Hackers Targeting NATO Nations - Unravelling Russia’s Latest Cyber Trap
0 min read
Forcepoint X-Labs
In an increasingly high-tech, connected world, cybersecurity continues to be the most significant challenge to maintain global stability.
Recent events have again brought attention to Russian hackers sophisticated cyber traps. Russia’s involvement in the cyberattacks has raised obvious concerns with all NATO nations and demand an urgent response to keep countries and individuals safe.
By studying this latest development in cyber warfare, we can gain insights into the constantly evolving threat landscape. The Forcepoint X-Labs team have delved into the complexities of Russia’s latest attack on Ukrainian Embassy employees, exposed the tactics used as well as how best to mitigate these attacks moving forward and explore the potential ramifications for NATO Nations.
The Russian BMW Bait
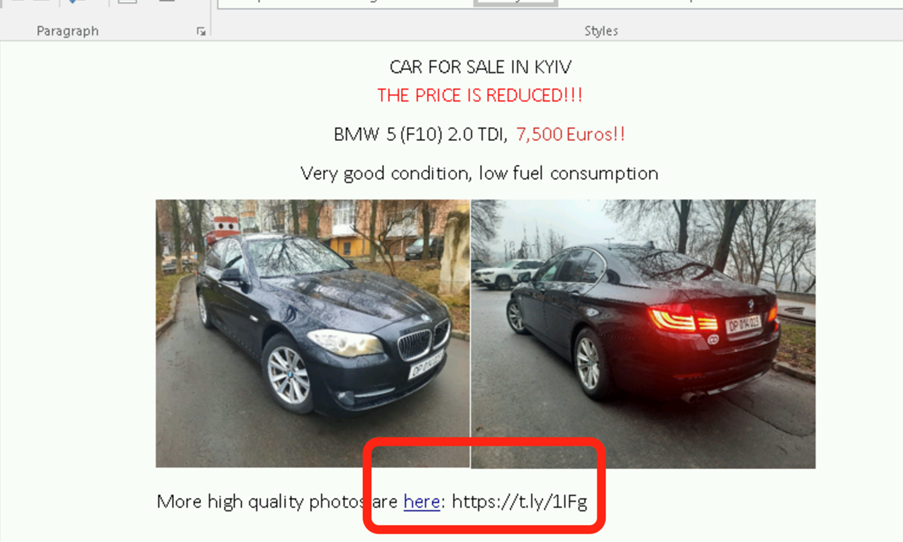
The Russian attack consists of two key stages. The first is a Word document that contains an ad for an innocent Car Flyer; A BMW that had been sent out firstly by a Polish Diplomat that was intercepted by APT29 (Cozy Bear). Cozy Bear copied this Ad (see figure 1) and laced it with a link to higher quality photos:
If you follow the link, there is an ISO that is dropped to the disk. If you click on the ISO itself, it mounts on a drive locally and consists of the following files (figure 2):
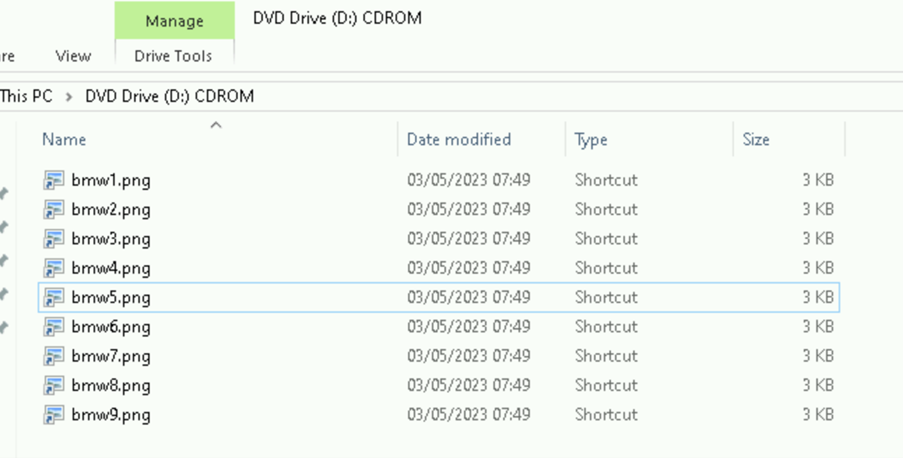
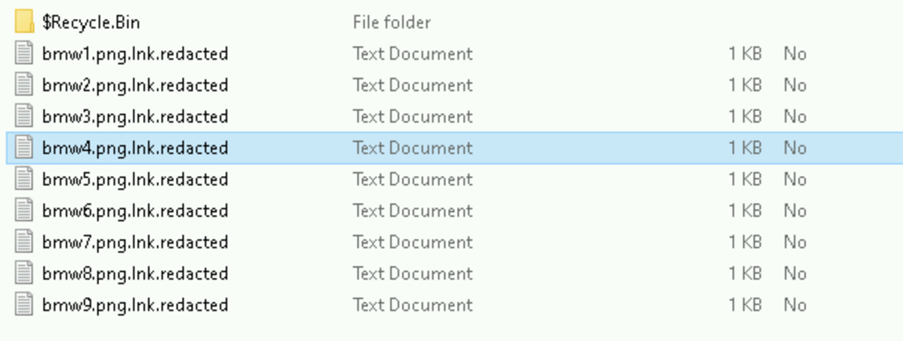
These look like standard PNG files, right? However, they are not. The PNG files are actually shortcut files (LNK) files that Forcepoint has blogged since 2010 about the potential pitfalls of LNK files.
If you follow any one of the links, they are all the same, with one minor difference – they all link to a slightly different PNG file embedded within the ISO file itself… e.g if you were to click on bmw1.png you will see the first picture of the BMW appear in your photo viewer, with one final twist.
If you view the properties on the LNK file itself, you’ll see the following (figure 3):
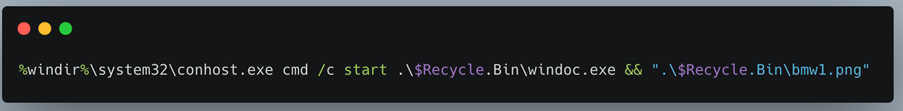
The above command consists of three key parts. The first is a call to Conhost. Conhost is the core windows Console Host and this is used to launch two commands (https://learn.microsoft.com/en-us/windows/console/definitions#console-host) . Secondly, it is launching “Windoc.exe” which is the embedded malware in a hidden folder called $Recycle.Bin within the ISO container itself. Secondly, it is launching the bmw1.png using the default photo viewer.
This means that if you click on the shortcut in Windows, you will see the image of the BMW for sale appear, and seemingly nothing else will happen, however the Spyware installs itself in the background. On the Forcepoint managed windows device, we see an application error, likely due to not meeting the correct platform targets for the malware created by APT29 (Cozy Bear) (figure 4):
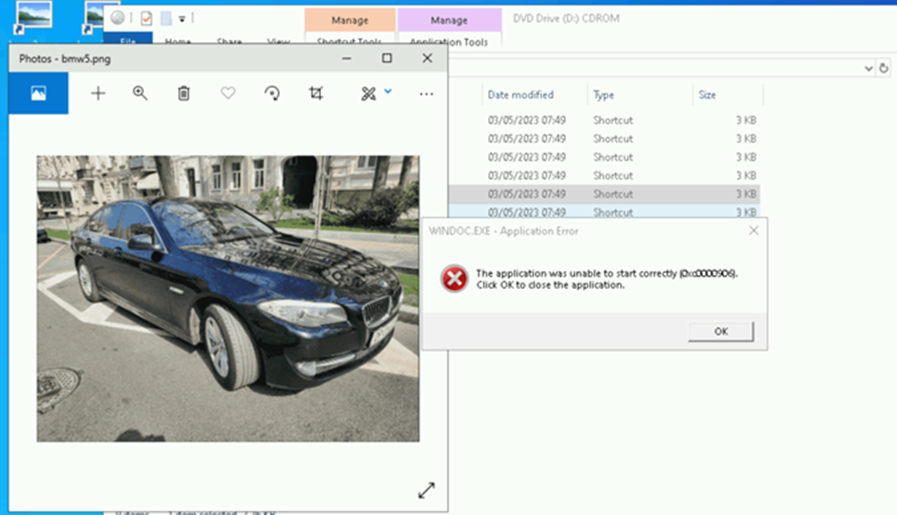
The Russian BMW Bait vs Forcepoint’s iX Appliance
Defending this attack is very simple with an out of the box information eXchange (iX) Appliance. If you send the file using the File Transfer Utilities [1], the iX appliance will respond to the ISO upload with an error and an audit log event would be sent to a SIEM (figure 5):

This is because Zero Trust Content Disarm and Reconstruction (CDR) and the iX appliance does not support ISO files by design.
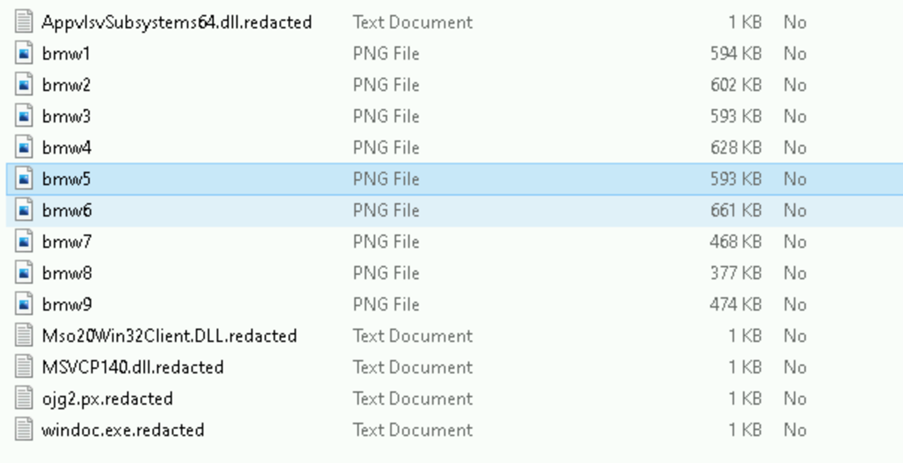
However, Forcepoint does recommend converting any ISO files to ZIP file extensions so they can be cleaned. So, let’s play this scenario out with the malware. If we send the ZIP variant of the ISO file, the following files (figure 6) are cleaned and delivered to the destination:
We can see from this, all LNK files are redacted as they are not images. If we go into the hidden folder, there are the five valid PNG files with some DLL files and an Executable. All the files apart from the PNG files have also been redacted (figure 7):
The PNG files themselves have been cleaned and are free from malware. The entire ZIP (and the entire attack in general) is now clean from malware and can be interacted with Safely within any corporate or secure network.
Storm -0978 Attack (CVE-2023-36884)
The details surrounding the most recent discovered zero-day attack, CVE-2023-36884 are still unclear. However, the attack appears to use a new zero day attack vector within Microsoft Office documents, however, Blackberry researchers have hinted at it being another variation of the Follina Attack.
Impact on Governments and Embassies
These attacks, and those similar, have a significant impact on not just NATO Governments but all Governments across the world.
Impacts that include;
- Disruption to Government Operations
- Devaluation of Public Trust
- National Data Security Breachers
- Vulnerability for Manipulation and Government Impact
- Financial Consequences
The far-reaching implications for governments showcase the importance of prioritizing cybersecurity and robust defense strategies to mitigate these threats and safeguard nations.
Defenses that work off prevention instead of the standard detection technologies, like Forcepoint’s Zero Trust CDR offer significant advantages. Zero Trust CDR is a game-changer for mitigating against the threat of even the most advanced zero-day attacks and exploits.

Forcepoint X-Labs
Read more articles by Forcepoint X-LabsThese posts are based on research done by Forcepoint's X-Labs.
In the Article
X-Labs
Get insight, analysis & news straight to your inbox

To the Point
Cybersecurity
A Podcast covering latest trends and topics in the world of cybersecurity
Listen Now