It’s Time to Take a New Path to SASE
0 min read

Jim Fulton
Part of our ongoing series about Zero Trust and SASE.
Chances are you’re reading this blog post from your laptop at home. Perhaps, you haven’t been in the office in weeks, if not months. Who knows when you’ll badge back into the lobby? And when you do, you’ll probably be sitting in one of those flexible, shared workspaces rather than a personal cubicle or office. That’s the reality of working from anywhere.
Much has been written (see here or here) about the security risks of working beyond what used to be called the corporate perimeter and how enterprises might adapt. Organizations have moved faster to cloud and SaaS apps than anyone would have expected a year ago, to the point that the journey to the cloud is no longer an issue of if, but when, and not of digital transformation, but of business transformation.
With people and data moving everywhere, security has to be agile to keep up. Now, the key issue facing many organizations is how to most effectively provide safe access to corporate resources on the web, in cloud apps and in internal, private apps anywhere, while keeping data safe everywhere.
SASE has rapidly become the headliner in IT investments for enabling the new distributed workforce. However, there’s a lot of confusion about where to start that’s made worse by vendors who are simply using the term “SASE” for re-badged point products. Of course, most SASE solutions are cloud-delivered. They also tend to be access-centric, that is, focused on controlling and protecting access to those corporate resources.
The whole point of access is to connect people to data so that they can use it to get their jobs done. A lot of vendors view that as the finish line. It’s not. To put it bluntly, securing access is just table stakes these days.
Enabling data to be used safely is ultimately what cybersecurity is all about. With people working anywhere, you can no longer rely upon old approaches such as trusting that their laptop or a device is attached to your ‘corporate’ network to have free reign with sensitive data. You have to control how that data is used—continuously requiring explicit permission every time somebody tries to access or move that data.
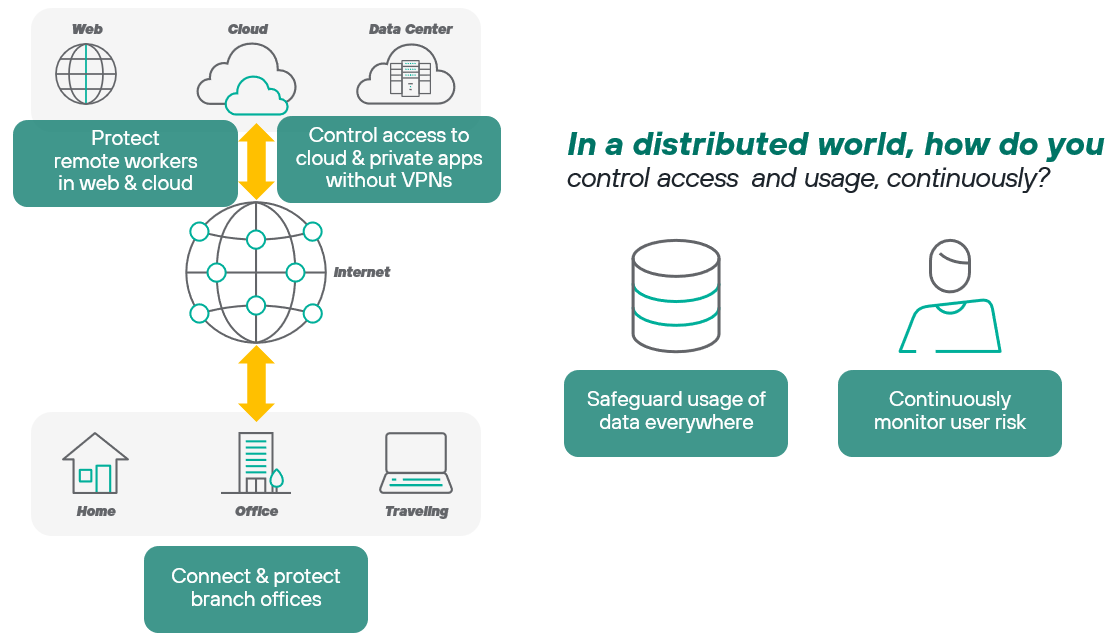 This ‘requiring explicit permission’ is the essence of Zero Trust. How do you apply Zero Trust? It turns out that SASE is answer. SASE brings together the wide range of capabilities for implementing Zero Trust into a converged, cloud-based platform that easier to deploy and manage than prior approaches.
This ‘requiring explicit permission’ is the essence of Zero Trust. How do you apply Zero Trust? It turns out that SASE is answer. SASE brings together the wide range of capabilities for implementing Zero Trust into a converged, cloud-based platform that easier to deploy and manage than prior approaches.
In our new whitepaper “5 Steps to SASE,” we can help organizations start on their path to what we’re calling a data-centric SASE architecture. It covers:
- How security teams and leaders can begin from different starting points to build out their converged SASE architecture, one cloud-delivered capability at a time.
- A definition of data-centric SASE and how protecting users and data is different from a SASE approach focused solely on access.
- The benefits and capabilities of data-centric SASE, which includes data protection, threat protection, application security and network security.
- We list the top 4 advantages that you should look for in a data-centric SASE platform.
We hope you find this paper useful to sorting out your priorities for protecting users and safeguarding critical information. Click the green Read the Whitepaper button to the right to download it.

Jim Fulton
Read more articles by Jim FultonJim Fulton serves as VP Product Marketing & Analyst Relations, focused on SASE, SSE and Zero Trust data security. He has been delivering enterprise access and security products for more than 20 years and holds a degree in Computer Science from MIT.
- 5 Steps to SASE - Your Executive's Guide
In the Article
- 5 Steps to SASE - Your Executive's GuideRead the Whitepaper
X-Labs
Get insight, analysis & news straight to your inbox

To the Point
Cybersecurity
A Podcast covering latest trends and topics in the world of cybersecurity
Listen Now