12K+ customers couldn't be wrong










































Forcepoint DLP Software Sets the Standard
Forcepoint is synonymous with Data Loss Prevention due to its well-known, mature platform, extensive classifier and template library, and unified approach to policy management. Download the chart to see how Forcepoint DLP software compares with other vendors.
Data Protection
20%
40%
60%
80%
100%
Forcepoint
Legacy Vendors
Limited DLP Vendors
Why Forcepoint is a Top-Rated DLP Vendor
Prevent Data Loss Anywhere
Monitor and block security incidents in real time wherever users interact with data.
Streamline Compliance Worldwide
Streamline policy configuration and management with 1,700+ classifiers and policy templates to identify and secure PII and PHI.
Adapt to Risk in Real Time
Contextualize user behavior to forecast risk and automatically adjust policies to prevent security incidents before they happen.
Unify Configuration and Reporting
Create, manage and report on policies for cloud, web, email and endpoint from one platform and dashboard.


The Practical Executive's Guide to DLP
Discover how DLP software solutions work with our Practical Executive's Guide to DLP. Find out what DLP excels at, explore the eight critical steps to implementing DLP software and get unique insights on how to generate value quickly from your newly adopted DLP.
DLP Benefits That Go Beyond The Data



Our patented fingerprinting technology and advanced AI mesh classification engine provide unmatched accuracy in identifying and classifying sensitive data, even in complex formats and custom documents.

Protect data across SaaS applications, web traffic, email communications, endpoints, and network channels with a unified approach that eliminates security gaps.

Reduce administrative burden with intuitive dashboards, automated incident response workflows, and real-time alerts that prioritize the most critical issues.
How Forcepoint Sets the Standard for DLP Solutions



Leverage artificial intelligence to discover, classify, and monitor structured and unstructured data with highly accurate enforcement that reduces false positives and adapts based on context and user behavior.

Control how sensitive data is shared with ChatGPT and other generative AI platforms, allowing organizations to embrace AI transformation while preventing unauthorized data exposure and maintaining compliance.

From GDPR to HIPAA, Forcepoint DLP automatically adheres to your industry’s requirements.
DLP Deployment:
In the Cloud or On-Premises
Deploy Forcepoint DLP in the cloud (SaaS) or on-premises. With implementation support from the Forcepoint professional services team, your organization can see time-to-value in as few as six weeks!


Watch Video
A Cybersecurity Alliance Safeguarding Latin America’s Digital Future
Globaltek Security has spent over 25 years partnering with Forcepoint to deliver scalable, AI-powered cybersecurity solutions—centered on data loss prevention and secure web access.
Secure Data Everywhere with Forcepoint Data Loss Prevention
Users work with data everywhere, and your data security software must account for that. Without comprehensive
coverage, organizations expose themselves to compliance violations and unnecessary data risk.
Forcepoint DLP delivers unified visibility, adaptive control and automated protection across all your critical channels,
backed by two decades of leadership in data security and the trust of enterprises around the world.
Our Customer Stories
Our Customer Stories





"We knew we needed data security that could perform at the highest level while integrating seamlessly into our current solutions. Forcepoint was the clear choice - not just for its capabilities but for the trust we've built with their team over time."
Read Customer StoryAnalyst recommended.
User approved.
Forcepoint is consistently ranked among the top Data Loss Prevention software solutions and data security software providers by users and industry analysts.
Forcepoint has been named a Leader in the IDC MarketScape: Worldwide DLP 2025 Vendor Assessment.
Forcepoint named the 2024 Global DLP Company of the Year for the second consecutive year by Frost & Sullivan.
Forcepoint recognized as a Strong Performer in The Forrester Wave™: Data Security Platforms, Q1 2025.
Stay Informed to Prevent Data Loss
Frequently Asked Questions
What is Data Loss Prevention (DLP)?
Data Loss Prevention (DLP) refers to a set of technologies and strategies designed to prevent sensitive data from being lost, misused or accessed by unauthorized users. Forcepoint DLP protects data in motion, at rest and in use—across endpoints, networks and cloud environments—to ensure your critical information stays protected. Our solution combines advanced analytics and policy enforcement to help stop data breaches.
How does DLP work?
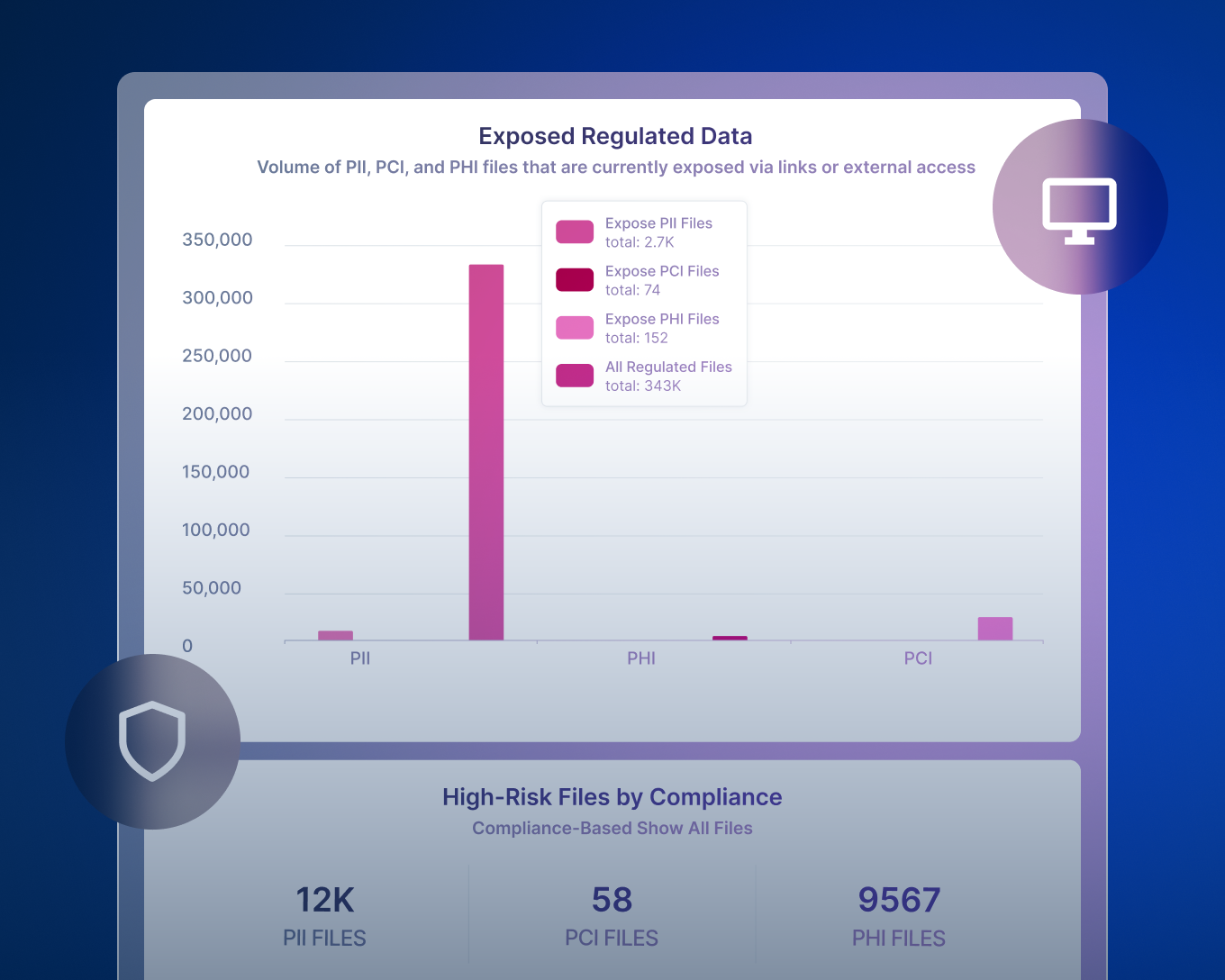
Data Loss Prevention (DLP) tools tag and monitor sensitive data to enforce policies that prevent it from being lost, stolen or misused. DLP scans data at rest (file shares, SharePoint, OneDrive), in motion (email, web, SaaS uploads) and in use (copy/paste, printing, screen capture) to detect regulated data like PII, PHI, PCI and intellectual property, such as images and blueprints.
DLP allows organizations to create policies that cover certain types of data, applications or sets of users and limit potentiially risky actions that could lead to a data leak or breach. DLP solutions vary in enforcement depending on the severity of the incident, including blocking, quarantining, encrypting or coaching users when policies are violated.
What is a DLP policy?
A DLP policy is a set of conditions that define how sensitive data should be handled within an organization. These policies help prevent unauthorized access, accidental leaks or intentional data exfiltration. With Forcepoint DLP, you can create customizable policies tailored to your business needs, ensuring data is protected across endpoints, networks and cloud environments.
How do DLP policies work?
DLP policies define how data should be handled based on its sensitivity, user roles and regulatory requirements. With Forcepoint, policies are customizable. Our policy engine also helps with maintaining global compliance standards like GDPR and CCPA.
What is DLP software?
DLP software is a security solution that helps organizations prevent the loss of sensitive and valuable information by ensuring that data assets are adequately protected, stored and used.
What is a DLP system and how do they work?
A DLP system is a comprehensive solution that helps prevent data breaches by monitoring, detecting and blocking the unauthorized movement of sensitive data. Forcepoint uses artificial intelligence to discover, classify and monitor structured and unstructured data with highly accurate enforcement that reduces false positives and adapts based on context and user behavior. Forcepoint’s unified approach to policy enforcement ensures consistent protection across all data channels.
What are the capabilities of DLP?
DLP can help your organization stay ahead of evolving threats, ensure regulatory compliance and protect sensitive data effectively and efficiently. Capabilities include policy creation and enforcement, incident response and reporting, compliance and regulatory support and more.
Do organizations need DLP?
Absolutely. If your organization handles Personally Identifiable Information (PII), Protected Health Information (PHI), Payment Card Information (PCI), intellectual property or operates in a BYOD environment, DLP is essential. Forcepoint DLP helps you prevent accidental leaks, insider threats and external attacks—protecting your brand, customers and bottom line.
What is data leakage?
Data leakage is the unauthorized or unintentional transmission of sensitive data outside your organization. This can happen through email, cloud apps, removable media or even printed documents.
What are best practices for implementing DLP?
Forcepoint recommends the following best practices:
Identify and Assess: Identify where your sensitive data resides and how it flows.
Classify Data: Use automated tools to label data based on sensitivity and compliance needs.
Establish Policies: Define clear rules for how data can be accessed, shared and stored.
Centralize Oversight: Avoid fragmented DLP efforts by unifying policy management across departments.
Train Employees: Educate users on data handling best practices and reinforce with real-time coaching.
What is the difference between network, endpoint and cloud DLP?
When people talk about the different types of DLP, they typically mean network DLP, endpoint DLP and cloud DLP.
Network DLP monitors and controls data in motion across the network
Endpoint DLP protects data on individual devices
Cloud DLP secures data stored in or moving through cloud services such as Microsoft 365 or Google Workspace
The main differentiator for Forcepoint DLP is that it unifies all three types of DLP under a single policy engine and console. The same classifiers and policies can be applied across endpoints, on-prem networks and cloud apps, including SaaS and GenAI environments, via Forcepoint CASB API integrations. This gives you consistent rules, incident views and risk scoring across web, email, endpoint and cloud channels, instead of managing three separate DLP systems.
What is endpoint DLP?
Endpoint DLP is Data Loss Prevention software that runs directly on user devices (laptops, desktops, sometimes mobile) to protect data in use and data at rest on the endpoint. It can see and control activities like copy/paste, save-as, printing, screen capture and writing to USB or other removable media - and Forcepoint DLP works even when the device is off the corporate network.
Forcepoint DLP is designed specifically to stop data loss that originates at the endpoint, whether accidental or malicious. It monitors real-time traffic and user actions inside applications, applies centrally-defined DLP and discovery policies, and can block, encrypt, quarantine or require justification when users attempt risky actions such as copying sensitive files to external drives or posting them to the web.
What is network DLP?
Network DLP monitors data in motion across your organization’s network. It identifies and blocks risky behavior—whether from insiders or external threats—before data can leave your environment. Forcepoint DLP offers deep visibility and control over data transfers, helping ensure compliance and reduce the risk of breaches.
What is cloud DLP?
Cloud DLP safeguards data stored in and moving through cloud services. Forcepoint DLP can augment and enhance platforms like Google Workspace and Microsoft 365.
Can Forcepoint DLP protect data on cloud applications like Google Workspace and Microsoft 365?
Absolutely. Forcepoint DLP can augment and enhance Google Workspace and Microsoft 365.
What are the key features and functionalities of DLP?
The key features and functionalities of DLP include:
- Data discovery across on-prem and cloud
- Data classification and labelling
- Advanced content inspection
- Predefined policies and templates for compliance
- Unified policy based enforcement for all channels
- Device control and endpoint protection
- Real-time monitoring and alerting
- Incident management and investigation
- Reporting, analytics and audit-ready compliance evidence
- Integration and deployment flexibility
What are the most common use cases for DLP?
Typical DLP use cases include preventing data breaches and accidental leaks, protecting intellectual property, and meeting regulatory compliance obligations. Common scenarios may include stopping unauthorized uploads of PII/PHI/PCI data, blocking exfiltration of source code and trade secrets and enforcing regional privacy rules like GDPR and CCPA using pre-built policy templates.
Modern deployments also focus heavily on cloud, hybrid work and GenAI. Common Forcepoint DLP use cases include securing data in Microsoft 365 and other SaaS apps, controlling data movement from unmanaged/BYOD devices, reducing insider risk by monitoring high-risk user behavior, and inspecting prompts and responses for generative AI tools. Together, these use cases map back to a single goal: keep sensitive data where it belongs without slowing users down.








