
12K+ customers couldn't be wrong










































Struggling To See Data in the Cloud?
You're not alone. With over 800,000 cloud applications on the market, legacy data security tools are overwhelmed by the complexities of SaaS policy management and AI-led data sprawl.
of organizations have experienced a
severe cloud security incident*
of corporate data is stored
in the cloud*
of enterprises lack visibility of
AI agent-accessible data***
See and Secure Data in SaaS and GenAI Apps With CASB
Forcepoint CASB secures access to the most popular SaaS applications in the world, like Microsoft 365, Google Workspace and Salesforce. The solution scans for sensitive data at rest within corporate-sanctioned applications and delivers true visibility and control over the data through an integration with Forcepoint Data Loss Prevention (DLP) software.

Forcepoint CASB Solution vs. the Competition
Forcepoint | Legacy Security Vendors | Legacy Networking Vendors | |
Cloud Access Security Broker (CASB) features
| |||
Data Security Features
|
DISCLAIMER: Product comparison is based off of in-product capabilities and cross-portfolio integrations available from the same vendor as of March 1st , 2023. Comparisons do not include integrations with third-party vendors. Feature comparison is based off of each vendor’s most recent and modern version available as of March 1st, 2023. Information is based off of data collected from public websites and forums, analyst papers, and product datasheets as of March 1st, 2023.
Critical CASB Capabilities to Keep Your SaaS Secure
Deep Visibility into SaaS Data
Gain full visibility into data across SaaS apps. Pre-built and customizable dashboards empower security, compliance, and audit teams to act fast with intuitive insights.
Protect Data and Simplify Compliance
Extend best-in-class DLP to CASB to prevent data loss in the cloud. Streamline policy configuration and compliance management with 1,700+ classifiers and policy templates.
Secure Access from Any Device
Empower hybrid workers with secure, zero trust access to SaaS applications from any device and location. Agentless deployment modes keep users productive and data protected.

Automate Threat Remediation
Automatically detect and respond to SaaS threats like malware, data overexposure, and policy violations in SaaS apps to minimize breach impact.
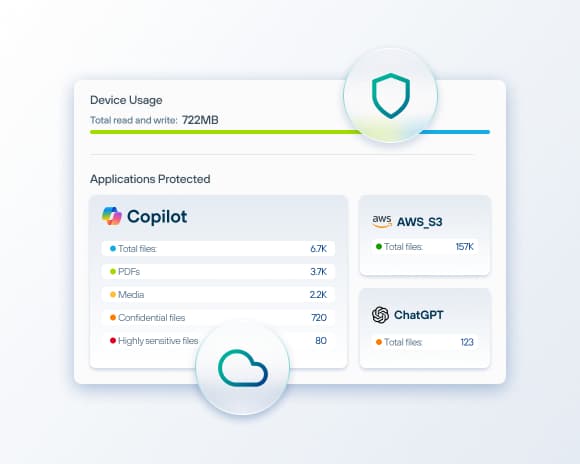
Secure Microsoft Copilot
with Forcepoint CASB
Prevent unintended data exposure and ensure safe AI adoption across Microsoft 365.
- Gain visibility and control over Copilot prompts, responses, and file attachments.
- Detect and classify sensitive data in AI interactions.
- Enable audit and remediation workflows for compliance and responsible AI use.

Closing the SaaS Security Gap: A Practical Guide for CISOs and CIOs
Overpermissioned files. Misplaced sensitive content. Documents owned by employees who left six months ago. Unmanaged AI tools like Copilot or ChatGPT absorbing corporate knowledge. These are the new frontiers of data risk. Discover the hidden SaaS data security risks in your organization and learn how to mitigate them in this comprehensive guide.
Why Customers Choose Forcepoint CASB Solution
Why Customers Choose Forcepoint CASB Solution
"Very good experience in getting visibility into and protection of cloud application, policy enforcement and user behavior."
Read the ReviewFrequently Asked Questions
How does Forcepoint CASB integrate with so many cloud applications?
Forcepoint CASB integrates with over 800,000 cloud applications using a combination of API-based, reverse proxy, and forward proxy methods. This hybrid approach allows us to monitor and secure data across virtually any SaaS, IaaS, or private cloud environment, regardless of how users access those apps.
- API-based: Best for deep visibility into sanctioned apps like Microsoft 365, Salesforce, or Google Workspace. It allows us to audit user activity, detect threats, and enforce DLP policies—even retroactively.
- Reverse Proxy: Ideal for inline protection of cloud traffic from managed devices. It enables real-time session control, such as blocking downloads or applying step-up authentication.
- Forward Proxy: Useful when securing unmanaged devices or BYOD scenarios. It routes outbound traffic to cloud services through Forcepoint’s proxy, allowing policy enforcement before the data even reaches the app.
What is a Cloud Access Security Broker (CASB) solution?
A Cloud Access Security Broker (CASB) is a security solution that acts as an intermediary between cloud users and cloud providers. It protects organizations from cyberattacks by preventing malware and securing data through encryption, making data streams unreadable to unauthorized parties. CASBs provide data security and access management for SaaS applications, ensuring safe and compliant cloud usage.
How does a CASB work and function?
CASB software secures data flowing between in-house IT architectures and cloud vendor environments by enforcing an organization's security policies. It governs user interactions with cloud applications and the data within them, ensuring secure and compliant access to cloud resources.
What is the purpose of a CASB?
The primary purpose of a CASB is to secure data in both managed and unmanaged cloud applications. It allows organizations to create policies that govern data usage, mitigating risks such as data exfiltration and leakage. CASBs also address the challenge of shadow IT by identifying and managing unauthorized SaaS applications.
How does a CASB enhance cloud security?
A CASB enhances cloud security by providing visibility into cloud application usage, enforcing data security policies, and protecting against threats. It monitors user activity, detects anomalies, and ensures compliance with regulatory standards. By acting as a security checkpoint between users and cloud services, a CASB helps prevent data breaches and unauthorized access.
How do CASBs help with regulatory compliance?
CASBs help with regulatory compliance by monitoring cloud usage and enforcing policies that align with industry regulations such as GDPR, HIPAA, SOX, and PCI DSS. They provide detailed reports and audits to demonstrate compliance, helping organizations avoid fines and legal issues. CASBs also ensure that data is stored and processed in accordance with regional data protection laws.
How do CASBs address the challenge of shadow IT?
CASBs address the challenge of shadow IT by discovering and monitoring unauthorized cloud applications used within an organization. They provide visibility into all cloud services, assess their risk levels and enforce security policies to manage and control their usage. This helps organizations mitigate the risks associated with unapproved cloud applications.
Why is CASB important for organizations using SaaS applications?
CASBs are crucial for organizations using SaaS applications because they provide comprehensive security and compliance management. They help organizations gain control over data in the cloud, protect against cyber threats, and ensure that cloud usage complies with regulatory requirements. CASBs also address the challenges of shadow IT by identifying and managing unauthorized cloud applications.
What are the pillars of an effective CASB?
Visibility: Enterprises need visibility into cloud app usage, including user accounts, departments, locations, and devices, to ensure information assets are controlled and compliant with governance processes.
Data Security: CASBs enhance Data Loss Prevention (DLP) by monitoring cloud file storage and preventing unauthorized data sharing, which traditional DLP products may miss.
Threat Protection: CASBs detect suspicious insider behavior and mitigate risks from former employees who may still access cloud apps containing sensitive information.
Compliance: CASBs help organizations comply with regional regulations like SOX, HIPAA, PCI DSS, NIST, CJIS, MAS, and ISO 27001, ensuring data privacy and security.
BYOD, Shadow IT, and Increased Cloud Usage: CASBs enforce granular access policies for managed and unmanaged devices, addressing challenges posed by BYOD policies, SaaS apps, and shadow IT.
What are the key features of a CASB solution?
Key features of a CASB solution include:
Visibility: Monitoring and reporting on cloud application usage.
Data Security: Encrypting data and enforcing Data Loss Prevention (DLP) policies.
Threat Protection: Detecting and mitigating cloud-based threats.
Compliance: Ensuring adherence to industry regulations and standards.
Access Control: Managing user access to cloud applications and data.
What are the benefits of a CASB solution?
CASBs improve data security for companies using popular SaaS applications like Microsoft 365, Workspace, and Salesforce. Key benefits include:
Enhanced visibility and control over data in SaaS apps.
Protection against cloud-based threats.
Secure access to numerous SaaS apps.
Improved compliance with industry-specific and global data privacy regulations.
How do you calculate the cost savings of a CASB?
A Deploying a CASB solution can reduce operational costs through:
Efficient management: Enforcing security policies for all cloud services from a single platform reduces the need for extensive security teams.
Increased agility: Secure cloud adoption enhances productivity, accelerates business application delivery, streamlines M&A activities, and reduces technical debt.
Greater automation: Automated discovery, categorization, policy enforcement, and remediation minimize the resources needed for cloud security management.
Elimination of redundant cloud applications: Identifying and removing unnecessary cloud apps reduces overall cloud service costs.
Improved utilization efficiency: Comprehensive cloud service inventories help IT teams optimize spending and reduce underutilization.
How is CASB different from DLP?
CASBs combine various technologies to secure cloud applications and data, acting as a firewall, filter and proxy between users and cloud services. They perform functions such as discovering cloud applications, evaluating risks and enforcing security policies. CASBs use gateways, log data, endpoint agents and APIs to monitor and analyze cloud activity.
DLP solutions employ various technologies to monitor data flowing through an IT environment, detect potential leaks or misuse and block user actions to safeguard data.
What are the benefits of integrating CASB with DLP?
A Integrating CASB with DLP offers several advantages:
Better coverage: Comprehensive DLP coverage in the cloud.
Stronger protection: Enhanced data security during cloud migration.
Unified policies: Leveraging existing DLP policies for both cloud and on-premises infrastructure.
Deeper insight: Greater visibility into user behavior and data usage in the cloud.
* Snyk
** Exploding Topics
*** SailPoint



