Navigating NIS2: The Crucial Role of Risk Management and Comprehensive Data Protection
Part 2 of our NIS2 Series
0 min read

Raddad Ahmad
In our previous post, we explored the evolving landscape of regulatory compliance, with a specific focus on the NIS2 Directive and its paramount importance in the realm of cybersecurity. Today, we continue our journey in this series, building upon the foundation in the first installment and embarking on uncharted territory. Our compass for this leg of the journey? Risk management and how it holds the key to a secure and resilient digital future.
Risk Management: A Shield Against Cyberattacks
Risk management is not a one-time task but an ongoing process that should be reviewed and updated regularly. It adapts to the changing environment and the ever-evolving threat landscape, ensuring organizations stay one step ahead. Here's why effective risk management matters:
- Reduced risk of cyberattacks: Through proactive identification and mitigation of vulnerabilities. It is your first line of defense against digital threats.
- Improved cybersecurity resilience: It is about not just preventing breaches but also swiftly recovering from them when they occur.
- Reduced costs: Cyberattacks come with hefty price tags, from direct monetary losses to hidden costs like reputation damage and downtime. Effective risk management can reduce these costs—preserving your bottom line and brand reputation.
Risk Management and NIS2: A Mandatory Connection
NIS2, the second iteration of the EU-wide cybersecurity legislation, has broadened its scope while introducing more stringent security requirements. It mandates the following elements of risk management for organizations within its reach.
- Identifying assets and quantifying their value: Cataloging all assets vulnerable to cyberattacks and evaluating their value to gauge potential impacts.
- Identifying threats and vulnerabilities: Recognizing the threats that could exploit your assets, such as malware, ransomware, and phishing, while pinpointing system vulnerabilities.
- Assessing risks: Understanding the likelihood and potential impact of each cybersecurity risk to prioritize risk mitigation.
- Implementing risk mitigation measures: Employing a range of measures, from technical controls like firewalls to operational ones like security awareness training and incident response plans.
- Monitoring and reviewing risks: Regular monitoring and reviews ensure that risk management processes remain effective and adaptable.
At Forcepoint, data is not just a crucial asset—It represents the heart and soul of every organization's operation. Our pioneering data protection solutions are second to none, providing top-notch tools to safeguard your most critical assets. As NIS2 and other regulations set new cybersecurity standards, you can trust Forcepoint as a partner in securing your data and ensuring uninterrupted operations. Cybersecurity is not just about compliance; it is about safeguarding your future. At Forcepoint, data always comes first.
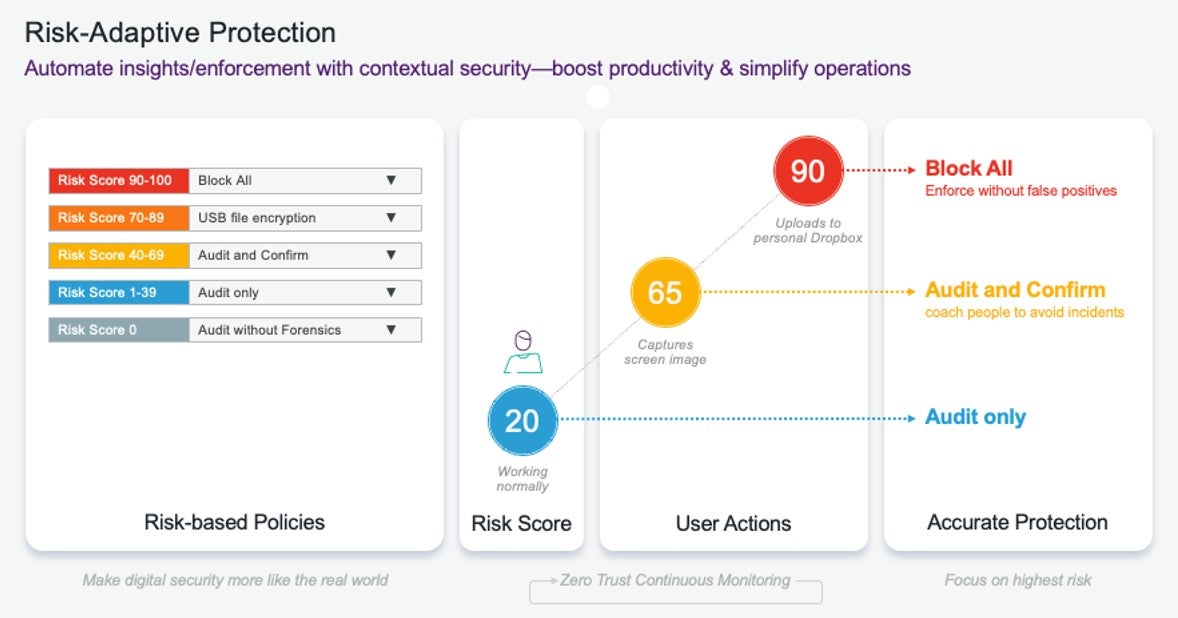
Our Risk-Adaptive Protection solution aligns with risk management requirements. By prioritizing user behavior and data interaction, it offers a behavior-centric approach to data security, resulting in:
- Enhanced employee productivity through personalized data security, allowing low-risk users to continue as usual while restricting high-risk user activities
- Reduced false positives thanks to a graduated policy enforcement based on risk levels, preventing alert overload for practitioners
- Secure collaboration on cloud applications by providing insights into user engagement with cloud data
- Efficient and straightforward risk investigation for insider threats
Your data is widespread and often uncharted. With data residing across data centers, multiple clouds, and numerous devices, gaining visibility becomes challenging. IDC estimates that 80% of global data is unstructured, with 90% unanalyzed. This unseen data presents risks. Forcepoint Data Visibility overcomes these challenges by applying self-learning AI and ML to automate finding, categorizing, and classifying data, regardless of whether the data is stored in the cloud or on-premises.
As compliance demands and data breaches grow, it is imperative to continuously monitor all data, whether on-premises or in the cloud. Forcepoint Data Visibility, provides a holistic view enabled by self-learning AI and ML, enabling ongoing discovery, classification, monitoring, and protection. This 360° perspective, with the added benefit of AI and self-learning capabilities, minimizes data loss, reduces compliance risks, and cuts costs linked to breaches and non-compliance
Our commitment to comprehensive cybersecurity includes NGFW and IPS, providing advanced threat detection and prevention capabilities. NGFW inspects traffic at a granular level, blocking malicious activity in real-time, while IPS actively monitors network traffic, detects threats, and takes immediate action, forming a robust defense mechanism to reduce the likelihood and minimize the potential impact of cybersecurity risks.
In today's rapidly evolving cybersecurity landscape, more is needed to comply with regulations. You need a forward-thinking, agile solution that can adapt to the challenges of tomorrow. Forcepoint's data-first SASE solution, driven by Forcepoint ONE, is designed to provide you with the security, simplicity, and flexibility you need to thrive in the digital age. Let us be your partner in securing your data and empowering your organization for success. Your data security is our priority, and we are committed to making it simpler, more efficient, and more robust than ever.
Stay tuned for our next post where we will cover Incident and Response Management.

Raddad Ahmad
Read more articles by Raddad AhmadRaddad is the EMEA Solution Architect Manager at Forcepoint. With 17 years of experience in deep technical operations, his expertise lies in architecting enterprise solutions that deliver comprehensive cybersecurity measures. This experience has enabled him to facilitate innovative business strategies, fundamentally transforming organizations' operations. My daily fuel consists of a hearty diet of security and cloud technologies.
- Incident Management in NIS2
In the Article
 Incident Management in NIS2Read Part 3
Incident Management in NIS2Read Part 3
X-Labs
Get insight, analysis & news straight to your inbox

To the Point
Cybersecurity
A Podcast covering latest trends and topics in the world of cybersecurity
Listen Now