Accelerate Zero Trust: Securing Cloud Applications for the Modern Workforce
0 min read

Tuan Nguyen
Today, as we continue our Accelerate Zero Trust series, let’s look at securing cloud apps for the modern distributed workforce. The shift to remote and hybrid work models has reshaped access and security needs for many organizations. Employees now expect remote sign-ins for business apps and corporate databases, driving the surge in cloud-based apps and data adoption. Collaboration tools like Microsoft 365, Google Workspace, Slack, Salesforce, and Jira facilitate global data access and real-time peer collaboration.
But as organizations adopt cloud services and remote and hybrid work becomes the norm, new concerns arise regarding visibility and control into employees accessing and using sensitive company data. For example, when employees use their personal devices (BYOD) or unmanaged devices to access cloud resources, it becomes a challenge for IT and InfoSec teams to control and have visibility into their actions. Additionally, using unsanctioned cloud applications for work (called Shadow IT) further complicates enforcing consistent company security policies for everyone.
A CASB solution gives organizations control over cloud apps, user access, and the data stored in those apps. It provides visibility and control over sanctioned and unsanctioned cloud apps and the devices being used, helping organizations to prevent data loss and enforce granular access controls.
Visibility and Control
A key component of a CASB solution lies in its ability to provide unparalleled visibility and control over cloud applications. Organizations need to know who is accessing what data, when, and from where.
The ability to control access to various cloud applications and to discriminate between appropriate use of a given application and inappropriate use (whether malicious or accidental) is crucial for an organization.
A CASB solution integrates with many of the most popular business applications in the cloud via APIs, but having unparalleled visibility and control means it should also be able to connect with the full range of custom cloud apps and services that an organization will have as well. To do so efficiently, a CASB solution can enable inline control via reverse and forward proxies, and a comprehensive offering will utilize a combination of proxies and APIs to provide real-time control and visibility for organizations.
As mentioned previously, BYOD or unmanaged devices can introduce complexity and challenges for IT teams requiring visibility into these devices. However, a CASB solution with agentless capabilities can effectively extend control over all devices ensuring secure access for employees everywhere.
Watch to learn more about how Forcepoint ONE CASB is a multi-mode CASB solution:
Shine a Light on Shadow IT
The rise of Shadow IT—a term used to describe unsanctioned apps and tools used by employees—poses a significant challenge to security.
Such behavior often happens when employees are dissatisfied with their existing tools and attempt to boost their productivity through unsupported means. Losing visibility and control of data in this way can lead to extensive data exfiltration and ultimately to reputational and financial losses.
It may seem that simply blocking an unsanctioned app may seem like the safest option, but this can encourage users to search for alternative Shadow IT solutions. A friendlier approach available with some CASBs is having the option to prompt users in real time that they are attempting to access an unsanctioned app and offer a sanctioned alternative educating employees and promoting education and awareness, good cybersecurity hygiene, and reenforcing best practices.
CASB solutions provide insights into app usage and enforce consistent security policies across the workforce, so organizations can regain control over the digital environment, mitigating risks associated with unapproved software, and providing strong IT governance for security administrators.
Maintaining Productivity
One concern with adopting a new security solution can be performance degradation. Performance is of vital importance because when deployed, CASBs connect workers to business applications workers rely on daily. A CASB solution needs to be scalable with low latency and provide high availability, with very minimal latency added when enabling company DLP policies and malware scanning.
A distributed global cloud infrastructure is key for optimal performance. Employees require secure and fast access to cloud resources wherever they are in the world without facing unnecessary bottlenecks. Distributed enforcement pushes policies across the cloud and to the edge for high-performance use for organizations.
Issues with performance can lead employees to seek out risky workarounds (shadow IT, as discussed previously) in order to maintain productivity. A modern CASB solution can offer safer, more efficient Zero Trust access to business-critical apps and data without sacrificing performance—no matter where people are and what device they use.
Understanding the Data
Effective security strategies are built on data-driven decisions. Comprehensive reporting capabilities are particularly important and useful for the management of remote and hybrid workers. A CASB solution can provide clear and easy-to-understand data to help security managers understand risk and prioritize efforts for informed decision making across the business.
This helps to elevate the role of security within an organization where admins can effectively communicate how data risk is monitored and mitigated and can demonstrate the value of a strong security posture to other lines of business.
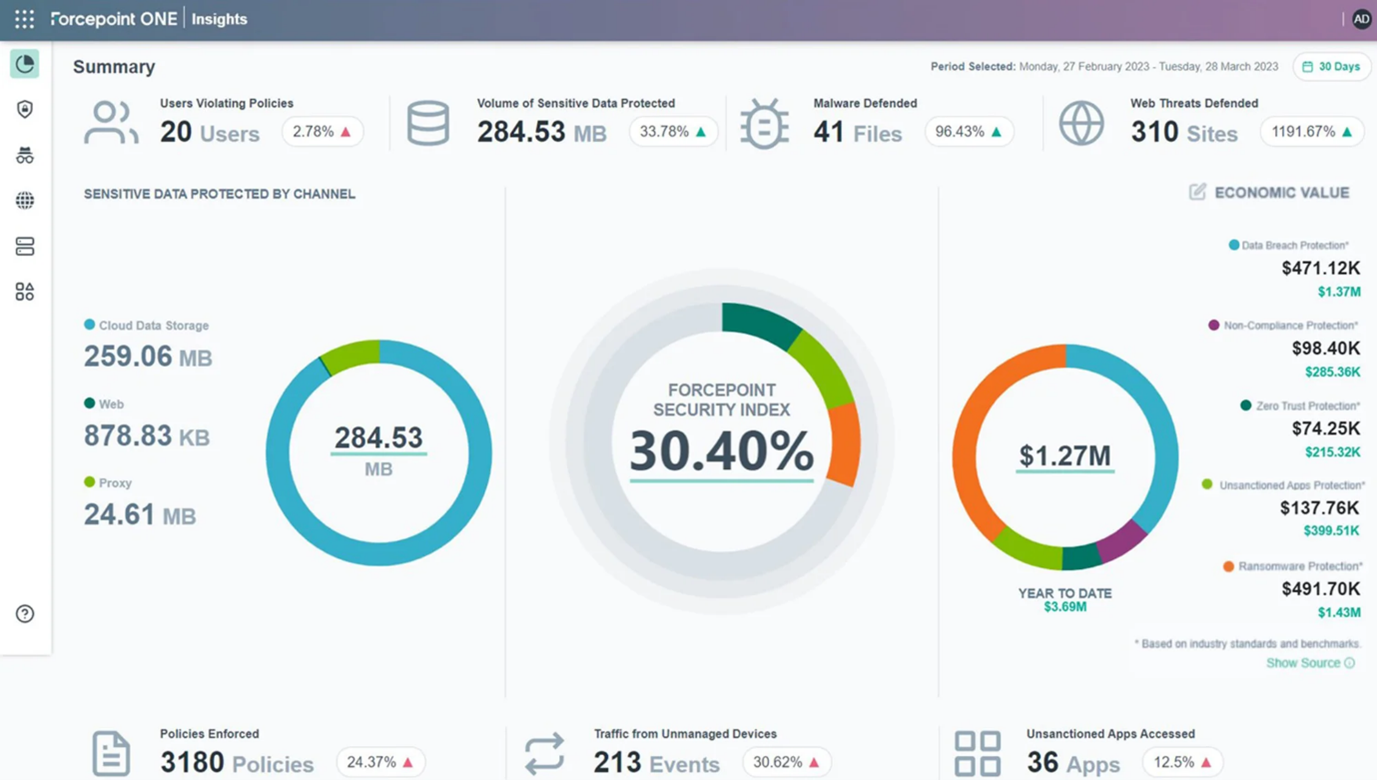
These insights often include custom dashboards that aggregate and highlight top sensitive data file downloaders and uploaders, top sensitive data match patterns triggered on upload or download, and top malware infected file downloaders and uploaders. The ability to quickly have a high-level view of an organization's cloud ecosystem and being able to drill in for more detailed reports is essential to understand the impact of a security solution.
Easy SIEM integration and exportable logs also help extend visibility to other areas of organizations. The overall result should shed light on which groups and departments are accessing which apps regularly, also highlighting exposure of sensitive data across these apps. This picture will help in fine-tuning controls over which users have access to which apps and data categories.
Understanding the data through clear reporting is critical to get a complete picture of the business cloud ecosystem and its users.
Security Simplified
For effective security management, a Cloud Access Security Broker (CASB) remains crucial. It links users with apps and enforces consistent security controls across the cloud ecosystem. A robust CASB solution ensures IT gains deep insight and meticulous control over sensitive data, all while preserving the swift and convenient access users rely on.
Forcepoint ONE is a Data-first SASE platform that simplifies security management, reduces risks of cyber-attacks, and provides users with frictionless secure access not only for cloud applications, but across the web, and on private applications as well. This all-in-one platform offers a complete solution that includes CASB, SWG, ZTNA, and DLP for a holistic approach to security.
Forcepoint is recognized as an industry leader in Data Security, providing customers comprehensive solutions to protect business critical data from internal and external threats. We are proud to have a strong focus on innovation and delivering to customers the best of breed security solutions to address the evolving threat landscape.
Request a quick demo and learn more about how Forcepoint ONE CASB can simplify securing cloud applications and accelerate the journey to Zero Trust.
Next week on ‘Accelerate Zero Trust’ series
Thanks for continuing with us on our Accelerate Zero Trust blog series. Stay tuned next week, when we'll explore another Forcepoint product and how it all works together to help you accelerate your Zero Trust journey.
In case you’ve missed our previous installments, take a moment to explore our earlier blogs in the series covering Zero Trust Data Security, Secure SD-WAN, and Secure Web Gateway.
Related Resources

Tuan Nguyen
Read more articles by Tuan NguyenTuan Nguyen serves as Product Marketing Manager at Forcepoint with a focus on web and cloud security solutions for SASE applications. With over 10 years of industry experience in cloud security, data center networking, and web development across both large enterprise companies and start-ups. He is passionate about bringing enterprise solutions to market and shaping a more secure digital landscape for organizations.
 Secure Your Cloud with Confidence: The CASB Buyer’s Guide Read the Whitepaper
Secure Your Cloud with Confidence: The CASB Buyer’s Guide Read the Whitepaper
X-Labs
Get insight, analysis & news straight to your inbox

To the Point
Cybersecurity
A Podcast covering latest trends and topics in the world of cybersecurity
Listen Now









