The President's Memorandum: Moving the US Government Toward Zero Trust Cybersecurity Principles
0 min read

Last year, President Biden's administration promoted the enhancement of Federal Government Cybersecurity practices through publishing the Executive Order on Improving the Nation's Cybersecurity. In addition to the broader adoption of secure cloud computing, there was a call for federal agencies to adopt a Zero Trust approach to mitigate increasingly sophisticated threats.
Recently, President Biden's administration has announced a new directive that galvanizes the United States Government to make serious progress toward attaining a Zero Trust Architecture by the end of Fiscal Year 2024. The goals are guided by the Zero Trust Maturity Model developed by CISA and OMB, which identifies five complementary areas of effort (Identity, Devices, Networks, Applications and Workloads, and Data), with three overlying principles that are applied across these areas (Visibility, Analytics, Automation and Orchestration, and Governance).
For Federal Government organizations to achieve an optimal Zero Trust state, visibility, analytics and automation must be the foundation applied across all five areas, as pictured below.
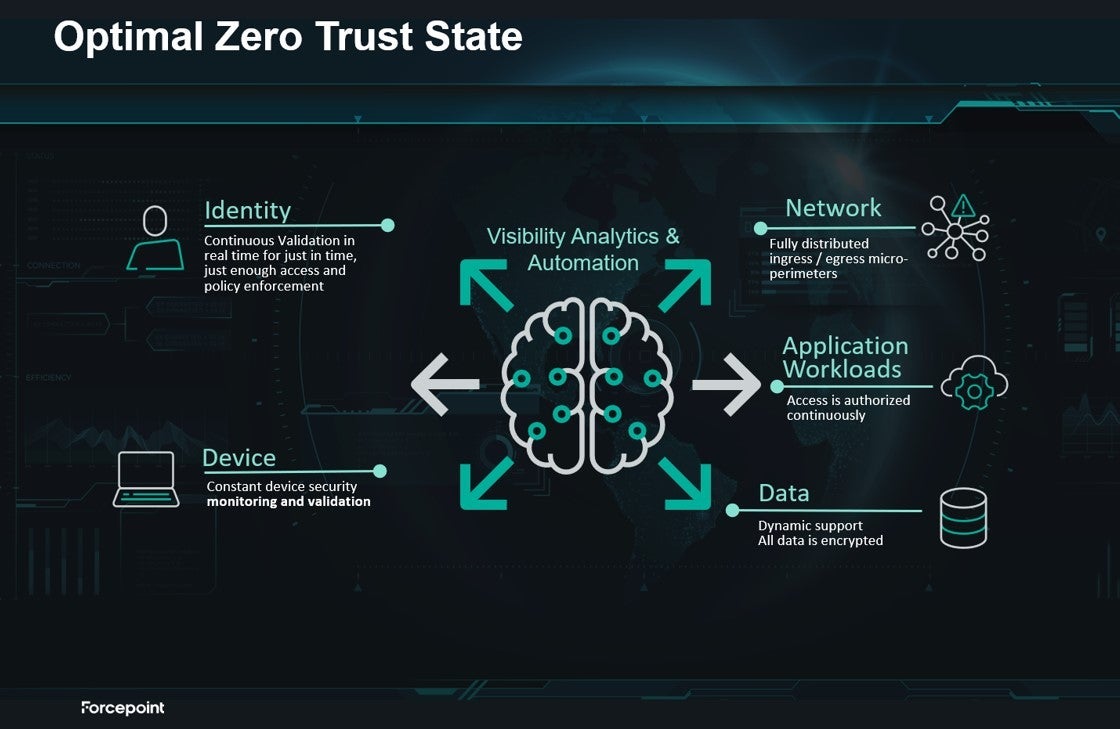
Next Steps for Government
By February 26th, agencies must identify a Zero Trust strategy implementation lead for each agency, tasked with organizing, planning, and implementing efforts. By March 28th, agencies must build upon the updated OMB policy's existing plans for zero trust. Then OMB policy requires agencies to achieve a Zero Trust security goals list by the end of FY2024. Those goals align with the zero trust maturity model developed by CISA and focus on the five pillars identified by CISA, namely, identity, devices, networks, applications and workloads, and data.
Achieving these lofty goals is likely to be costly; however, OMB advised: "Agencies should internally source funding in FY22 and FY23 to achieve priority goals, or seek funding from alternative sources, such as working capital funds or the Technology Modernization Fund."
Outside of this guidance, it will be necessary for the Federal Government to align the FITARA scorecards with these new Zero trust milestones, as many of them predate the modern Zero Trust/Cloud era.
Forcepoint Zero Trust Solutions
Forcepoint Zero Trust solutions bring together data security, network, web, and cloud security; threat protection; advanced monitoring; and Zero Trust control to empower agencies to use data where and how your people need it safely. Our mission is to simplify security and protect data wherever it resides. Integrating with your existing security, Forcepoint leverages real-time knowledge of who is on your network what they can access, ensuring data on the network is safe and automatically adapting policies to control the risk of individual users. This enables Federal leaders implementing Zero Trust to go beyond compliance to achieve centralized visibility, meaningful access controls, and continuous monitoring.
Want to learn more? Schedule a demo today.
- Defining Zero Trust in the Wake of the Biden Administration’s Cybersecurity Executive Order
In the Article
 Defining Zero Trust in the Wake of the Biden Administration’s Cybersecurity Executive OrderRead the Blog Post
Defining Zero Trust in the Wake of the Biden Administration’s Cybersecurity Executive OrderRead the Blog Post
X-Labs
Get insight, analysis & news straight to your inbox

To the Point
Cybersecurity
A Podcast covering latest trends and topics in the world of cybersecurity
Listen Now