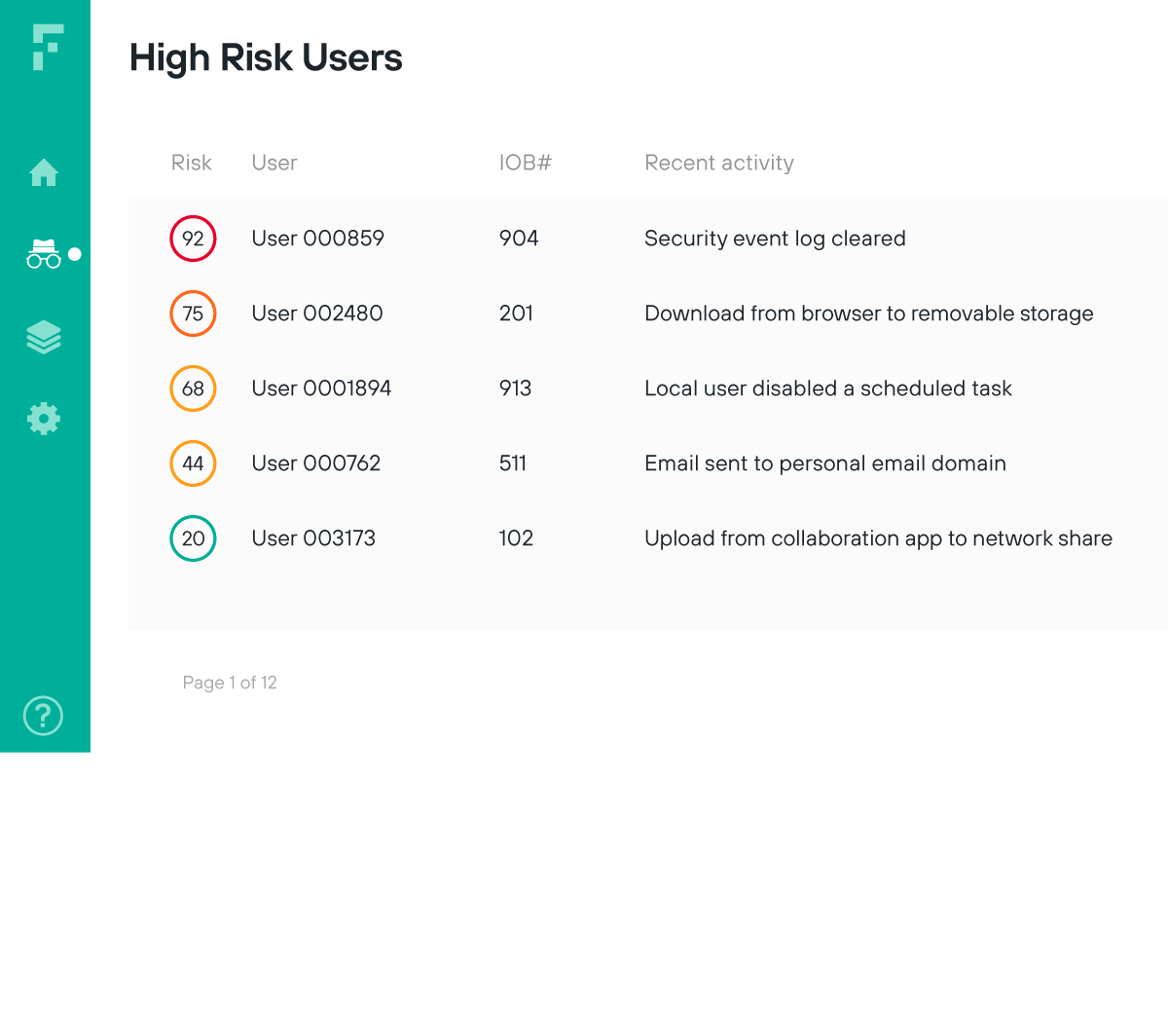
透過持續性的使用者驗證程序來實行 Zero Trust 模式
揭露未經核准的使用者所帶來的風險,並於第一時間警示分析人員注意異常行為,以實現真正的 Zero Trust 安全方法
根據可能表明存在入侵活動的使用者異常行為,限制其存取權限
即時監控使用者與資料的即時互動情況,以確認使用者風險
INFOGRAPHIC
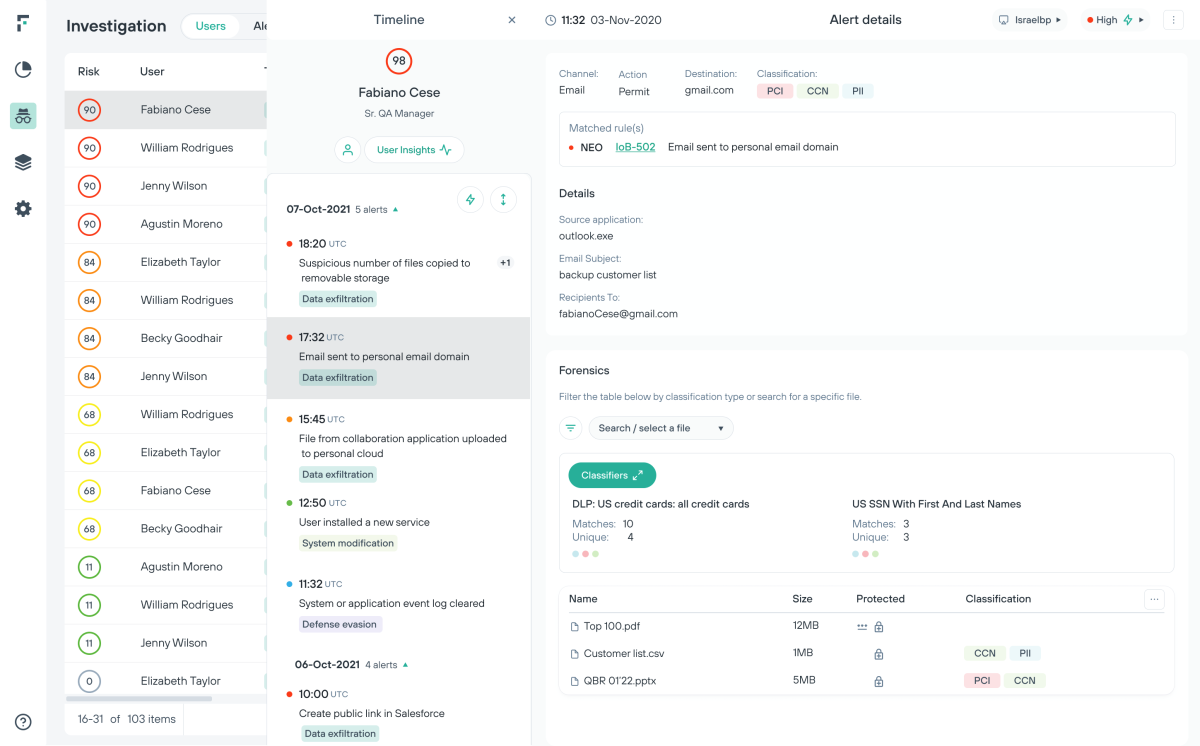
充分提高安全分析人員的效率,並減輕警示疲勞
Risk-Adaptive Protection 可將組織的資料安全做法從事件導向轉變為風險導向。
在使用者層級進行政策調整協調,進而預先防範外洩事件
提高風險調查效率,並強化學習能力
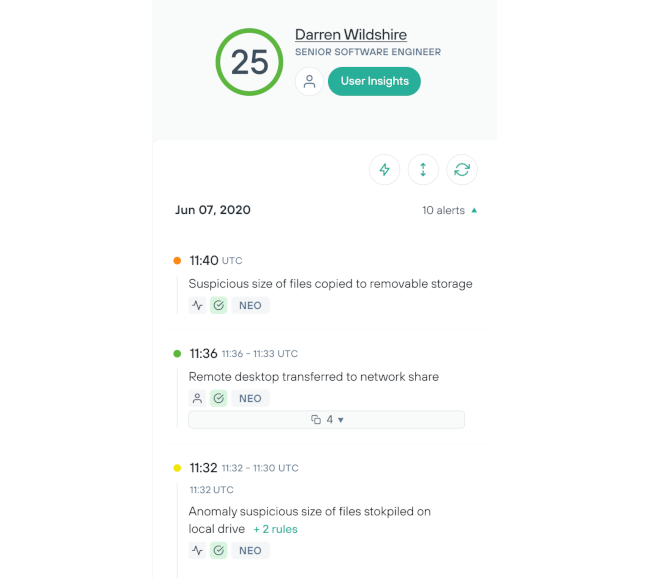
以簡單高效的方式調查來自內部人員的風險
透過簡單的實作程序及個人化的自動化作業,來減少手動操作的需求。
藉由自動化作業及排除誤報情況,來提升分析人員對使用者進行調查的能力
利用維護簡易的雲端基礎架構,以及 30 秒就能完成的代理程式部署作業,讓員工能投入真正重要的事務
即時響應新出現的威脅
通過自動調整安全策略以阻止有風險的使用者行為,從而防止數據泄露。
減少誤報警報,並節省花在事件分析上的時間。
允許低風險使用者存取他們所需的資料,同時避免潛在的威脅。
通過持續監控使用者活動,實現即時數據安全自動化。
分析師推薦。
使用者認可。
Forcepoint 一直被使用者和行業分析師評選為頂尖的資料外洩防護軟體和資料安全軟體供應商。
Forcepoint 在《IDC MarketScape: Worldwide DLP 2025 Vendor Assessment》中被評斷為業界領導者。
Forcepoint 於 2024 年連續第二年獲市調研究公司 Frost & Sullivan 評為 「全球年度最佳 DLP 公司 」
Forcepoint 在 2025 年第一季的 The Forrester Wave™: Data Security Platforms 中獲評為 [強勁表現者。
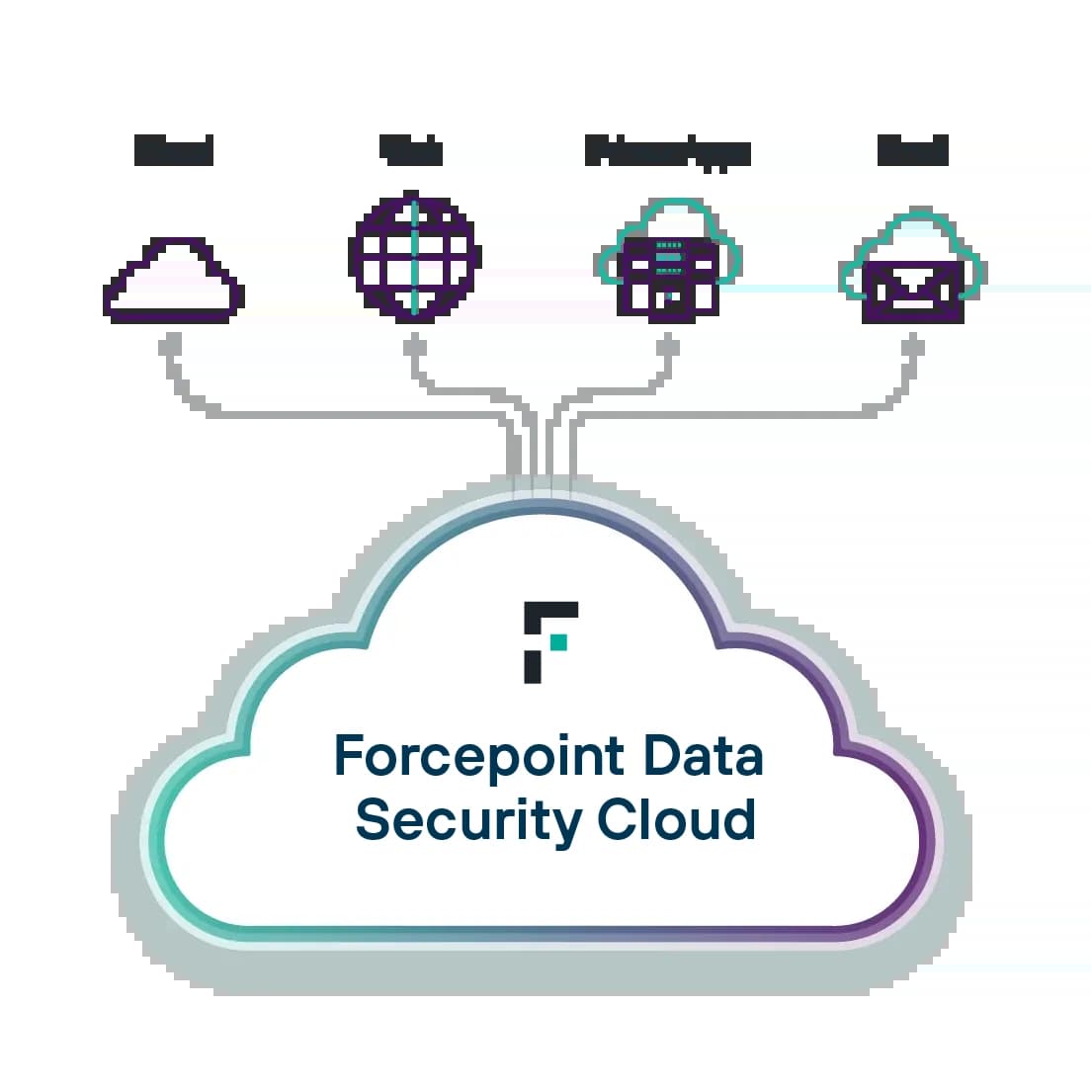
新一代的資料安全
利用 Forcepoint 隨時隨地保護資料。利用 AI 推動資料探索與分類,不僅能統一政策管理方式,還可即時因應風險,以防範外洩及簡化法規遵循。
Enterprise DLP: 透過簡單易用的集中平台,設定、擴充及自動化資料保護政策。
Forcepoint Data Visibility:全方位瞭解全組織的非結構化資料。
Data Classification: 獲得 AI 和 ML 加持,提升資料分類的精確度與效率。
RISK ADAPTIVE PROTECTION 資源
閱讀以瞭解 Risk Adaptive Protection 最佳做法




