أكثر من 12 آلاف عميل يثبتون صحة اختيارنا










































الكشف عن مخاطر المطلعين عند أقرب نقطة للكشف
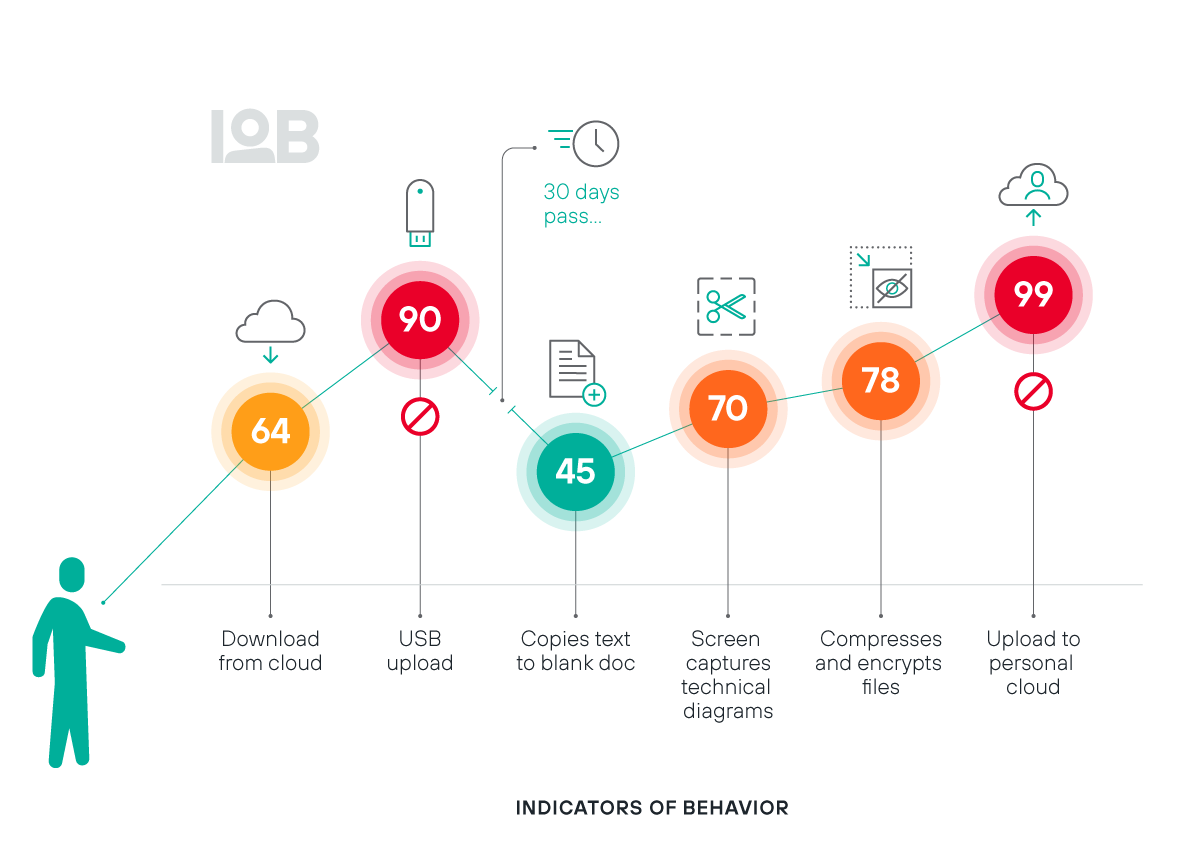
اكتساب رؤية ذات معنى في تفاعلات المستخدم مع البيانات المهمة
القضاء على النقاط العمياء الخطرة وتعزيز عرض كامل للوقت الذي يتجه فيه المستخدمون نحو سلوك محفوف بالمخاطر
فهم سلوكيات المستخدمين ونواياهم مع التسجيل المحدّث دائمًا للمخاطر
فتح قدرات المراقبة الواسعة عبر ما يزيد عن 100 مؤشر للسلوكيات (IOB)
DATASHEET
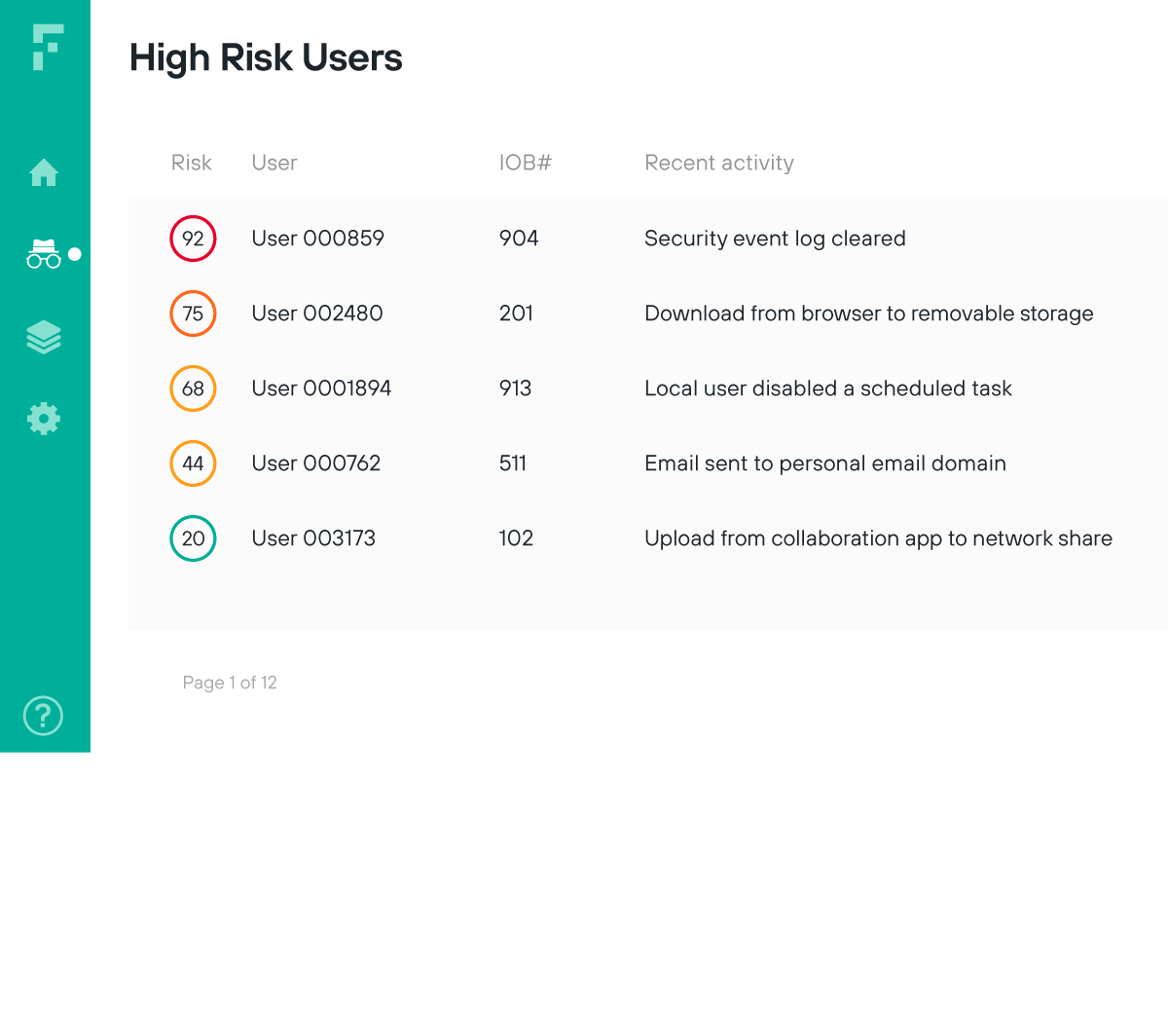
تنفيذ نموذج Zero Trust مع التحقق المستمر من صحة المستخدم
تسطيح المخاطر الواقعة من المستخدمين الخاضعين للعقوبات ومحللي التنبيهات على السلوكيات غير العادية في أقرب نقطة للكشف من أجل اتباع نهج Zero Trust حقيقي للأمان
تقييد الوصول استنادًا إلى أنشطة المستخدمين غير العادية التي قد تشير إلى التعرض للخطر
التحقق من المخاطر التي يتعرض لها المستخدم من خلال المراقبة الفورية للتفاعل المستمر بين المستخدم والبيانات
INFOGRAPHIC
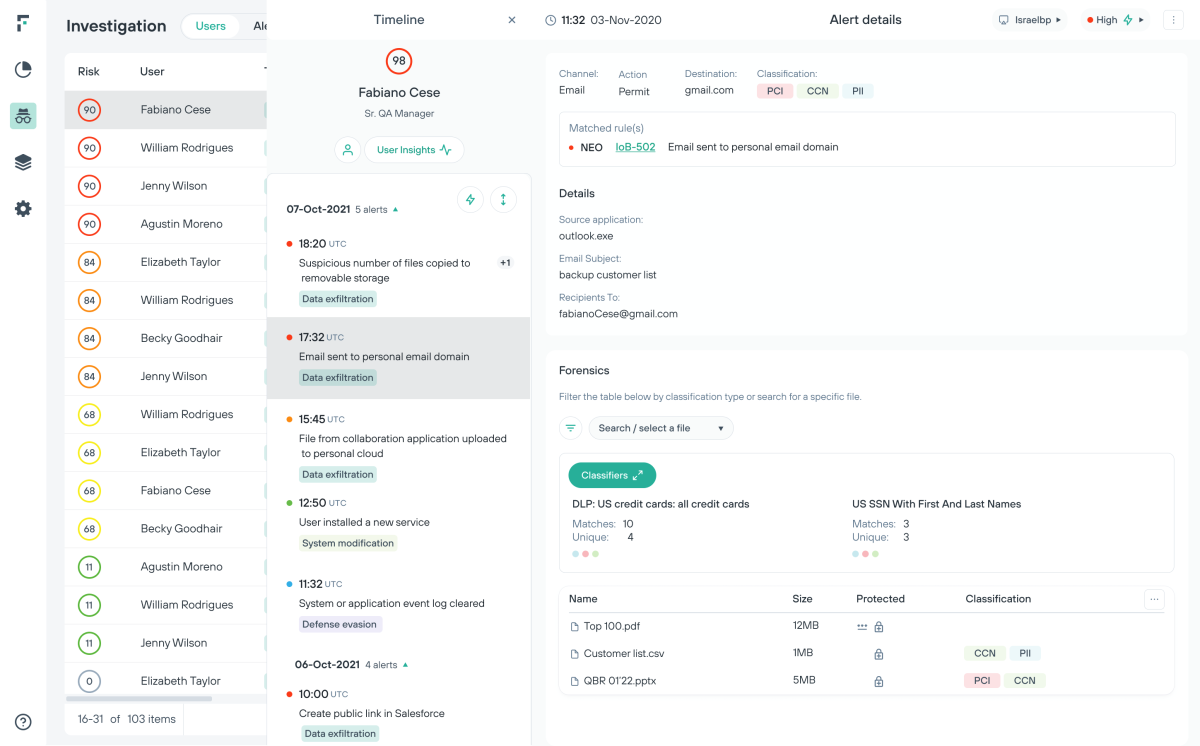
زيادة كفاءة محلل الأمان وتقليل الإجهاد الناجم عن كثرة التنبيهات
يعمل نظام Risk-Adaptive Protection على تحويل المؤسسات من نهج يركز على الأحداث إلى نهج يركز على المخاطر فيما يتعلق بأمن البيانات.
استباق حدث تسريب البيانات بخطوة من خلال تنسيق تعديلات السياسة حسب مستوى المستخدم
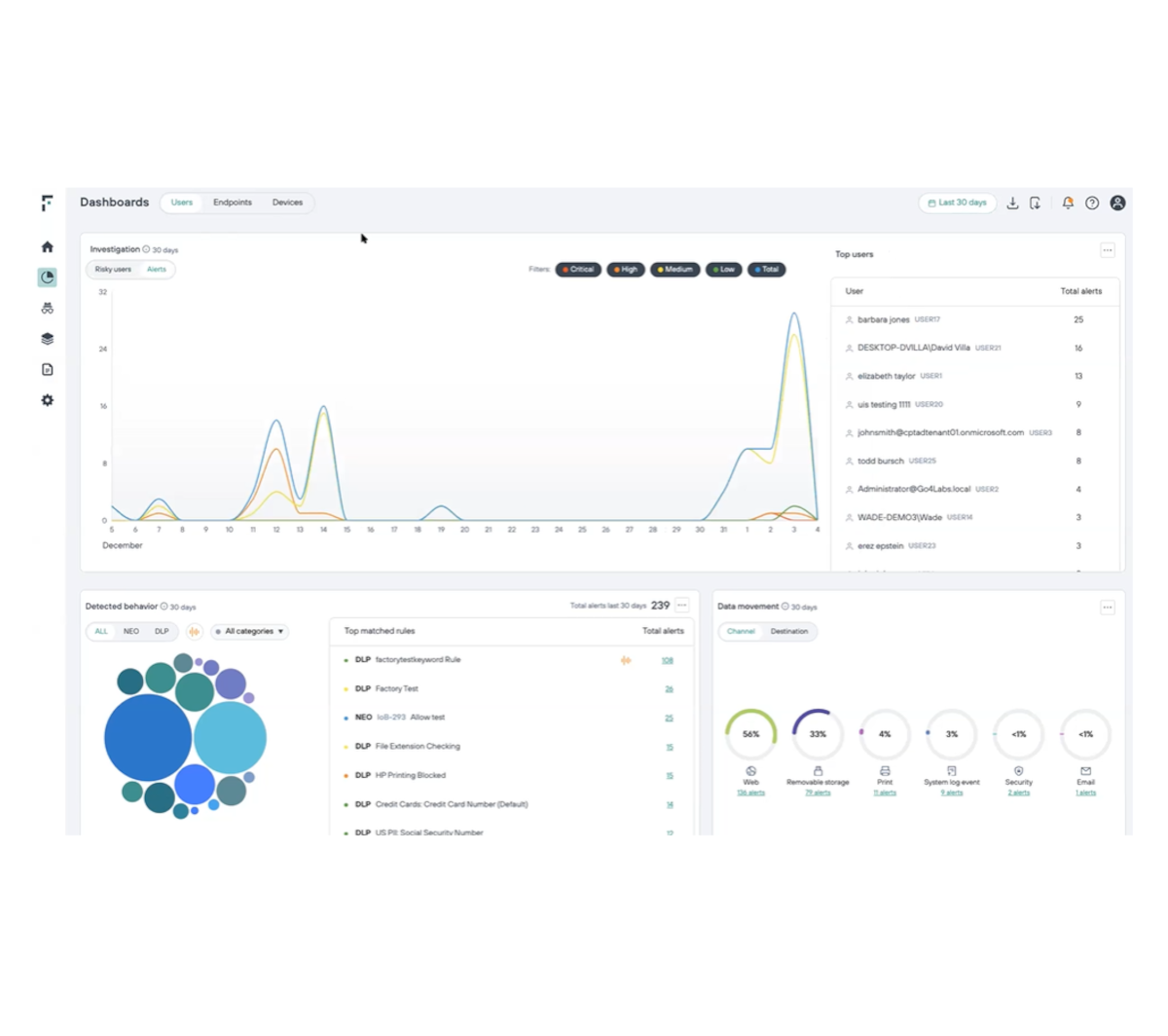
إجراء التحقيقات بفعالية وزيادة القدرة على التعلم
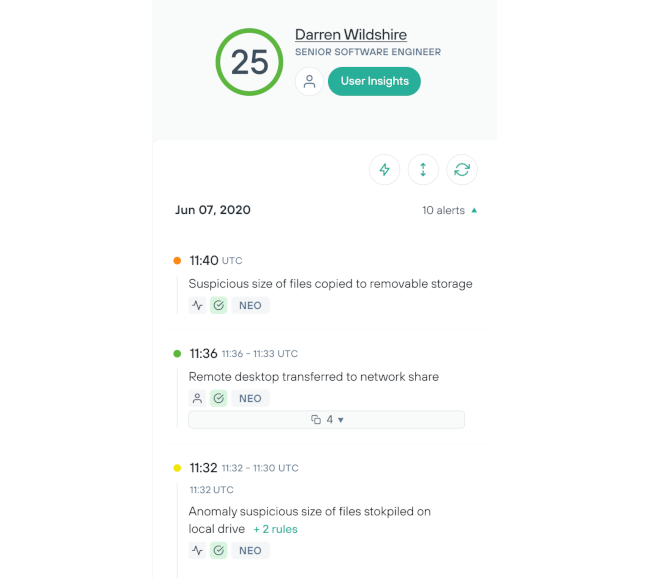
التحقيق في المخاطر من جانب المطلعين بكل كفاءة وسهولة
تقليل الحاجة إلى نقاط الاتصال اليدوية من خلال عملية التنفيذ دون مشاكل والأتمتة المخصصة.
زيادة قدرة المحللين على التحقيق في المستخدمين من خلال الأتمتة والقضاء على الإيجابيات الكاذبة
تحرير موظفيك من خلال بنية تحتية سهلة الصيانة في الخدمة السحابية ونشر وكيل على مدار 30 ثانية
الاستجابة للتهديدات الناشئة في الوقت الحقيقي
منع تسريب البيانات بتكييف سياسات الأمان تلقائيًا لمنع سلوك المستخدمين المحفوف بالمخاطر.
منع تسريب البيانات بتكييف سياسات الأمان تلقائيًا لمنع سلوك المستخدمين المحفوف بالمخاطر.
السماح للمستخدمين ذوي المخاطر المنخفضة بالوصول إلى المعلومات التي يحتاجون إليها مع تحجيم التهديدات المحتملة.
أتمتة أمن البيانات في الوقت الحقيقي بالمراقبة المستمرة لنشاط المستخدمين.


الدليل العملي لمنع تسرّب البيانات
اكتشف الخطوات الثماني المجربة والصحيحة لتطبيق حلول برنامج Data Loss Prevention (DLP) لأي مؤسسة مهما كان حجمها من خلال دليلنا العملي.
التحليلات الموصى بها.
تمت الموافقة على المستخدم
يتم تصنيف برنامج Forcepoint باستمرار ضمن أفضل موفري برامج Data Loss Prevention وبرامج أمان البيانات من قبل المستخدمين والمحللين في المجال.
تم تسمية Forcepoint شركة رائدة في IDC MarketScape: Worldwide DLP 2025 Vendor Assessment
تم اختيارForcepoint كأفضل شركة في مجال حماية البيانات من التسرّب DLP لعام 2024 من قبل Frost & Sullivan للسنة الثانية على التوالي.
ي في كصاحبة أداء قي The Forrester Wave™: Data Security Platforms، الربع الأول من عام 2025
الجيل القادم لأمن البيانات
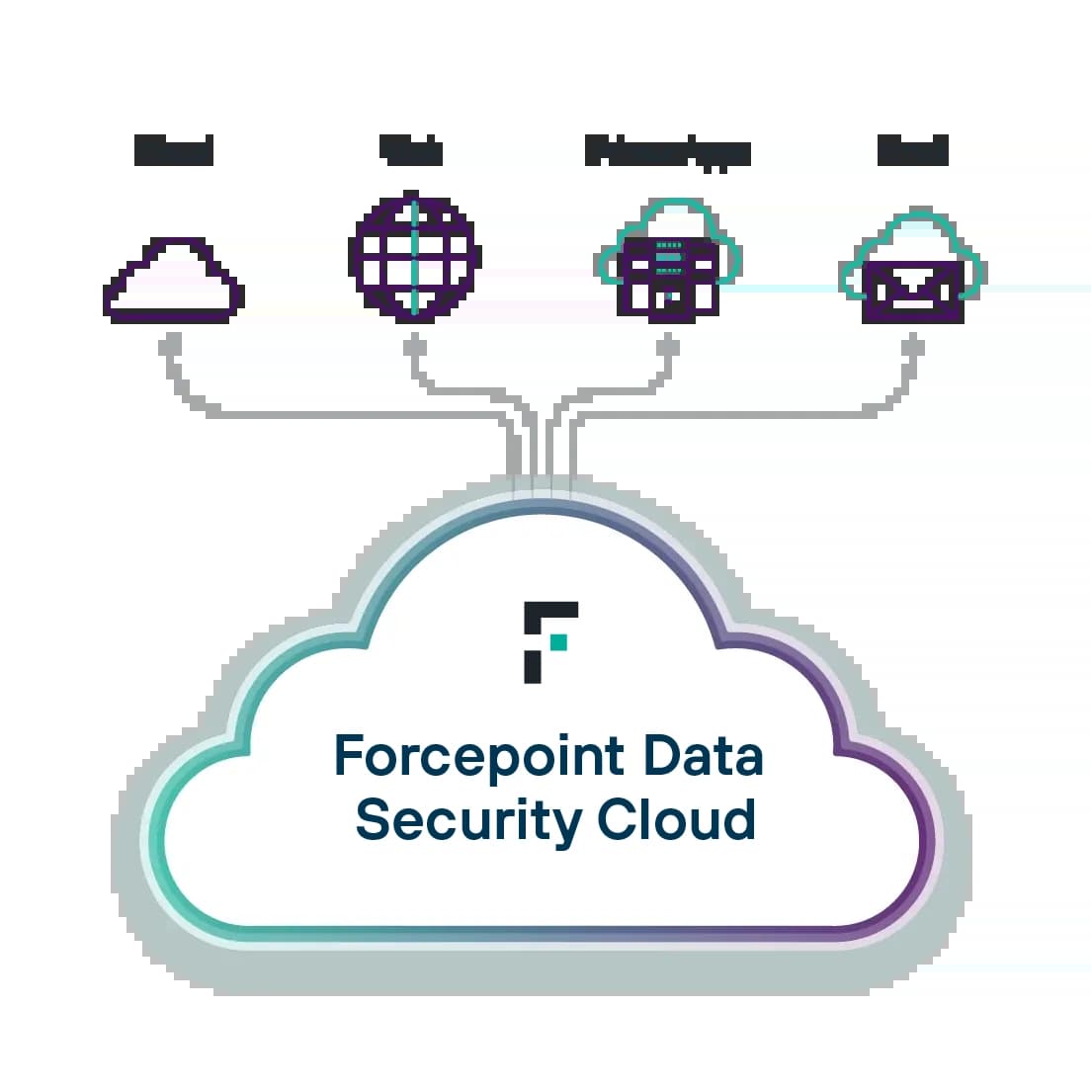
تأمين البيانات في كل مكان بواسطة Forcepoint. يمكنك منع الانتهاكات وتبسيط الامتثال باستخدام الذكاء الاصطناعي لتعزيز اكتشاف البيانات وتصنيفها، وتوحيد إدارة السياسات، والتكيف مع المخاطر في الوقت الفعلي.
Enterprise DLP: تعيين سياسات حماية البيانات وتخصيصها وأتمتها من منصة مركزية سهلة الاستخدام.
Forcepoint Data Visibility: احصل على عرض بانورامي للبيانات غير المهيكلة عبر مؤسستك.
Data Classification: تقديم المزيد من الدقة والفعالية في تصنيف البيانات بمساعدة الذكاء الاصطناعي (AI) ونماذج اللغات (ML).
موارد Risk Adaptive Protection
اقرأ عن أفضل ممارسات Risk Adaptive Protection

Data Security Everywhere - Automate Data Security Management with Risk-Adaptive Protection
مشاهدة الفيديوCompetitive DLP Risk-Adaptive Protection Feature Comparison
عرض ورقة البياناتRisk-Adaptive Protection: Personalized Automation Solution for Forcepoint DLP
قراءة ملخص الحل

