Five Takeaways to Build a Resilient Cybersecurity Strategy

Since the pandemic began, government agencies have been working diligently to enable productive and secure remote access for their employees. With workers connecting from more places and devices than ever before, the baseline for security has changed dramatically. Forcepoint’s recent Government at th Edge Summit brought together government and industry leaders to discuss what works to ensure resiliency in the coronavirus era.
Government at the Edge Summit Sessions
With people as the new perimeter, cross domain solutions provide remote classified access, while Zero Trust helps ensure security. But resiliency relies on more than technology. Monitoring must include the human touch as well—from being transparent about what’s being done in the name of protection to having someone oversee what access users are granted and why. Here are some key takeaways from the summit.
1. Enable remote classified access
One of the biggest challenges with regard to resiliency for government agencies has been ensuring employees can do classified work in a remote environment. The cloud, which many agencies were already moving to for cost savings, underpins this capability. More specifically, cross domain solutions permit communication between networks and classification levels that would otherwise be kept separate.
At the summit, Maj. Joe Brendler, who spent just under 32 years on active duty in the Army, talked about his experience with cross domain solutions. He cited the Army’s Seventh Signal Command, which was using a combination of Trusted Thin Client and Commercial Solutions for Classified (CSfC) to rewire its campus before COVID-19 and was able to leverage those same technologies to support a suddenly remote workforce.
Cross domain solutions and Trusted Thin Clients take the complexity out of IT by reducing it to a single network connection that allows the user to connect to the cloud at different classification levels. This simplicity is crucial to resiliency. As the cloud becomes more available, especially at the classified level, more cloud providers are going to be offering desktop-as-a-service in the future, too.
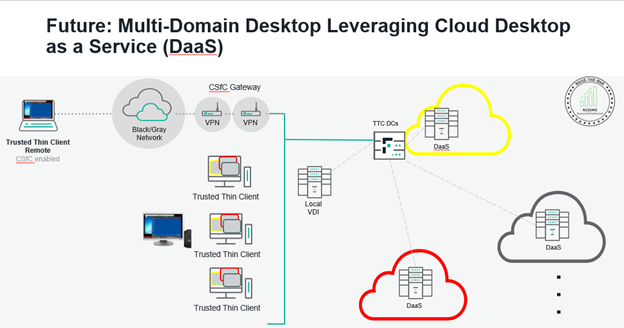
2. Understand the role of Zero Trust in resiliency
The transition to the cloud has shifted how agencies think about security too, which includes a growing emphasis on Zero Trust architecture. In the “Blueprint for Zero Trust in a Remote World” panel Steve Hernandez, CIO of the Department of Education, noted that, before COVID, most agencies were relying on a traditional approach to defense: gates, guns, and guards. The cloud disrupted that model first, and COVID then pushed even more employees and data outside the perimeter. As a result, a Zero Trust model has become non-negotiable.
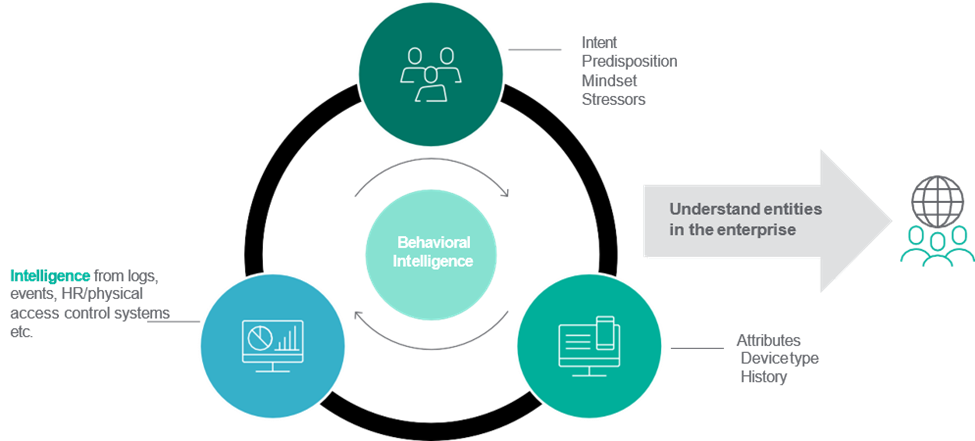
In a nutshell, a Zero Trust model requires every user to be authenticated before gaining access to applications and data. That authentication should take place on an ongoing basis via behavioral analytics. Agencies can leverage existing technology, like SD-WAN, for Zero Trust, Hernandez added. At the heart of it all, though, is data—understanding what you need to protect.
Insights from artificial and behavioral intelligence are key to that protection. In the panel, Myrna Soto, Chief Strategy and Trust Officer at Forcepoint, suggested agencies need these technologies in order to assess risk and have adaptive policies. There is simply too much data and not enough humans to do it any other way. Brandon Wales, Executive Director of the Cybersecurity and Infrastructure Security Agency at the Department of Homeland Security, added that NIST’s 800-207 is a great place to start for agencies new to the game.
3. People are the new perimeter
In rolling out new technology, people and processes cannot be overlooked. With employees connecting from more devices and places than ever, people are the new perimeter—which means cyber resiliency must consider human factors.
At the summit, Dr. John Zangardi, President of Redhorse Corporation and former CIO of DHS, said that agencies tend to become focused on cost-schedule-performance when they’re trying to bring new capabilities online. This often causes them to lose sight of the human factors and the importance of constraints or boundaries that ensure appropriate behavior on the part of employees.
This sentiment was echoed by Dr. Margaret Cunningham, Principal Research Scientist for Human Behavior within Forcepoint X-Labs, the world’s first dedicated research division that combines deep security expertise with behavioral science research. “Organizational climate factors really start to determine how oversight and accountability work,” she added.
4. Managed privileged user access and sprawl
Privileged users in particular need to be kept in check in order to secure this new “perimeter.” But according to a recent survey from Forcepoint and the Ponemon Institute, privileged access is in fact widespread—hardly a privilege at all. As such, insider threats can be expected. This points us back to continuous monitoring; only by having a baseline of normal data can you tell how risky a specific user’s actions are.
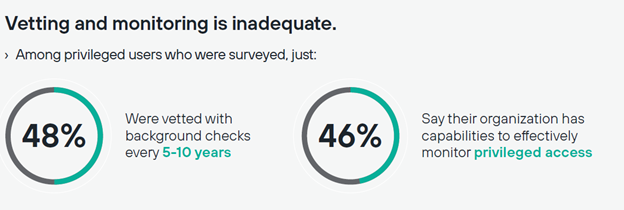
Jared Quance, Insider Threat Program Manager at the U.S. Coast Guard, said on the panel:
“If I can’t recreate who they were for the past five years, what their tasks were for the last five years, then I’m really not going to be able to resolve whether or not they have had some sort of chronic growing bad behavior,”
Agencies must make sure stopgaps are in place to ensure privileged users—or even those who just have shared folder accesses—have their rights and privileges adjusted when their roles change.
And while privileged user access is a technology problem, Quance added, there must be someone who owns it. “You should have a person specifically dedicated to nothing more than 9-to-5 management of privileged users,” he said.
5. Be transparent
User access management, identity access management, and Zero Trust architecture all represent protection for both the agency and its people. Increasingly, it’s almost inevitable that a bad actor will be able to get inside. Still, this monitoring must be communicated properly and consistently to employees so they don’t feel like their employer is spying on them. Monitoring isn’t surveillance, Forcepoint’s CEO Matt Moynahan explained during the summit. It’s protection.
“You hear this term coming up in the media called surveillance capitalism, and I’ll oftentimes get in a back and forth with a reporter or an analyst. I’ll say let’s play a word association game: how do you feel about surveillance? And everybody thinks of a government agent. How do you feel about monitoring? And everybody thinks of big brother. But you say how do you feel about protection? And they say, Oh I feel great about that!”
At the end of the day, resiliency means considering not just the technology that will ensure connectivity and keep data safe, but also the human factors that can impact the agency’s overall security posture. With people as the new perimeter, cross domain solutions are crucial to permitting remote classified access, while Zero Trust will ensure security. But monitoring must include the human touch as well—from being transparent about what’s being done in the name of protection to having someone oversee what access users are granted and why.
