The Best DLP Software in 2026: Compare Costs and Features
0 minutos de leitura

Lionel Menchaca
In 2026, IT and security teams want clear answers: which DLP solution stops data leaks, ensures compliance and mitigates insider and external threats to structured and unstructured data?
This guide compares the best DLP software in 2026 by features, costs, deployment models and customer feedback. Forcepoint stands out with unified policy management, AI-driven classification and integration with Data Security Posture Management (DSPM) to give SecOps better context and faster response.
The Best Data Loss Prevention Solutions for 2026
Use this guide to compare features, costs and customer feedback before selecting the right data loss prevention software for your organization.
1. Forcepoint Data Loss Prevention (DLP)
The Forcepoint DLP solution prevents exfiltration of sensitive data and delivers unified policy management with centralized control of all channels or security vectors from a single policy. This allows visibility and control of your data everywhere your people work and anywhere your data resides.
Forcepoint simplifies DLP deployment and ongoing management with over 1,700+ pre-defined templates, policies and classifiers that cover the regulatory demands of 90 countries, over 160 regions and every major industry.
Key Features
- Unified Policy Management & Enforcement: Forcepoint DLP applies consistent security policies across all systems, applications, and endpoints.
Risk-Adaptive Protection:
- Forcepoint Risk-Adaptive Protection (RAP) dynamically adjusts policies in real time based on user behavior, reducing false positives and alleviating productivity concerns.
AI-Powered Data Classification:
- AI-powered data classification engine produces automated, highly accurate and efficient classification. It also easily integrates with Forcepoint DSPM to create a powerful data security combination.
Proactive Threat Detection:
- Identifies and stops data security risks before they lead to breaches and compliance violations.
User Coaching & Intent Validation:
- Provides real-time user guidance to prevent data loss and ensure secure data handling.
Comprehensive Data Flow Monitoring:
- Tracks data movement across networks, applications, and endpoints for real-time visibility.
Automated Classification & Labeling:
- Integrates with Forcepoint Data Classification (our recommendation) or third-party tools to tag and secure sensitive data.
Audit-Ready Compliance Tracking:
- Delivers detailed forensics and insights into policy violations and security incidents to streamline audits.
Flexible Deployment Options:
- Supports cloud, on-premises, and hybrid deployments to fit any business and IT requirements.
Download the DLP Comparison Table
Pros
- Prevents data loss anywhere, even offline devices
- Streamlines compliance with pre-built classifiers and templates
- Risk-adaptive enforcement reduces false positives
- One dashboard to manage all channels
Cons
- May require initial tuning in complex environments
- Potentially more than small organizations need if data sensitivity is low
Who Should Consider This Product
Enterprises in regulated industries such as finance, healthcare, government, IT services, insurance, energy and retail that need scalable, adaptive DLP integrated with broader data security posture management.
Best for: Overall
Why: Strongest all-channel coverage, unified policies, Risk-Adaptive Protection, AI Mesh classification, DSPM integration.
Customer Feedback
Forcepoint's user-friendly data security doesn’t compromise power. Their intuitive UI makes securing a multi-cloud and hybrid workforce simple while keeping us compliant. – Bulwarx, Data Security Lead
Speed is vital. Forcepoint's rapid deployment minimized disruption and secured our data and endpoints in no time. – Leading IT Services Integrator
Forcepoint's dashboard is a game-changer. We can spot misconfigured policies quickly and maintain real-time visibility across our network. – Cybersecurity Management Company
2. Symantec Data Loss Prevention (Broadcom)
Symantec DLP, acquired by Broadcom in 2019, protects sensitive data across SaaS apps, networks, and endpoints. Deployment often requires a unified server, management console, and endpoint agents.
Key Features
- Centralized incident management console
- Unified DLP policies across multiple channels
- Content inspection and user behavior analytics
- Regulatory compliance support
Pros
- Incident visibility through a central console
- Supports a policy administrator role
- Monitors email and network traffic
Cons
- Complex and resource-heavy deployment
- High overhead for incident management
- Endpoint agent setup can be challenging
- Limited SaaS DLP on endpoints
- Smaller customers cite weaker support
Who Should Consider This Product
Best for large enterprises with dedicated DLP teams and resources to manage complex environments.
Best for: Large enterprises
Why: Deep, complex deployments that require dedicated DLP teams and heavy customization.
Customer Feedback
Some customers report that deployment and incident management are cumbersome, requiring specialized staff. Smaller organizations also note that support quality is inconsistent compared to enterprise accounts.
3. Trellix Data Security (formerly McAfee DLP)
Trellix DLP protects sensitive information across its lifecycle, offering discovery, classification, centralized policy management, and compliance reporting.
Key Features
- Protection against insider risk
- Out-of-the-box compliance templates
- Centralized policy management
- Event management and reporting
Pros
- Supports multiple platforms (Windows, macOS, etc.)
- Customizable classifications
- Regulatory compliance templates
Cons
- Policy setup can be complex
- Requires experienced admins
- Higher system resource usage
- Gaps in discovery and classification coverage
Who Should Consider This Product
Organizations needing on-premises endpoint DLP with strong compliance templates.
Best for: Endpoint-heavy orgs
Why: Strong endpoint presence, on-prem-heavy environments, classic endpoint agent model.
Customer Feedback
Users appreciate the cross-platform support but report that policy configuration is time-consuming. Some also note heavy system resource use and gaps in visibility.
4. Proofpoint Enterprise DLP
Proofpoint Enterprise DLP protects against data loss across email, cloud, and endpoints, combining content, behavior, and threat telemetry.
Key Features
- Unified coverage for email, cloud, and endpoints
- 240+ customizable sensitive data detectors
- Unified alert and investigation interface
- Policy portability across channels
Pros
- Strong email and cloud focus
- Customizable alerts
- People-centric approach to data risk
Cons
- Limited query optimization
- Privacy preservation controls lagging
- Onboarding managed services can be difficult
Who Should Consider This Product
Best for email-heavy enterprises or organizations with large volumes of cloud communication.
Best for: Cloud-first teams (email + collaboration)
Why: People-centric telemetry, strong email/cloud focus, heavy use in comms-driven organizations.
Customer Feedback
Customers highlight Proofpoint’s email-centric strengths but report challenges with managed service onboarding and query optimization limitations.
5. Digital Guardian (Fortra)
Digital Guardian, now part of Fortra, provides endpoint-focused protection using agents and sensors to monitor and manage data activity.
Key Features
- SaaS availability
- Out-of-the-box dashboards
- Pre-built policies for discovery and monitoring
- Integrates with classification tools
Pros
- Scalable for enterprise data protection
- Strong reporting capabilities
- Works with existing classification tools
Cons
- Implementation delays reported
- Interface could be more user-friendly
- Heavy reliance on endpoint agents
Who Should Consider This Product
Best for organizations needing endpoint and network-focused DLP with SaaS flexibility.
Best for: Endpoint-heavy orgs
Why: Historically endpoint-focused, strong agent-based controls and reporting.
Customer Feedback
Users value scalability and reporting but cite complexity in implementation and usability challenges for non-specialist teams.
6. Microsoft Purview Data Loss Prevention
Microsoft Purview DLP is integrated into Microsoft 365, protecting sensitive data across Exchange, OneDrive, SharePoint, and Teams.
Key Features
- Pre-built compliance templates
- Machine-learning driven analysis
- Automated policy enforcement
- Cloud-native integration
Pros
- Seamless with Microsoft ecosystem
- Customizable policies
- Easy cloud deployment
Cons
- High false positives reported
- Limited endpoint coverage
- Complicated setup for large orgs
- Extra support costs may apply
Who Should Consider This Product
Ideal for Microsoft 365-centric organizations that want native DLP coverage across collaboration tools.
Best for: Microsoft 365
Why: Native across Exchange, SharePoint, OneDrive, Teams; best for M365-centric ecosystems.
Customer Feedback
Customers appreciate tight integration with Microsoft apps but often report high false positives and challenges extending coverage to endpoints.
7. Palo Alto Networks Enterprise DLP
Palo Alto Networks Enterprise DLP extends protection across firewalls, Prisma Access, and cloud apps in the Palo Alto ecosystem.
Key Features
- Unified protection policies
- Predefined and customizable detection rules
- Deployment options in cloud or on-premises
Pros
- Effective for sensitive data like PCI and PII
- Integrates with Palo Alto firewalls
- Scales across multiple sites
Cons
- Documentation gaps for maintenance
- Product complexity reported
- File categorization accuracy issues
Who Should Consider This Product
Best for enterprises already invested in Palo Alto firewalls or Prisma Access.
Best for: Large enterprises
Why: Integrated with Palo Alto firewalls and Prisma Access; strong in network-heavy security stacks.
Customer Feedback
Customers like the integration with Palo Alto’s broader security tools but mention product complexity and uneven accuracy in file categorization.
8. Netskope Data Loss Prevention
Netskope DLP is cloud-delivered, securing sensitive data across cloud, networks, endpoints, and email services.
Key Features
- Real-time monitoring by user, device, and behavior
- 40+ compliance templates
- File encryption capabilities
- Works across browsers, sync clients, and mobile apps
Pros
- Strong identity-aware monitoring
- Effective scanning and searching
- Customizable compliance templates
Cons
- Reports of detection delays
- Fail-closed issues without admin action
- Steep learning curve for new admins
Who Should Consider This Product
For customers of Netskope One SSE seeking integrated DLP.
Best for: Cloud-first teams
Why: SSE-native, identity-aware, strong across browsers, remote users, and SaaS/cloud apps.
Customer Feedback
Customers value Netskope’s real-time monitoring but report slow resolution times and a steep learning curve for new administrators.
9. Nightfall AI DLP
Nightfall AI delivers a cloud-native, API-based DLP platform designed for modern SaaS environments. It helps organizations automatically detect, classify, and protect sensitive information across platforms such as Slack, Google Drive, Jira, Confluence, GitHub, and other collaboration tools.
Key Features
- Pre-trained machine learning detectors for PII, PCI, and PHI
- API integrations with leading SaaS platforms
- Automated redaction and quarantine workflows
- Custom detectors for proprietary or industry-specific data types
Pros
- Fast, low-friction SaaS deployment (no agents required)
- Broad coverage across popular collaboration and cloud tools
- Machine learning–based detection with strong accuracy
- Scales easily for remote and hybrid teams
Cons
- Limited visibility into on-premises or endpoint data
- Fewer deep policy customization options than enterprise DLP suites
- Reporting and analytics less granular than Forcepoint or Symantec
Who Should Consider This Product
Ideal for cloud-first organizations seeking a lightweight, API-driven DLP solution to protect data across SaaS collaboration and development platforms.
Best for: AI-driven security
Why: ML-native classification, SaaS-first, strong ML detectors for PII/PHI/PCI across collaboration tools.
Customer Feedback
Customers praise Nightfall AI’s simplicity and quick setup, noting strong detection accuracy and responsive support. Some users mention a need for more advanced policy controls and richer analytics for enterprise deployments.
10. Zscaler Data Protection
Zscaler Data Protection is a zero-trust, cloud-native solution built into Zscaler’s Secure Web Gateway and Zero Trust Exchange.
Key Features
- Centralized policy management
- Real-time enforcement
- OCR to secure image files
Pros
- Real-time policy enforcement
- Prevents unauthorized transfers
- Strong Zero Trust integration
Cons
- Limited offline functionality
- Learning curve for new users
- Latency during high workloads
Who Should Consider This Product
Best for organizations already on Zscaler Zero Trust Exchange needing unified DLP.
Best for: Cloud-first teams
Why: Zero Trust Exchange integration, strong real-time cloud/web inspection.
Customer Feedback
Users like the real-time enforcement but note offline limitations and potential latency during heavy usage.
11. Endpoint Protector (CoSoSys)
Endpoint Protector by CoSoSys focuses on endpoint and device control to prevent data loss via removable media, cloud apps, and file transfers.
Key Features
- Multi-OS coverage (Windows, macOS, Linux)
- USB and peripheral control
- Real-time file transfer monitoring
- Multiple deployment models
Pros
- Strong cross-platform support
- Effective external device management
- Broad coverage of sensitive data transfers
Cons
- Some uncontrolled vectors reported
- False positives can be high
- More limited scope compared to enterprise platforms
Who Should Consider This Product
Best for organizations prioritizing endpoint and device-level control.
Best for: Endpoint-heavy orgs
Why: Multi-OS device control, USB/peripheral governance, endpoint-first focus.
Customer Feedback
Customers value the OS coverage and device controls but report higher false positives and gaps in monitoring certain data channels.
###
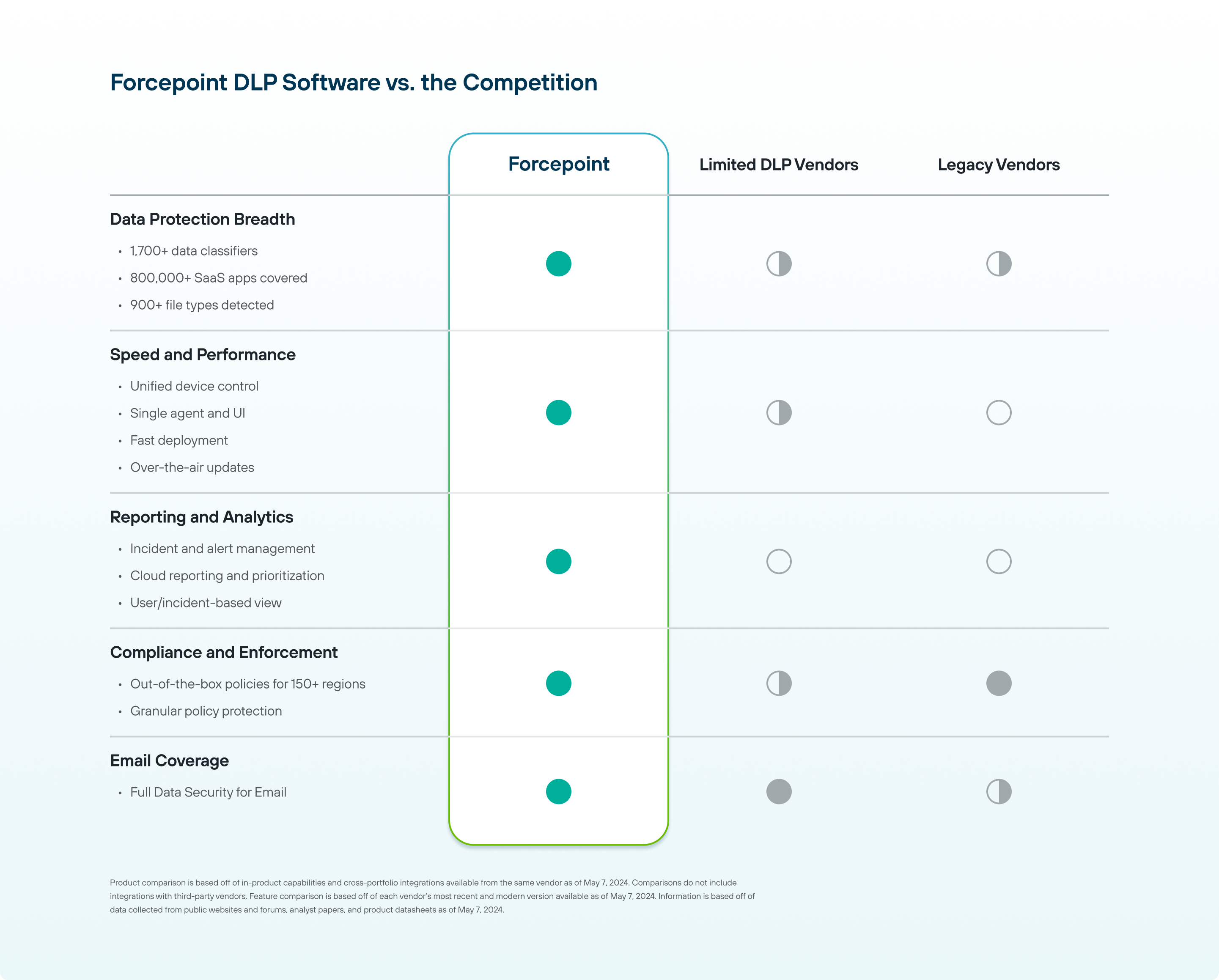
See the DLP Feature Comparison Chart below:

Fig. 1 - DLP Feature Comparison Chart #1

Fig. 2 - DLP Feature Comparison Chart #2
Understanding Data Loss Prevention (DLP) Software
What is data loss prevention (DLP) software?
Data loss prevention (DLP) software is a security tool that identifies, monitors and protects sensitive data so it does not leave the organization in an unauthorized way. It applies policies to govern how regulated and confidential information is stored, used and shared across endpoints, networks and cloud applications.
How DLP software works
DLP software discovers and classifies sensitive data, then applies policies to control how that data can move.
- For data in motion, DLP inspects traffic such as email, web uploads and SaaS activity to detect and block risky transfers.
- For data at rest, it scans file shares, databases and cloud storage to locate sensitive records and apply labels or controls.
- For data in use, it monitors actions on endpoints, such as copy and paste, printing, screenshots or transfers to USB devices, and can block or coach users in real time.
Core features to look for in DLP software
When comparing DLP software, it is important to look beyond basic blocking and alerts.
Key features include:
- Data classification and content inspection for patterns like PCI, PHI, PII and intellectual property
- Custom policy creation that aligns with regulations and internal data handling rules
- Coverage for data in motion, data at rest and data in use
- Cross-platform protection for endpoints, cloud apps, web, email and on premises systems
- Integration with SIEM, SOAR and CASB tools for richer incident context and workflows
- Reporting and analytics that surface trends in data movement and policy violations
- Centralized management so security teams can administer policies and incidents from a single console
Types of DLP software
Most DLP programs are built from three main types of coverage that can be deployed together or separately:
- Endpoint DLP focuses on laptops and desktops. It controls data in use, including saving files locally, printing, screenshots and copying data to removable media.
- Network DLP inspects data in motion over email, web and other network channels to detect and stop sensitive information from leaving the environment.
- Cloud or SaaS DLP protects data in cloud applications and collaboration tools, often working with CASB or SSE platforms to control uploads, sharing and access in the cloud.
For a more detailed breakdown of each type and where they fit, see our guide to types of DLP solutions.
How to Choose the Right DLP Software for Your Business
Match DLP coverage to your environment
Start by mapping DLP coverage to how your organization actually works. Endpoint heavy environments, such as laptop fleets or contractors working remotely, need strong endpoint DLP. Cloud first teams that rely on SaaS apps and web access need deep coverage for cloud and web traffic. Microsoft 365 centric organizations benefit from tighter integration with Exchange, SharePoint, OneDrive and Teams. Large enterprises with complex networks often need a mix of endpoint, network and cloud DLP with centralized management.
Use the “Best for” labels in the vendor list to quickly see which tools align to your environment.
Check integration with your existing security stack
Effective DLP rarely operates in isolation. Look for products that integrate with your SIEM and SOAR platforms so incidents can be correlated and automated. Integration with CASB or SSE platforms helps extend DLP policies into cloud apps and remote users. Connections to identity providers and ticketing tools make it easier to route incidents to the right teams and enforce least privilege access.
Evaluate manageability and total cost of ownership
Licensing price is only one part of DLP cost. Factor in the time required to create and tune policies, maintain infrastructure, and triage alerts. Solutions with unified policy management, reusable templates and risk based controls reduce day to day admin effort. Cloud native or hybrid deployment options can also lower infrastructure overhead and accelerate rollout to new sites or teams.
Prioritize classification accuracy and analytics
Poor classification accuracy drives false positives and user frustration. When comparing DLP vendors, look at how they classify data, whether they support advanced pattern matching and AI driven classification, and how easy it is to maintain classifiers over time. Strong reporting and analytics should help you see which users, locations and channels generate the most risk so you can prioritize improvements instead of reacting to isolated alerts.
Align DLP capabilities to your compliance and risk priorities
Finally, ensure the DLP platform supports the regulations, frameworks and internal policies that matter most to your organization. Pre built policy templates for PCI, HIPAA, GDPR or industry specific standards can shorten rollout. If you handle a lot of intellectual property or unstructured data, look for DLP that works well with data discovery and posture management so you can see exposure as well as individual incidents.
Platforms like Forcepoint DLP combine these factors with AI driven classification and integration with Data Security Posture Management (DSPM), helping security teams reduce data risk while keeping people productive.
Frequently Asked Questions about DLP Software
How does DLP software work?
DLP software works by discovering and classifying sensitive data, then enforcing policies that control how that data can be used and shared. It scans content for patterns such as payment card data, health records, personal identifiers and confidential documents. Based on policy, it can allow, block, encrypt or flag an action, and can coach users in real time when they try to move data in risky ways. Effective DLP covers data in motion, data at rest and data in use so protection is consistent across channels.
What are the main types of DLP (network, endpoint and cloud)?
There are three primary types of DLP coverage. Network DLP inspects data in motion over email, web and other network channels to detect and stop sensitive information leaving the environment. Endpoint DLP runs on laptops and desktops to control data in use, including saving, printing, screenshots and copying to removable media. Cloud or SaaS DLP protects data in cloud applications and collaboration tools, often working with CASB or SSE platforms to manage uploads, sharing and access.
What is endpoint DLP?
Endpoint DLP focuses on protecting data on user devices such as laptops and desktops. It monitors how people interact with data in use, including copying content, printing, taking screenshots and moving files to USB devices or synced folders. Endpoint DLP is critical for remote and hybrid workforces because it enforces data loss prevention policies even when users are off the corporate network. Platforms like Forcepoint DLP apply consistent endpoint policies alongside network and cloud controls so users are protected wherever they work.
What are the key features of DLP software?
Key DLP features include data discovery and classification, so sensitive content is identified accurately across systems. Most mature platforms support custom policy creation that aligns with regulations and internal data handling rules, along with coverage for data in motion, data at rest and data in use. Centralized policy and incident management, integration with SIEM, SOAR and CASB tools, and detailed reporting and analytics are also critical to reduce noise and support audits. Cross platform protection for endpoints, cloud applications, web and email helps security teams apply one set of rules everywhere.
What are the main use cases and benefits of DLP?
Common DLP use cases include preventing accidental data leaks, stopping malicious exfiltration of sensitive files and protecting regulated data such as PCI, PHI and PII. Organizations also use DLP to secure intellectual property, govern data in cloud collaboration tools and support remote and third party workers. The benefits of DLP include reducing the likelihood and impact of data breaches, improving compliance, increasing visibility into where sensitive data lives and how it moves and helping people make safer decisions without slowing the business. Modern platforms like Forcepoint DLP combine these benefits with AI driven classification and contextual analytics so teams can prioritize and remediate the highest risks first.

Lionel Menchaca
Leia mais artigos de Lionel MenchacaAs the Content Marketing and Technical Writing Specialist, Lionel leads Forcepoint's blogging efforts. He's responsible for the company's global editorial strategy and is part of a core team responsible for content strategy and execution on behalf of the company.
Before Forcepoint, Lionel founded and ran Dell's blogging and social media efforts for seven years. He has a degree from the University of Texas at Austin in Archaeological Studies.
 IDC MarketScape: Worldwide DLP 2025 Vendor AssessmentRead the Report
IDC MarketScape: Worldwide DLP 2025 Vendor AssessmentRead the Report
X-Labs
Receba insights, análises e notícias em sua caixa de entrada

Ao Ponto
Cibersegurança
Um podcast que cobre as últimas tendências e tópicos no mundo da cibersegurança
Ouça Agora