Forcepoint X-Labs
Pioneering integrated behavior and threat-intelligence innovations
Meet the industry’s only lab that combines cybersecurity researchers, human behavior researchers, data scientists, and counter-intelligence specialists.
We drive proactive - not reactive - protection by understanding human and machine behavior and the movement of critical data.
We are researchers with expertise in cognitive science, physics, engineering, big data, artificial intelligence, and security research. Our backgrounds vary from national government and research labs to some of the top technology organizations in the world.
Focus areas
Human behavior
Applying insights from behavioral intelligence to cybersecurity
Threat and behavior intelligence research
Applying up-to-date threat and behavior intelligence for stronger cyber protection solutions
AI and data science
Leveraging machine learning and analytics for behavioral understanding
Game-changing approaches
Building on traditional threat intelligence by adding the power of behavioral intelligence insights
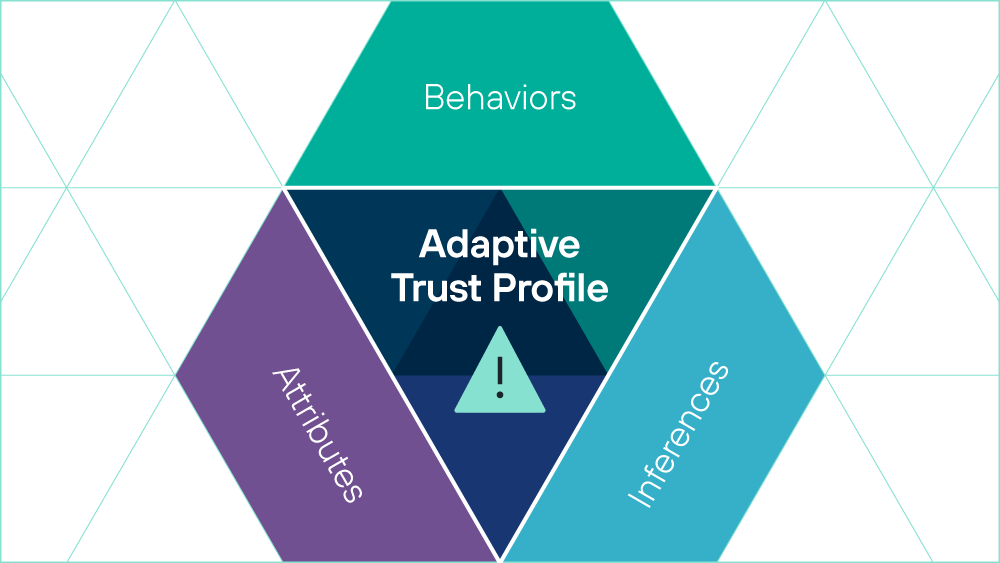
Adaptive Trust Profile
The Adaptive Trust Profile™ (ATP) is a core building block of Forcepoint’s Converged Security Platform. More than a technology, the ATP is a collection of attributes, models and inferences about entities which derives, through applied artificial intelligence and analytics, a set of risks for each entity. The ATP allows security professionals to focus on those entities which truly pose the highest level of risk to the business and employees. With this approach, we allow customers to escape the reactive and binary, event-based approaches to drive risk adaptive protection.
Behavior and Threat Intelligence
Behavioral and threat intelligence insights enable products in the Forcepoint portfolio to continuously improve their ability to provide dynamic, adaptive protection of your data, people, and machines.
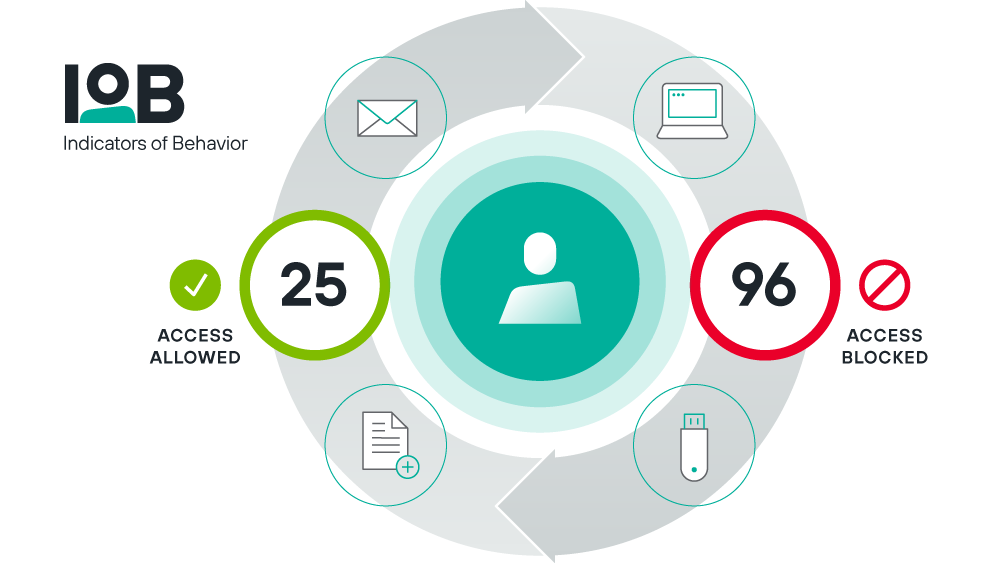
Indicators of Behavior
Indicators of Behavior (IOBs) are analytics that assess the risk of users and devices in real-time. IOBs help you understand how employees, contractors and accounts behave and automatically identify high-risk interactions that could indicate a malicious insider or compromised account. This enables us to observe and prioritize risk—as events occur—to move left of loss without getting in the way of productivity.
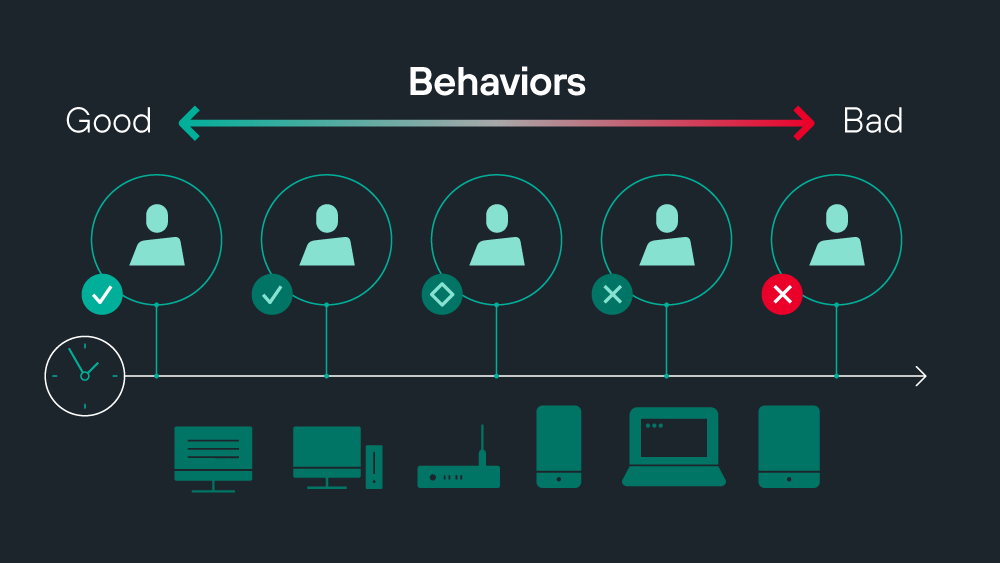
Cyber Behavior Catalog
The Cyber Behavior Catalog™ allows us to map observations made over many different data sources and times to actual human and machine behaviors. These behaviors are the building blocks of the behavior models that help populate and leverage the Adaptive Trust Profile.