12K+ customers couldn't be wrong










































Uncover Insider Risk at the Earliest Point of Detection
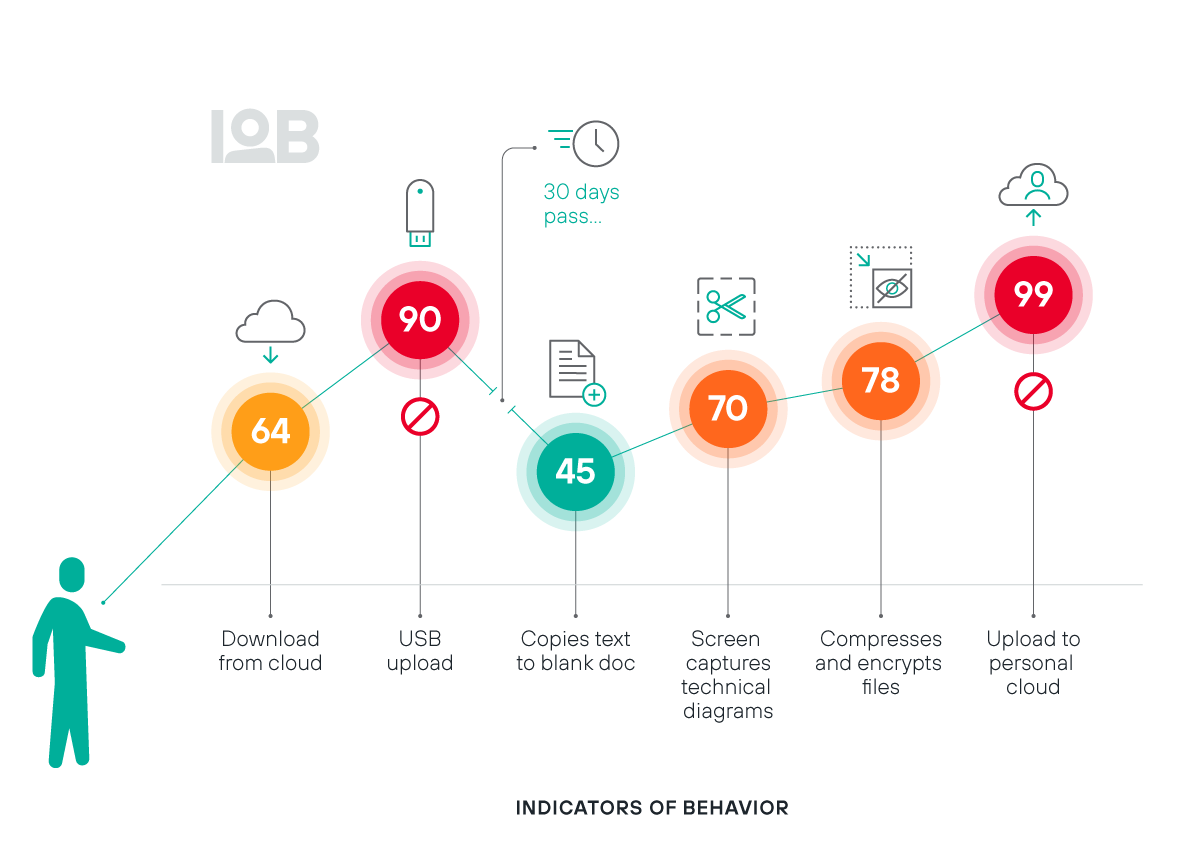
Gain meaningful visibility into user interactions with critical data
Eliminate dangerous blind spots and power a complete view of when users are trending towards risky behavior
Understand user behaviors and intent with always up-to-date risk scoring
Unlock broad monitoring capabilities across 100+ Indicators of Behaviors (IOBs)
DATASHEET
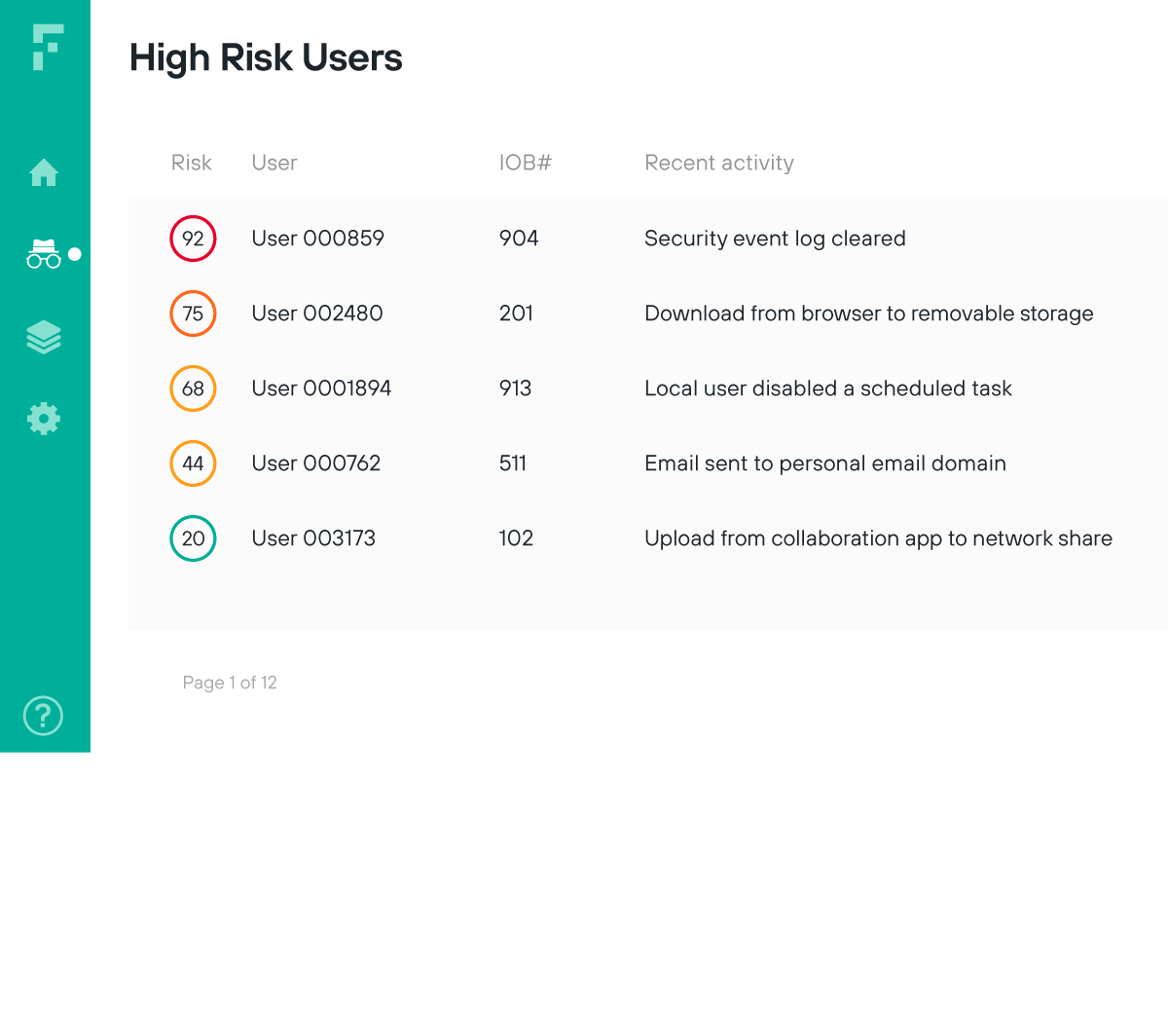
Implement a Zero Trust model with continuous user validation
Surface risk from sanctioned users and alert analysts to unusual behaviors at the earliest point of detection for a truly Zero Trust approach to security
Limit access based on unusual user activities that could indicate compromise
Validate user risk through real-time monitoring of ongoing user and data interaction
INFOGRAPHIC
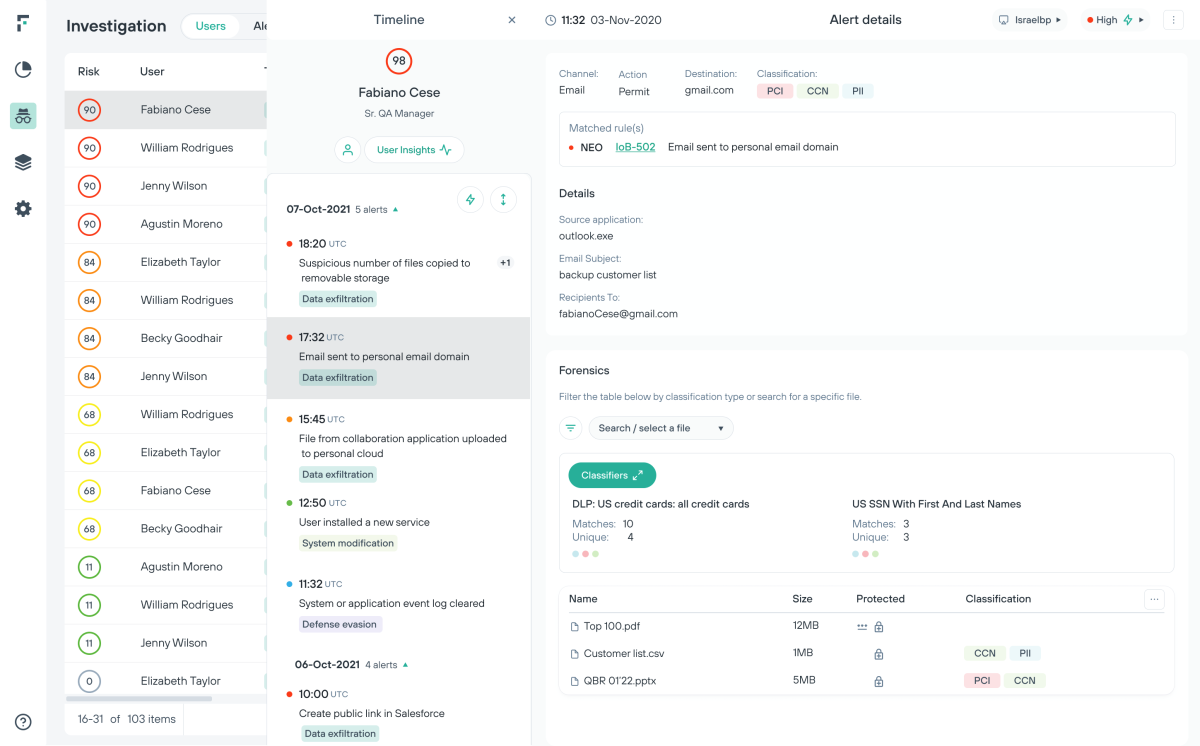
Maximize security analyst efficiency and reduce alert fatigue
Risk-Adaptive Protection shifts organizations from an event-centric to a risk-centric approach to data security.
Get ahead of the exfiltration event through orchestration of policy adjustments at the user level
Gain investigation efficiency and increase learn capacity
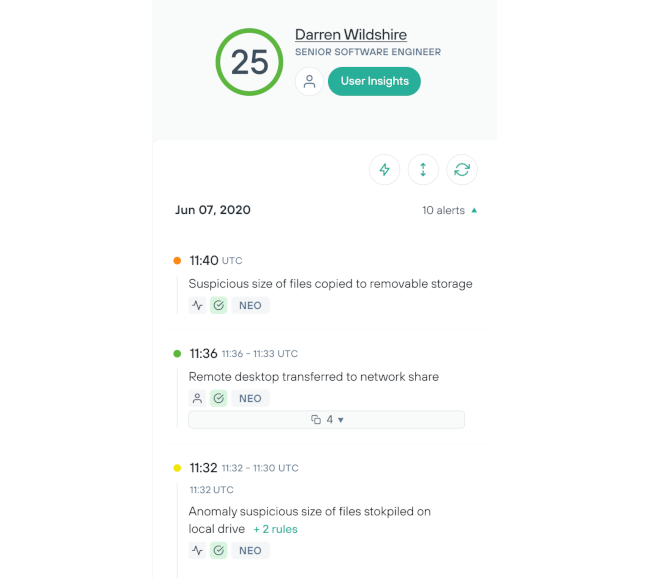
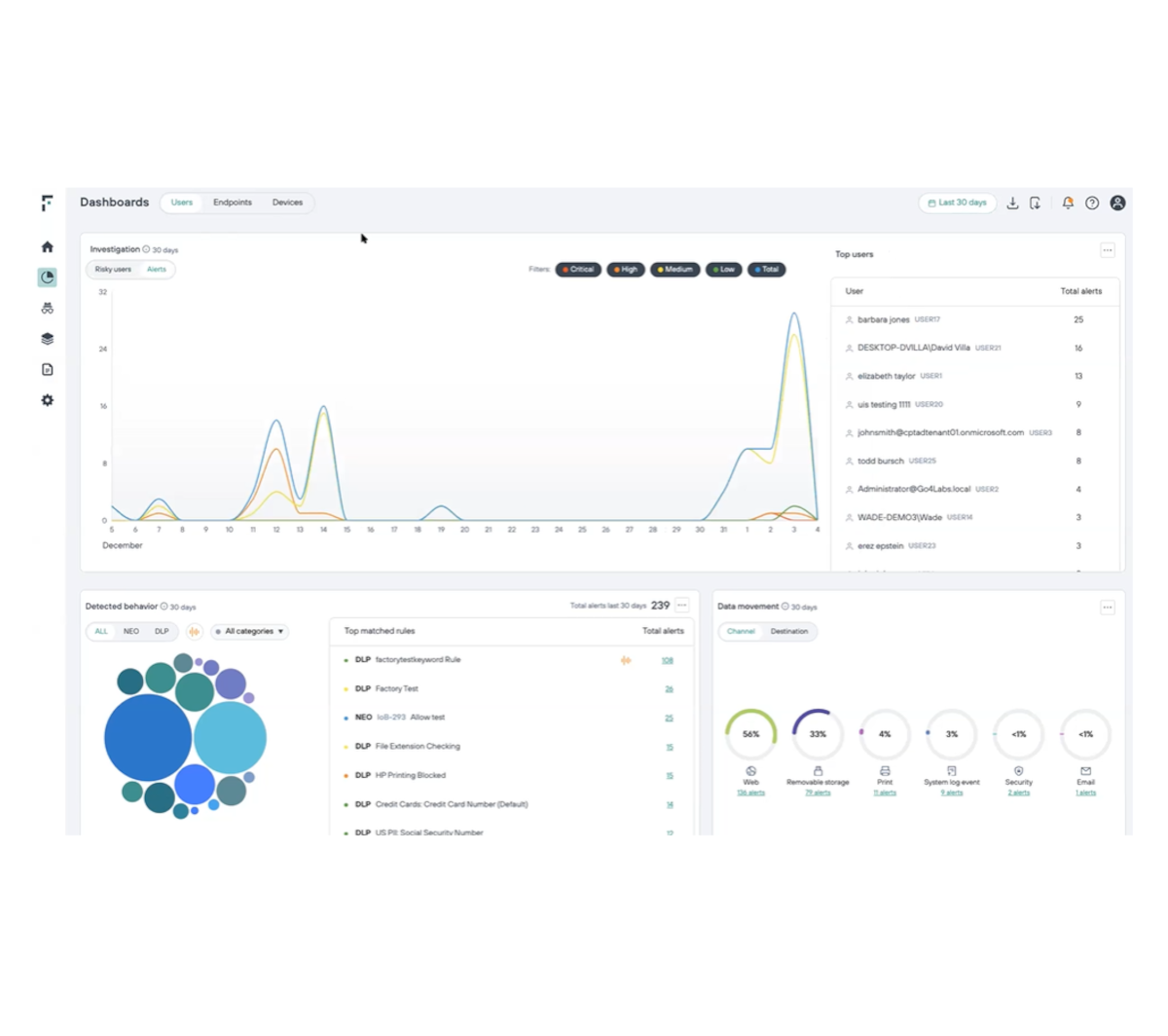
Investigate risk from insiders with efficiency and ease
Reduce the need for manual touchpoints through a frictionless implementation process and personalized automation.
Increase analyst capacity to investigate users through automation and the elimination of false-positives
Free up your staff through an easily maintained infrastructure in the cloud and a 30-second agent deployment
Respond to emerging threats in real time
Prevent data exfiltration by automatically adapting your security policies to block risky user behavior.
Reduce false positive alerts and get back time spent on incident analysis
Allow low-risk users to access the information they need while keeping potential threats at bay
Automate data security in real time through ongoing monitoring of user activity


The Practical Executive's Guide to Data Loss Prevention
Discover the eight tried-and-true steps to implementing Data Loss Prevention (DLP) software for any size enterprise with our hands-on guide.
Analyst recommended.
User approved.
Forcepoint is consistently ranked among the top Data Loss Prevention software and data security software providers by users and industry analysts.
Forcepoint has been named a Leader in the IDC MarketScape: Worldwide DLP 2025 Vendor Assessment.
Forcepoint named the 2024 Global DLP Company of the Year for the second consecutive year by Frost & Sullivan.
Forcepoint recognized as a Strong Performer in The Forrester Wave™: Data Security Platforms, Q1 2025.
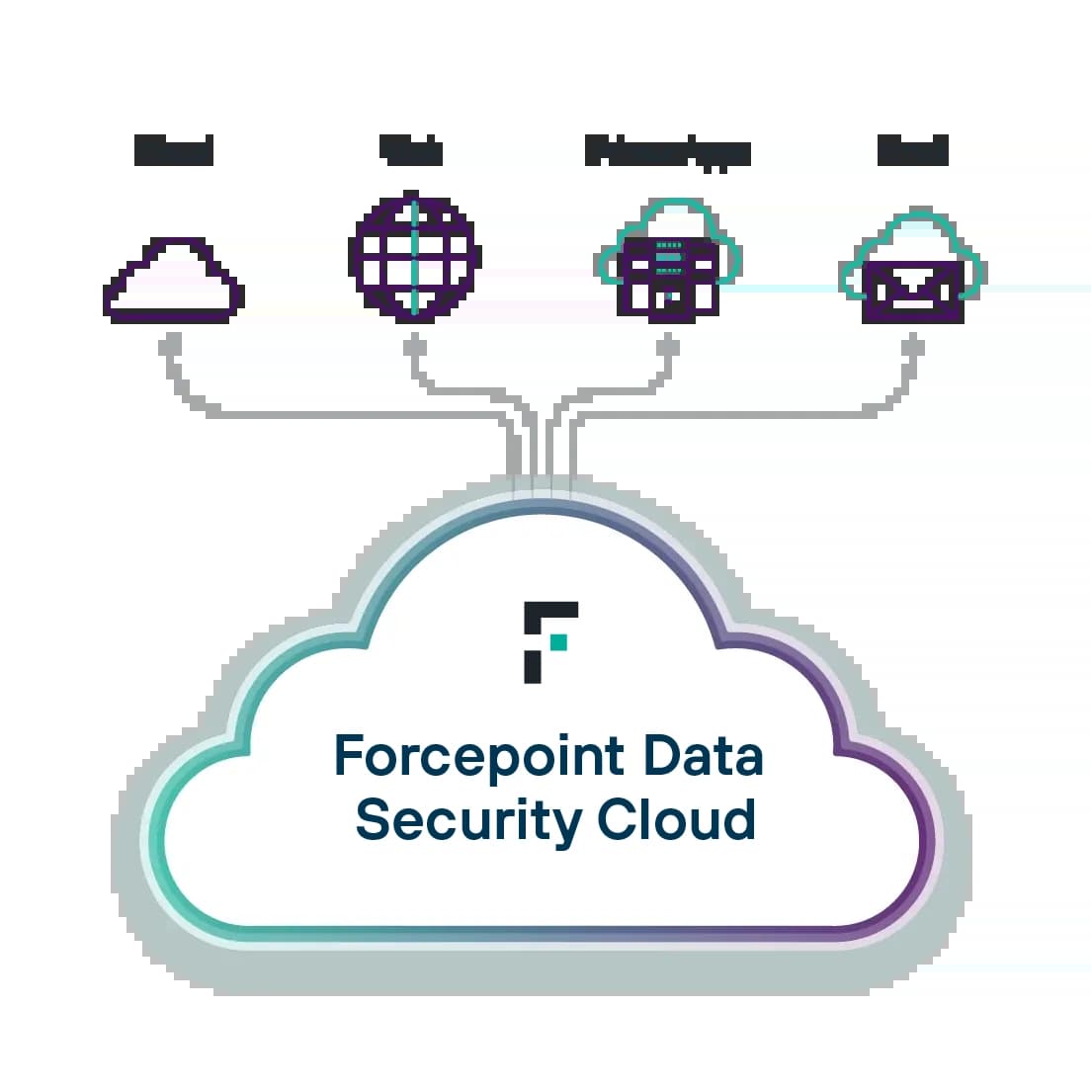
The Next Generation of Data Security
Secure data everywhere with Forcepoint. Prevent breaches and simplify compliance by using AI to power data discovery and classification, unifying policy management and adapting to risk in real time.
Enterprise DLP: Set, scale and automate data protection policies from a centralized, easy-to-use platform.
Forcepoint DSPM: Discover, classify and orchestrate with AI-powered automation.
Data Classification: Develop greater accuracy and efficiency in classifying data with the help of AI and ML.
RISK ADAPTIVE PROTECTION RESOURCES
Read About Risk Adaptive Protection Best Practices

Data Security Everywhere - Automate Data Security Management with Risk-Adaptive Protection
Watch the VideoCompetitive DLP Risk-Adaptive Protection Feature Comparison
View the DatasheetRisk-Adaptive Protection: Personalized Automation Solution for Forcepoint DLP
Read the Solution Brief

